
January 26, 2026 • 20 min read
IT vendor risk management: Best practices for managing third-party tech risk

Mindi Scorey
Your IT ecosystem is built on countless third-party vendors. Think SaaS tools, cloud providers, and service partners. Each IT vendor adds value, but they also add risk. From compliance gaps to service outages, even one weak link can cause chaos. Let’s explore the best ways to manage vendor risk proactively so you benefit from third-party tools while keeping your business resilient.
What is IT vendor risk management?
Your IT stack is a mix of SaaS tools, cloud platforms, and service providers. Each one can offer significant benefits like efficiency and operational agility, but they also introduce potential risks.
And we’re not just talking about cybersecurity risks. Misconfigurations, compliance gaps, and vendor outages can all disrupt operations and expose sensitive data.
A robust VRM program is essential for safeguarding your organization and helps you stay ahead of issues by identifying, assessing, and monitoring risks throughout the vendor lifecycle. By ensuring each vendor aligns with your security and compliance requirements, your VRM program will help protect both your day-to-day performance and long-term business continuity.
Key characteristics of IT vendor risk
Unlike other third-party vendors, IT vendors sit deep inside your business operations and systems. They manage data, connect through APIs, and influence how securely and reliably your business runs.
Therefore, IT vendor risks have very specific characteristics you need to account for, including:
- Deep access: Vendors often have admin rights or network connections that touch core infrastructure.
- Sensitive data handling: Many IT vendors handle customer, employee, or financial information across borders.
- Shared compliance: The regulatory practices of your IT vendors can affect your compliance standing with frameworks like GDPR, HIPAA, or ISO 27001.
- Operational impact: Operational stability is compromised the moment a critical vendor fails.
- Constant change: Risks constantly shift due to updates, integrations, and new tools.
As a result, ongoing oversight is essential. Continuous monitoring of IT vendor risks is the only way to keep tight control and make sure you’re fully compliant.
Common sources: SaaS, cloud, infrastructure, data processors
Your vendor ecosystem stretches far beyond cybersecurity tools. It includes every platform that touches your data, users, or workflows. In this respect, risks can come from anywhere.
Here are a few common sources of IT vendor risk:
- SaaS applications like CRMs, HR systems, and messaging tools connect directly to business data, making credential leaks or weak integrations a real concern.
- Cloud providers such as AWS or Azure keep operations running, but shared-responsibility gaps and setup errors often open the door to threats.
- Infrastructure and managed service partners control uptime, network security, and physical access, leaving you exposed to outages or security lapses if their controls fail.
- Data processors handle sensitive information under strict privacy laws, but their mistakes can result in financial liabilities, regulatory fines, and brand damage.
- Emerging tools like AI platforms and DevOps integrations drive innovation but widen your digital supply chain, creating new points of risk.
Each relationship you build with an IT vendor brings unique operational, compliance, and financial risks. That’s why vendor risk assessments and continuous monitoring are so critical. Without them, you lose visibility into emerging risks as your tech stack expands.
Business impact of unmanaged IT vendor risk
Unmonitored vendors create business risk.
Firstly, breaches are costly. According to IBM’s 2024 Cost of a Data Breach Report, the average cost of a vendor-related breach is $4.91 million per incident. And what makes matters worse is that IT vendors sit at the heart of this. In fact, the same report found that nearly 30% of AI-related security incidents came from third-party SaaS vendors.
But it’s not just the money. It’s also about business continuity.
Vendor outages are highly damaging. The Uptime Institute’s 2024 analysis found that 10% of outages originated from vendors, and over half cost companies more than $100,000.
Beyond downtime, there’s also reputational risk. Security events and stalled operations erode customer trust, trigger PR crises, and divert resources from growth to damage control.
Compliance failures add another hit. If a vendor mishandles data under GDPR or HIPAA, you share the liability. This means fines, audits, and even contract losses.
A strong vendor risk management program limits that exposure by continuously monitoring vendor performance, verifying compliance, and aligning third parties to your security standards. This prevents small risks turning into big business disruptions.
Key categories of IT vendor risk
In today’s connected IT environment, third-party vendors are no longer peripheral. They’re inside your operations, your data, and often your customers’ trust.
A strong IT VRM program is the only way to see these hidden dependencies clearly and manage them before they become business-wide disruptions.
Here are the risks you’re facing with each IT connection.
Security risks
Cybersecurity threats from third-party vendors are common and costly.
In fact, Verizon’s 2025 Data Breach Investigations report shows that 30% of all breaches involve a third party, and Cyberark’s Identity Threat Landscape report shows that 80% of organizations experienced a successful supply-chain attack between 2023 and 2024.
But what risks make you vulnerable to a breach?
- Stolen or leaked vendor credentials used to access your systems
- Misconfigured settings that expose data or weaken authentication
- Unpatched software with known security flaws
- Malicious code inserted into vendor updates or shared tools
- Weak APIs that allow unauthorized access or data interception
In these scenarios, a weakness in the vendor’s system becomes an entry point attackers can use to reach your data.
But it’s not just data breaches that pose a threat. Security risk also covers the quieter vulnerabilities that build up over time.
- Over-privileged vendor accounts that grant unnecessary access
- Unsecured data storage without encryption or audit trails
- Shadow IT tools adopted by vendors without approval
- Poor monitoring of vendor activity across shared systems
- Infrequent configuration reviews that allow risky drift
In these situations, no single incident triggers the breach, but weak oversight allows risks to accumulate until a failure becomes inevitable.
And when you combine both types of security threats together, you get gaps in a vendor’s environment that expose your systems, data, and customers.
Compliance risk (frameworks like SOC 2, ISO, GDPR)
Compliance risk refers to the possibility that a vendor’s failure to meet regulatory, legal, or contractual requirements exposes your organization to the same non-compliance. Ultimately, if a vendor isn’t compliant, often neither are you.
For example, a data processor storing EU data in the wrong jurisdiction can instantly put your organization out of alignment with GDPR.
Other compliance issues include:
- Vendors processing personal data without required consent
- Vendors failing to maintain audit-ready security controls
- Missing or outdated data retention and deletion policies
- Cross-border transfers without lawful safeguards
- Subcontractors without proper compliance assurances
And regulators aren’t sympathetic. Non-compliance triggers huge fines. For instance, a breach of GDPR can result in fines of up to €20 million or 4% of global revenue.
Even without fines, non-compliance is costly. Failed audits can slow procurement, delay deals, and damage customer confidence.
Performance risks
Performance risk refers to vendor-caused slowdowns or outages that disrupt the availability and responsiveness of your systems and services. A performance failure, like a cloud outage or sluggish API, can grind operations to a halt and cost thousands of dollars to fix.
Beyond the cost of fixing outages, you also lose time and money because downtime erodes productivity. And if you can’t provide services to your clients, you risk breaching service level agreements (SLAs), which undermines customer trust.
That’s before you address the hidden costs, like emergency overtime, workaround development, and customer churn.
Performance threats to look out for include:
- Recurring vendor outages that interrupt core services
- Latency or slow API response times that delay transactions
- Degraded system performance during peak workloads
- Missed SLA uptime or response guarantees
- Conflicting maintenance windows that cause downtime
- Capacity limits that prevent scaling when demand spikes
Resilience risks
Resilience risk refers to a vendor’s ability to keep operating through disruptions and recover quickly when failures occur. Signals include weak disaster recovery testing, single points of failure, and business continuity or disaster recovery (BCP/DR) plans. And if a vendor operates from a single data center or hasn’t tested its recovery process, every disruption ripples straight through your business.
The result isn’t just downtime. It’s lost data, missed deadlines, failed customer commitments, and potential regulatory breaches if critical systems go dark. Without resilience at the vendor level, your own business continuity strategy is only as strong as its weakest link.
Integration risks
Integration risk refers to risks caused when vendor systems fail to interoperate reliably with your existing tech stack. Common triggers include API failures, unsupported versions, authentication issues, or incompatible data formats.
And as digital ecosystems expand, integration risk has become a quiet but serious threat to performance. When APIs break, versions fall out of sync, or authentication fails, critical systems stop talking to each other.
The impact is immediate. Your automations fail, data becomes unreliable, and teams are forced into manual workarounds. Over time, these gaps slow innovation and increase security exposure, while ramping up maintenance costs across your vendor ecosystem.
Best practices for managing IT vendor risk
Managing IT vendor risk relies on knowing where weaknesses hide and building habits that keep you ahead of them.
Here’s how to keep your ecosystem secure, compliant, and reliable.
Conduct pre-contract due diligence
Before you sign anything, make sure you know who you’re dealing with.
Ask for proof of SOC 2, ISO 27001, or GDPR compliance, and review how vendors encrypt, store, and share your data. Check their financial stability, business continuity plans, and any history of breaches or regulatory action.
Try building standardized questionnaires and giving vendors security ratings so you can compare them and spot early red flags.
Implement continuous monitoring and alerts
Vendor risk changes constantly as systems update, teams shift, and threats evolve. Continuous monitoring gives you early warning. This means that instead of reacting to crises, you can act before risks escalate into losses.
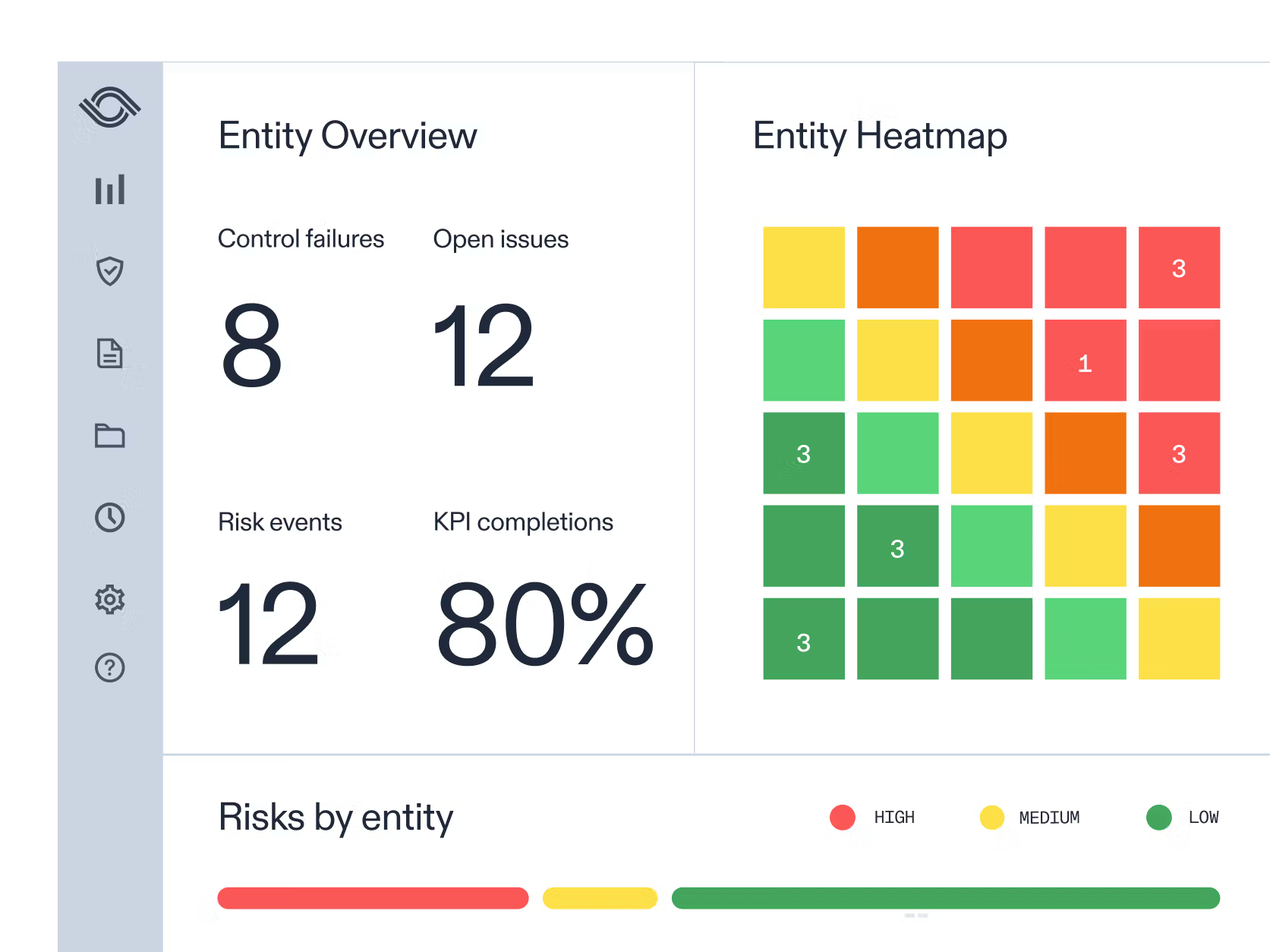
Use automated tools to track security ratings, SLA performance, and compliance status in real time. Set alerts for expiring certifications or incident reports, and review dashboards regularly with key stakeholders.
Align vendor SLAs with risk tolerance
Your service level agreements should match how much risk your business can afford, not what’s easiest for the vendor.
Define exactly what “good performance” looks like. Specify how much uptime you expect, how quickly the vendor must respond to issues, and how long they have to recover from outages.
If they fall short, your contract should include penalties or service credits.
But don’t stop at performance. Make sure your agreements also cover security and compliance standards, so vendors stay accountable for protecting your data too.
Require remediation timelines and attestations
If you find gaps during onboarding or while working with a vendor, don’t just accept verbal assurances. Set clear deadlines in the contract for fixing each issue, whether it’s a missing certification, an unpatched system, or a failed control. Then ask for evidence that the problem’s resolved, such as updated audit reports and patch confirmations.
Track everything through your vendor risk management platform so you can see actual progress in real time. That way, “we’re working on it” becomes measurable accountability, not an empty promise.
Continuous monitoring and automation
In modern vendor ecosystems, continuous oversight is the only way to stay ahead of fast-moving risks.
Here’s what that looks like.
Leveraging APIs and integrations for monitoring
APIs connect your VRM platform directly to vendor systems, feeding real-time data on incidents, configuration changes, and compliance status.
This eliminates manual check-ins and gives IT and risk teams instant visibility into emerging threats or performance drops.
Automating evidence collection
Automation tools pull updated SOC 2 reports, certifications, and remediation proofs without waiting for vendor responses. This keeps your vendor files current, audit-ready, and consistent with regulatory requirements like GDPR and ISO 27001.
Building dashboards for IT risk visibility
Centralized dashboards turn raw data into actionable insights. They highlight high-risk vendors, track SLA trends, and visualize overall security posture across your vendor ecosystem. With this data at your fingertips, you can make faster, data-backed decisions about risk.
Communicating IT vendor risk to leadership
Strong vendor risk management only works if leadership understands what’s at stake and why it matters.
But it’s not always easy to communicate that effectively. Here are some tips.
Reporting critical findings in executive language
Translate technical issues and jargon into business impact.
Don’t just list vulnerabilities. Explain what they mean for operations, compliance, or reputation.
For example, “This vendor’s data breach could disrupt payroll for 5,000 employees” is far clearer than “S3 bucket misconfiguration detected.”
Using metrics and trends to demonstrate control
Leaders want progress, not panic.
Use metrics like the number of high-risk vendors reduced, mean time to remediate (MTTR), or SLA uptime trends to show your VRM program is working.
To make this information clearer, use visual dashboards that illustrate improvements at a glance.
Linking IT vendor risk to enterprise objectives
Connect third-party risk directly to goals like business continuity, customer trust, and regulatory compliance. For example, if a cloud provider’s outage halts customer logins for hours, it’s not just an IT issue. It’s also a customer experience problem that affects revenue and brand reputation.
By showing how vendor disruptions or compliance gaps impact larger business objectives, you help leadership see IT risk management as essential to growth and resilience.
How AuditBoard enables IT vendor risk oversight
AuditBoard brings clarity, control, and connection to IT vendor risk management by unifying oversight across teams, tools, and frameworks, all within one platform.
Here’s how.
Centralized IT vendor register
AuditBoard’s centralized vendor register gives teams a complete view of every third-party relationship, from SaaS providers to data processors.
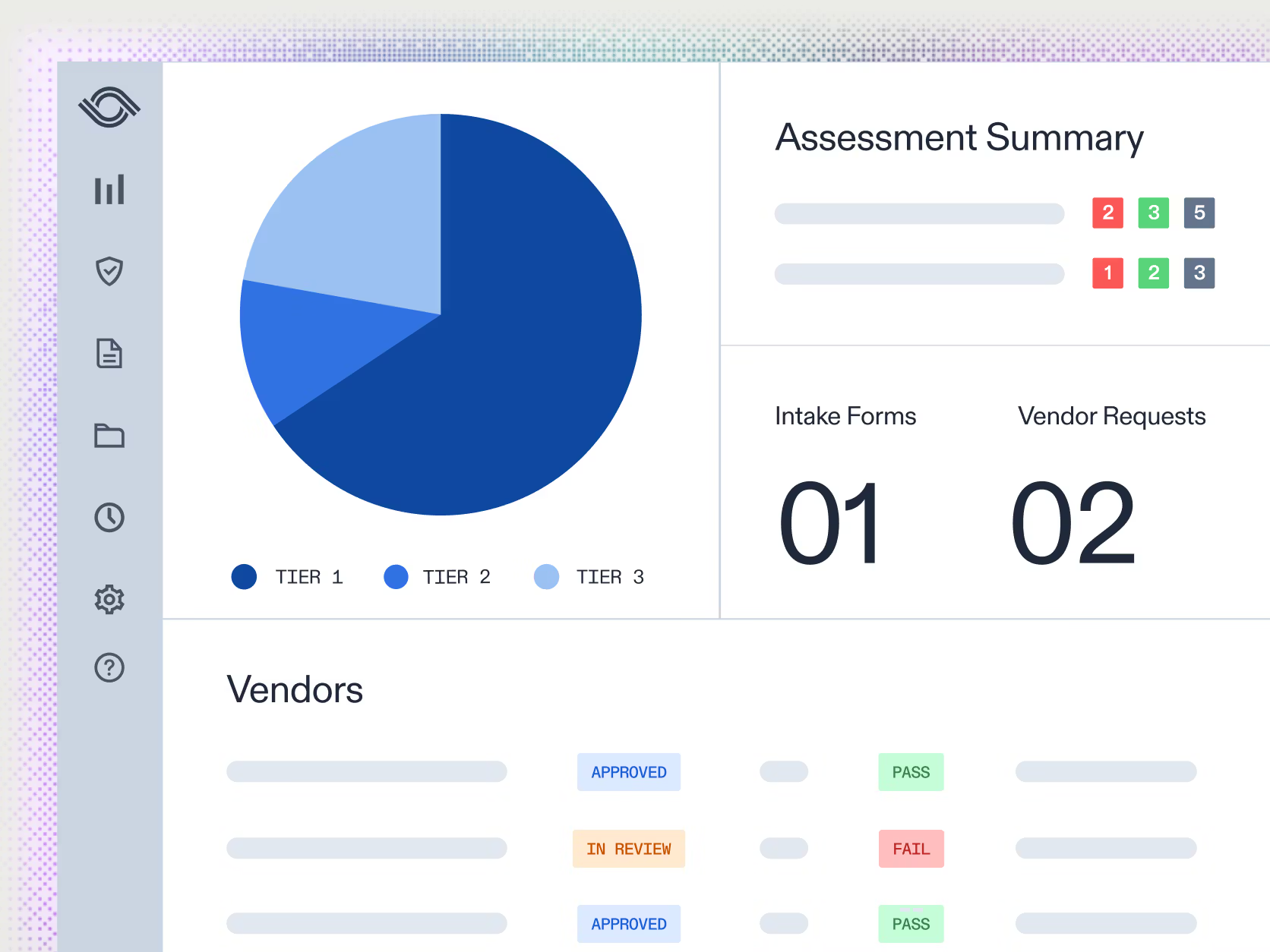
You can track vendor criticality, monitor risk ratings, and link each vendor to the controls, frameworks, and business units they support. This cuts out blind spots and simplifies reporting for stakeholders and auditors.
Integration with existing IT tools (SIEM, CMDB)
Through API integrations with tools like SIEMs, CMDBs, and risk monitoring platforms, AuditBoard pulls real-time data on incidents, configurations, and asset dependencies.
That way, vendor risks are automatically reflected in your broader cybersecurity and operational risk ecosystem, so everything’s synchronized and visible.
Automated evidence collection and reporting
AuditBoard automates evidence collection, pulling the latest SOC 2 reports, certifications, and remediation updates into one secure system.
Plus, AuditBoard’s interactive dashboards and ready-to-share reports translate this data into actionable insights for leadership.
The result? Faster audits, fewer manual errors, and a more proactive, data-driven vendor risk management program.
Request a demo today to see how AuditBoard streamlines your entire vendor risk management program.
About the authors

Mindi Scorey, CISA, is a Manager of Product Solutions (ITRC) at AuditBoard, where she serves as a product expert on the AuditBoard platform. Prior to AuditBoard, Mindi spent over ten years in the Global Internal Audit organization at Unum Group where she served in several roles including Director of IT SOX and Director of Professional Practices. Connect with Mindi on LinkedIn.
You may also like to read


Shadow AI: Audit privacy risks in your data supply chain

12 vendor risk management metrics every compliance leader should track

The ultimate vendor risk assessment checklist for compliance teams

Shadow AI: Audit privacy risks in your data supply chain

12 vendor risk management metrics every compliance leader should track
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO



