
October 20, 2022 • 7 min read
Five Things Companies Are Doing Today to Get Ahead of Upcoming SEC Cybersecurity Rules

Richard Marcus
In my capacity leading Information Security at AuditBoard, I oversee product, infrastructure, and enterprise security, as well as all of the audit, compliance, and risk functions we perform internally. But one of my favorite parts of the job is getting to speak to InfoSec leaders across our customer base. Lately, I have been hearing a lot of organizations discuss their plans for tackling the cybersecurity disclosure changes coming soon from the SEC. I’d like to share some insights I’ve obtained from our community’s best with the broader community.
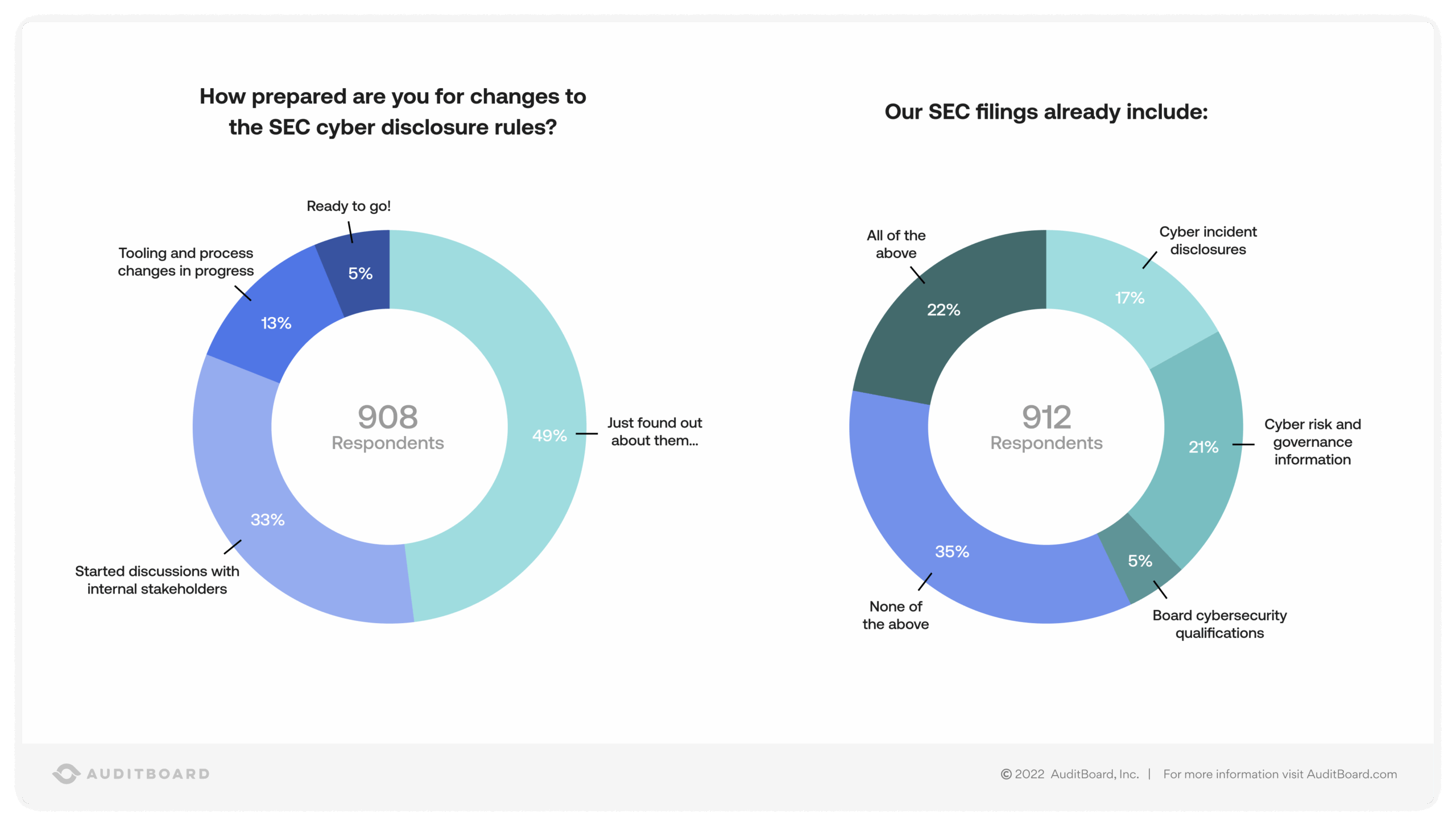
In an August 2022 flash poll conducted by AuditBoard, 48% of over 900 audit, risk, and compliance respondents said that they “just found out” about the proposed rule changes. In addition, 35% of the group said that their current SEC filing practices do not currently include cyber incident disclosures, cyber risk and governance information, or board cybersecurity qualifications. If your business is in a similar position, you have some ground to cover before you are prepared for the SEC’s new requirements.
The new rules require reporting on material cybersecurity breaches including more recurring and aggregated look-back reporting on all incidents — and not just point-in-time reporting. It also calls for descriptions of the way cybersecurity governance is performed, specifically regarding policies and procedures and management’s role in that process. There are reporting requirements about the board and the interaction with the board that may become mandatory, as well as discussion of internal policies and procedures regarding third-party and cybersecurity risk, including management’s role.
Given the coming changes and deeper disclosure regulations, it’s smart for organizations to get ahead of the shift and start using the tools and building the processes needed to meet the new requirements. Here are five things that sophisticated companies are doing today that your organization can learn from.
1. Improving cybersecurity expertise amongst their boards.
Historically, many boards have lacked the qualifications to be able to participate in meaningful conversations about cybersecurity with leadership teams. This can lead to less visibility and influence for CISOs and less funding for mission-critical security initiatives due to an overall lack of understanding. Given the new regulations requiring statements about board cybersecurity competency, some organizations are getting ahead of this need by bringing in more board-level InfoSec expertise so that risk and compliance can have meaningful interactions with the board. We’re seeing that boards are starting to take a greater interest in these topics and companies are looking to staff these skill sets on the board when they recruit and evaluate candidates for board positions.
2. Properly resourcing risk assessment, mitigation, and control.
These changing standards are a great opportunity for us to surface issues at a higher level within the organization, to help executive teams and boards make risk-based decisions, and to ensure that controls and risk mitigations are properly prioritized and resourced. Having board visibility into these issues is a useful way for InfoSec teams to position themselves to get more well-deserved attention, and potentially even redraw the org chart to bring more attention to the right areas.
3. Taking advantage of the shift to increased transparency.
It must be acknowledged that government regulation tends to lag culture. These SEC-led initiatives are coming downstream of a greater cultural movement to increase transparency — whether you are publicly traded or not. Shareholders and consumers want more visibility into the organizations that they interact with, and the companies that you do business with want to know more about you. These SEC changes are something that you can point to in order to help your business leadership understand why more transparency might be something they want to incorporate into their practices — not just for the sake of compliance, but also to foster public perceptions of trust and assurance.
4. Increasing scrutiny on third-party vendors and suppliers.
With third-party cybersecurity incidents impacting disclosures for larger organizations, there is even more pressure to make sure that all vendor relationships meet big business criteria and needs. Those third-party organizations may not have SEC reporting disclosure requirements that apply to them directly, but they need to know that their upstream customers have this requirement and that they can expect increased scrutiny all the way down the supply chain.
5. Reviewing competitor disclosures.
I recommend looking at your competitors and getting a sense of what is standard in existing reporting and release documentation. There are companies completing voluntary reporting in these areas already, and typically larger, more established, and more mature companies are a good place to look. It’s worthwhile to review industry-specific filings in your area — think of it as helpful peer pressure.
There is a lot to consider for your company in advance of these changes. Take a cue from what larger organizations are doing, and leverage security compliance technology to help you prepare your organization for the new SEC requirements.
About the authors

Richard Marcus, CISA, CRISC, CISM, TPECS, is the CISO at AuditBoard, where he is focused on product, infrastructure, and corporate IT security, as well as leading the charge on AuditBoard’s own internal compliance initiatives. In this capacity, he has become an AuditBoard product power user, leveraging the platform’s robust feature set to satisfy compliance, risk assessment, and audit use cases. Connect with Richard on LinkedIn.
You may also like to read

What is the Colorado AI Act? A detailed guide to SB 205

What is the EU AI Act?

What is the NIST AI Risk Management Framework?
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO



