June 7, 2023 • 10 min read
Strengthening the Three Lines Through Data-Driven, Collaborative, Continuous Assurance


David Malcom & Joe Gonski
Like so many internal audit teams, we are always looking for ways to optimize our processes, new methods to introduce efficiencies, and modernization opportunities to enhance our work.
One example of a current advancement is moving to a more quantifiable risk assessment approach through developing solutions that provide real-time monitoring of risks and control metrics across multiple areas within the organization. Additionally, at Northern Trust, we are introducing a data-driven, collaborative approach to auditing, enabling us to complement (and in some cases replace) our point-in-time testing with continuous assurance. This change will help us to re-envision the role of internal audit in our company as we continue to look for chances to become a trusted advisor to the organization, share data across the three lines, and create efficiencies through collaboration.
In this article, we’ll share some benefits that can be obtained with continuous assurance, our thoughtful approach to collaboration that ensured our ability to not compromise our independence, and an example of how continuous assurance can be utilized in a company to enhance your control testing capabilities.
Choosing Your Targets for Continuous Assurance
Continuous assurance combines data from multiple sources, leverages automation to highlight potential high-risk anomalies within the data, and facilitates more informed decision-making. With continuous assurance, auditors address risk and control deficiencies in near real-time instead of performing point-in-time assessments that consist of reviewing past activities. This approach enables the first and second lines to address control deficiencies before the impact spreads across the organization.
In our experience, we initially defined criteria to help identify good candidates for continuous assurance and — based on the level of effort required to implement — those that represented “quick wins” for the organization. Utilizing our criteria, we target highly repetitive, frequently tested, manual processes that produce structured data and require little auditor judgment in assessing the outputs. When we apply continuous assurance to processes that meet these criteria, we develop the ability to identify potential risks throughout the year and reduce human error that may occur as part of manual control testing.
Establishing Collaboration Without Impairing Independence
Collaboration across the three lines initially makes many internal auditors nervous for one reason – independence. Independence does not mean we cannot collaborate with the business. In fact, Standard 2050 in the IPPF has clear guidance that the CAE should collaborate with other internal assurance providers so the internal audit team can leverage their work and ensure adequate coverage.
We all have the same objective, which is to identify, mitigate, and manage risk to the organization. To maintain independence, the teams across the three lines should agree to rules of engagement, define roles and responsibilities, and ensure it is clearly understood that audit’s role is not to implement or execute any first- or second-line controls as part of continuous assurance.
To optimize the organization’s risk management capabilities, an important step is for the three lines to try to agree on a common risk taxonomy and risk definitions, which leads to the use of consistent language in organizational communications. This results in stakeholders’ ability to understand the criticality of risks and deficiencies identified, regardless of the team that reports them.
Depending on the maturity of the organization’s risk function, the internal audit team may identify areas where they can rely on testing performed by the first or second line. By relying on the testing capabilities of the first or second lines, internal audit is able to expand their coverage and focus on other emerging areas of risk within the organization. As these areas of emerging risk are typically new to auditors, this helps increase auditors’ interest and engagement as they are provided with the opportunity to develop additional skills and competencies.
Continuous Assurance in Action: Access Management as a Use Case
In most organizations, access management is a great target for continuous assurance because it meets virtually all of the criteria utilized to evaluate potential opportunities. As each of the three lines plays a role in the management and monitoring of user access, each would be interested in data related to user access management even with differing use cases.
We built a dynamic business intelligence (BI) reporting solution that allows auditors to review the organization’s management of risk related to user access management at any point in time. The solution consumes data from applications, including user login dates and the entitlements that users possess access to, as well as data from Human Resources on hirings, terminations, and job movements.
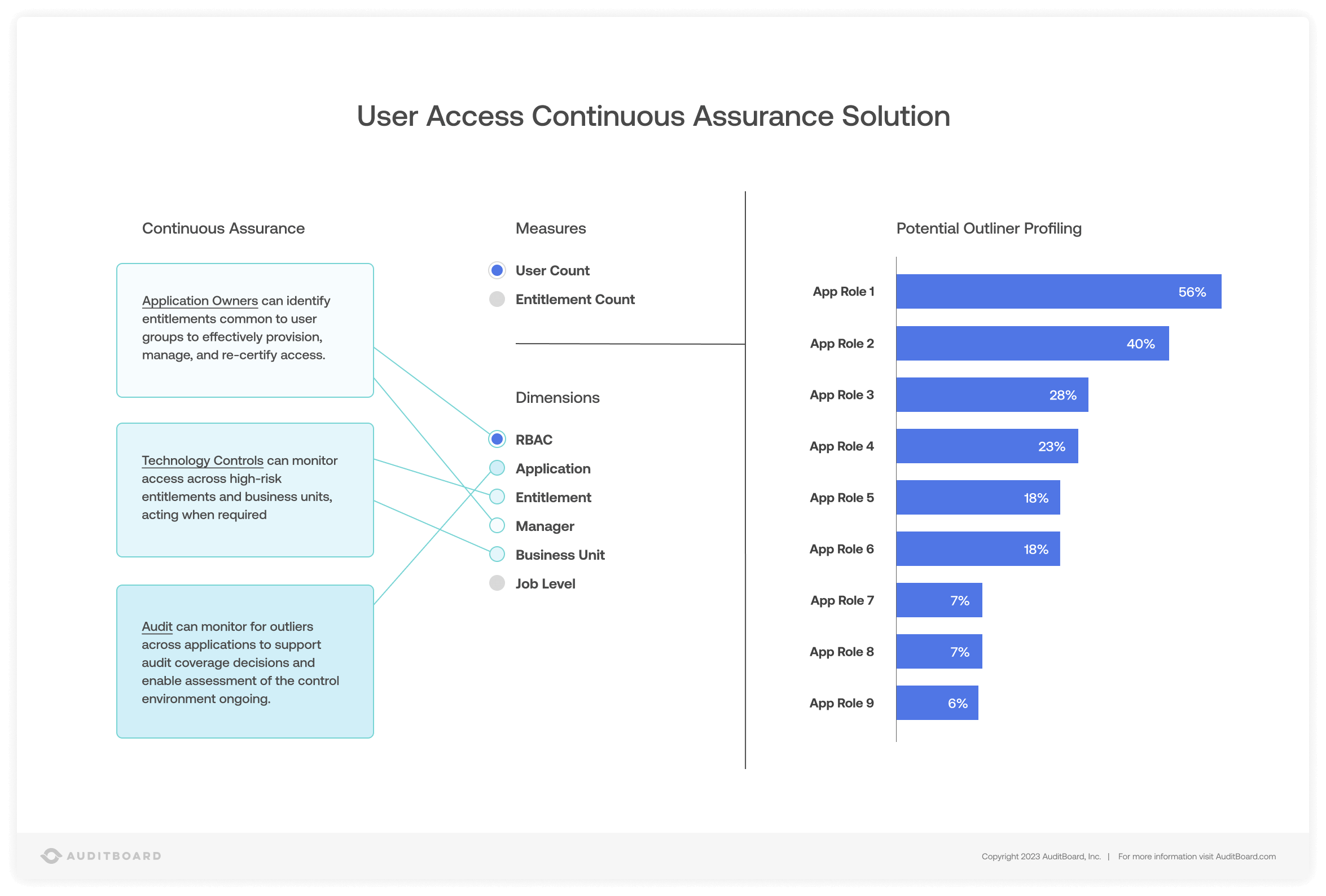
When we combine that data, our BI solution provides visibility into users who have retained their access beyond their termination date, job changes that require an off-cycle review of the user’s access (and potential removal of access that is no longer necessary), access that is not consistent with users in a similar role, and users who have not logged into their account for a certain time (which may indicate that the access is no longer needed).
When performing required manual access reviews (which typically occur every six months or annually, depending on the organization), people determining the appropriateness of access rights often are not provided with data that would enable them to make more informed decisions. Not only does our solution provide this intelligence to the access reviewer, but adding automation to the business intelligence solution enables the first line to establish rules such as removing access that has been dormant for six months.
It’s important to note that the BI dashboard itself is not the control — the action taken by the first or second line utilizing the information presented in the dashboard is the control.
- The first line takes action on data anomalies that may represent unmanaged risks or control failures through users’ possessing unnecessary access.
- The second line provides oversight to ensure the first line is effectively and timely actioning these anomalies.
- As the third line, internal audit conducts formal, periodic control assessments that report on the consistency of the first and second lines’ compliance with executing their control requirements. If it appears as if control exceptions exist, audit can ask targeted questions as to why the first line did not remediate these specific issues and why the second line did not follow up to understand why these issues remain unmitigated.
As part of continuing assurance, internal audit should issue a periodic, insightful report to the business that directly answers the question: “Are we doing a better job of managing access or a poorer job of managing access based on our quarter-by-quarter performance?” Because of the timely, frequent, and transparent nature of these reports, they are typically well-received by management. Additionally, implementing continuous assurance reduces (if not removes) the time needed to test user access on individual audits.
As we look to harness the advances in artificial intelligence on top of what we built, we can take our solution to the next level by enabling the organization to define Role-Based Access Controls (RBAC) as well as increase the entitlements that can be assigned to all new employees as part of birthright access.
Earning Trusted Partner Status
Through this collaboration, stakeholders’ view of audit is evolving. Investments in analytic capabilities mean that audit is increasingly sought out to provide an independent, data-driven perspective on the organization’s risk management capabilities and operating effectiveness of controls. By developing and coordinating an approach to continuous assurance, management teams increasingly view internal audit as trusted business partners to the organization who provide timely, valuable insights. Sometimes when audit doesn’t have a seat at the table, you need to make your own chair and pull it up yourself.
About the authors

David Malcom is an SVP and Managing Director in Northern Trust’s Audit Services department, where he oversees the Data and Digital team. David has 23 years of audit, data analytics, risk consulting, and information security experience. Prior to joining Northern Trust, David worked with organizations including Accenture, Hyatt Hotels Corporation, and PricewaterhouseCoopers. Connect with David on LinkedIn.

Joe Gonski is an SVP and Director in Northern Trust’s Audit Services department where is the Data Analytics Program Lead. Joe has 17 years of audit and data analyics experience. Prior to joining Northern Trust, Joe worked with organizations including Accenture, KPMG, and CNA Insurance. Connect with Joe on LinkedIn.
You may also like to read


Audit reporting best practices: Guide for audit leaders
Latest data on AI adoption reinforces need for internal auditors’ “superpowers”

AuditBoard and IAF report: The more you know about AI-enabled fraud, the better equipped you are to fight it

Audit reporting best practices: Guide for audit leaders

Latest data on AI adoption reinforces need for internal auditors’ “superpowers”
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO