
July 2, 2025 • 20 min read
Best SOC 2 compliance software for long-term readiness

Jimmy Pfleger
SOC 2 deadlines create panic. Teams scramble through spreadsheets, chase evidence across email threads, and pray nothing falls through the cracks. Meanwhile, auditors ask the same questions your organization answered six months ago, but the documentation lives somewhere between three different tools and a folder marked "Important."
Most SOC 2 compliance software promises quick fixes with automation-first approaches. These tools help startups check boxes fast, but they crumble under complexity. When your environment includes multiple cloud providers or your SOC 2 scope keeps shifting as new technology comes in, one-size-fits-all solutions leave gaps that auditors notice immediately.
The real cost? Failed audits force expensive remediation cycles. Incomplete control mapping exposes your organization to actual security risks (like exposing customer data). Disconnected evidence collection means you're rebuilding documentation from scratch every audit cycle.
The global average cost of a data breach in 2024 hit a record high with a 10% increase over last year. Lost business costs from data breaches averaged $2.8 million in 2024, factoring in lost customers, downtime, post-breach response, and regulatory fines.
Here's what successful compliance teams know: SOC 2 readiness works year-round, not just during audit season. The right platform maps controls to your actual environment, automates evidence collection without losing context, and connects security practices to business operations.
Modern SOC 2 compliance software handles this complexity while keeping your team focused on what matters: building security into your operations vs. just documenting it.
What is SOC 2 compliance software, and what should it do?
SOC 2 compliance software tracks your security controls and collects evidence for audits. But most tools stop at basic automation. They'll grab screenshots and generate reports, but they miss the bigger picture of how your security actually works.
The first thing to do when you’re getting SOC 2 ready isn’t shopping for software — it’s taking stock of what you already have. If your team’s worked with frameworks like CIS, SOC 1, NIST, ISO, or PCI, chances are you’ve got plenty of controls and evidence that count toward SOC 2. The strongest platforms help you spot what already fits, so you’re not reinventing the wheel or doing double work. Instead, you map what’s in place, fill the true gaps, and move faster toward audit readiness.
Effective SOC 2 platforms align with your actual business processes, capturing context, control ownership, evidence sources, and risk linkage, rather than relying solely on predefined templates. It maps controls to what you do, not some generic template. When your team changes access permissions or updates security policies, the platform should capture that context. That's what real compliance automation looks like.
More than just checklists and automation
Walk into any compliance meeting, and someone will mention "automated evidence collection." Yes, automation tools help. But if that's all your tool does, you're missing the point.
Here's what really matters:
Your controls should match your reality
Every company builds security differently. You might use Okta for identity management while your competitor uses Azure AD. Your SOC 2 tool should adapt to how you work, instead of forcing you into someone else's framework. This flexibility protects your sensitive data while meeting compliance requirements.
Say you have a custom approval workflow for production deployments. Generic tools can't handle that. They assume you use standard change management processes. But your auditor wants to see how your actual process works vs. how a template thinks it should work.
Evidence needs the full story
Screenshots prove something happened. But auditors want to know why it happened and who made it happen. Context matters.
Think about access reviews. A basic tool shows you ran a quarterly review. A better tool shows who approved each access change, what they considered, and how exceptions were handled. That's the difference between checking a box and proving your control works.
Integrations should integrate
Lots of tools brag about connecting to 100+ systems. But connecting and integrating are different things. True integration means that when you update a user's role in your HR system, that change flows through to your SOC 2 evidence automatically. In turn, you get a seamless compliance process.
Why one-time readiness won't scale
Audit season arrives and your team drops everything to gather evidence. You're pulling reports, tracking down documentation, and hoping nothing's changed since last year.
That approach worked when your company had 50 employees. But now you're at 200, adding new systems quarterly and facing multiple compliance requirements. The scramble gets worse each year and becomes increasingly time-consuming.
Here's what changes when you move to continuous readiness: Instead of three months of chaos, you spread the work across 12 months. Controls get tested regularly. Evidence collects automatically. When audit time comes, you're already prepared.
The real win? Your information security improves because controls work year-round.
What to look for in a SOC 2 compliance solution
The best SOC 2 tools solve problems you didn't know you had. They connect scattered controls into a unified view, turn manual evidence collection into automated workflows, and give you confidence that nothing falls through the cracks.
With 23% of SOC 2 reports now containing over 150 security controls — up from 16% in 2023 — the complexity of managing compliance has grown significantly.
Here's what separates tools that help from those that just add complexity:
Central control mapping
Your SOC 2 controls shouldn't live in isolation.
Let’s say you introduce a new password policy. That single control might apply to more than just the Security Trust Service Criteria — it could also cover Availability or Processing Integrity, if those are in scope for your SOC 2.
The right platform won’t make you map each one by hand. Instead, you assign the control once, and updates automatically flow to every area it touches. If you strengthen a control or change your process, that change gets reflected everywhere it matters, so you’re not juggling overlapping requirements or risking inconsistencies in your audit evidence.
Most tools treat each control as a separate checklist item. But controls overlap in real environments. Your access review process touches user provisioning, privilege management, and termination procedures. When one part changes, the others need to update too.
Central control mapping also helps during SOC 2 audit preparation. Instead of scrambling to show how different controls relate to each other, you have a clear view of dependencies and overlaps.
Evidence collection and retention
Evidence collection should happen in the background while your team focuses on actual security work. The platform should capture what happened, when it happened, and who was involved, without requiring manual uploads or screenshots.
Here's what good evidence collection looks like:
- Automatic time-stamping: Every action logged with precise timing
- Role-based attribution: Clear records of who performed each action
- Change tracking: Before and after states for any security modifications
- Retention policies: Evidence stays accessible for the full audit period
Bad evidence collection requires your team to remember what they did and document it later. Good evidence collection captures everything as it happens, so your audit trail builds itself. And you get a comprehensive view of your security program.
Cloud and security integrations
Your SOC 2 platform should connect to the tools you already use. Deep integrations with cloud providers, identity systems, and security tools mean evidence flows automatically instead of requiring manual exports.
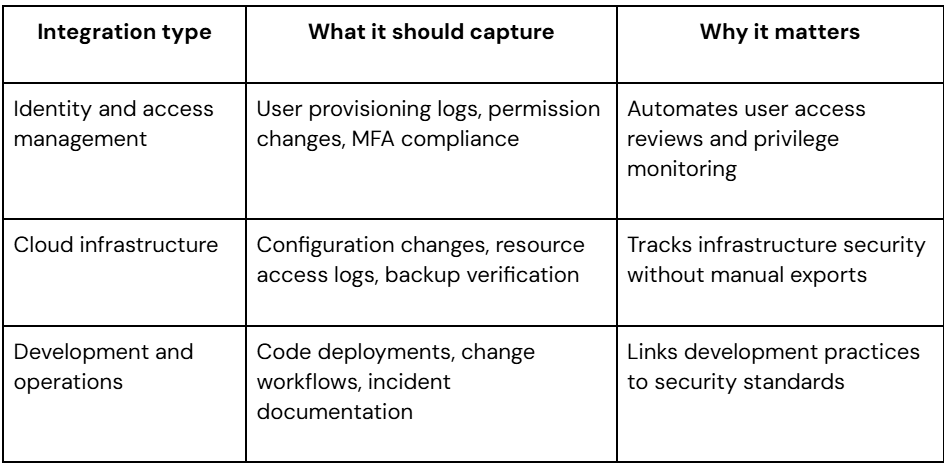
Workflow and policy support
SOC 2 compliance involves people and technology. Your platform should support approval workflows, policy reviews, and team collaboration without forcing everyone into rigid processes.
When your security team updates an incident response procedure, the platform should route it through legal, IT, and management for review. Each stakeholder sees only what they need to evaluate, and the approval process moves forward automatically once everyone signs off.
Real-time visibility and audit readiness
You should know your audit status at any moment without running reports or checking multiple systems. Continuous monitoring through real-time dashboards shows control health, evidence completeness, and any gaps that need attention.
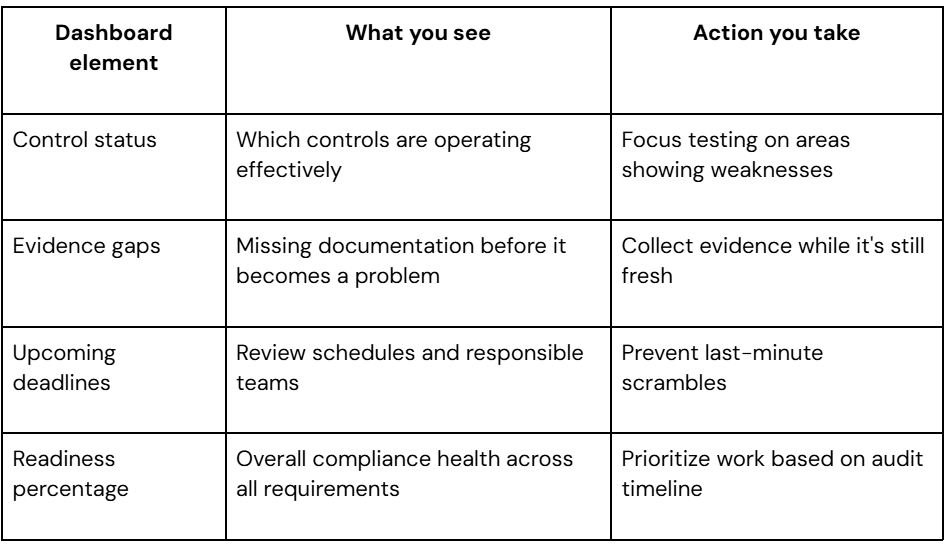
Think of it like a car dashboard. You don't need to understand every detail, but you should immediately know if something needs attention. Your SOC 2 dashboard should give you the same instant awareness of your compliance health.
“We're able to build Power BI dashboards that I use to report to the audit committee — I just press refresh, export it out, import it into my audit report, and I'm done. During the audit committee meeting, if I get a question I'm able to drill down very quickly to get the answers.” (Rob Zunt, VP of Internal Audit and Bambi Gifford, Manager of Internal Audit at U.S. Xpress)
Top SOC 2 compliance tool in 2025
The right SOC 2 platform should anchor your entire compliance program while connecting seamlessly to the tools your teams already use. Instead of replacing everything, smart organizations build around a central compliance hub that integrates with their existing security stack.
Here's how the best platform works with complementary tools to create a unified compliance ecosystem:
AuditBoard
AuditBoard supports every stage of your SOC 2 program, including scoping, mapping controls to frameworks, collecting evidence, and collaborating with internal or external auditors. The platform helps you define what’s in-scope, connect controls to real business processes, automate evidence collection, and keep everyone aligned through the audit cycle.
What sets AuditBoard apart:
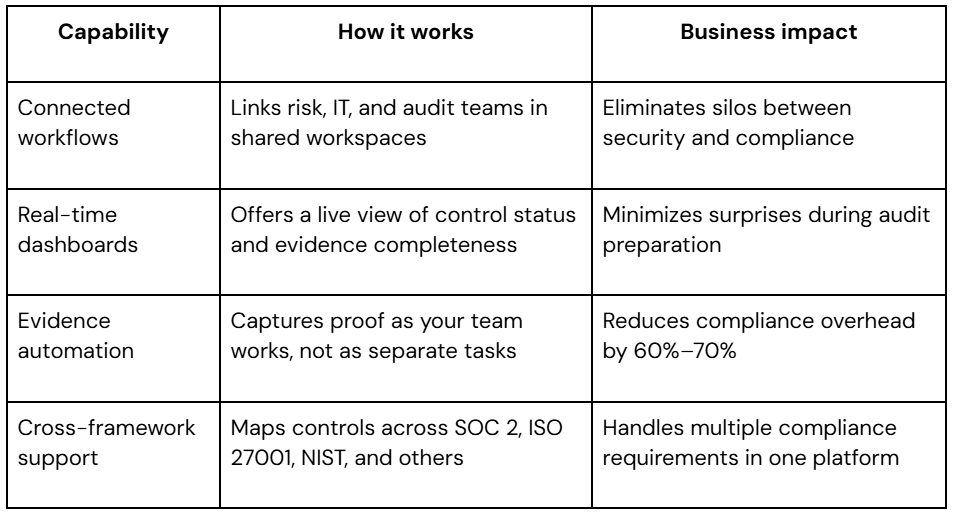
AuditBoard's strength lies in bringing your entire SOC 2 compliance strategy together. When your access review process connects to your incident response procedures, and both feed into your audit evidence automatically, compliance becomes part of operations rather than a separate burden.
Why platform integration matters more than feature overlap
Many organizations try to solve SOC 2 compliance by adding point solutions for each requirement. This approach creates more problems than it solves:
The integration advantage:
- Changes in one system automatically update compliance evidence.
- Audit trails connect across all your security tools.
- Teams work in familiar interfaces while compliance happens in the background.
- Auditor requests and evidence delivery are combined into a single source of truth.
What to avoid:
- Tools that duplicate functionality without adding value.
- Solutions that require manual data entry or evidence uploads.
- Platforms that can't connect to your existing security stack.
- Point solutions that create new silos instead of connecting existing ones.
The goal isn't to have the most tools; it's to have tools that work together to make your security posture visible, measurable, and audit-ready. Many companies turn to service providers for initial setup, but the right platform reduces that dependency over time.
Choosing the right fit for your organization
Not every SOC 2 tool works for every company. Your choice depends on where you are now, where you're heading, and how complex your environment is. Here's how to match your needs to the right approach:
Speed vs. scalability
Early-stage companies often prioritize speed over everything else. Quick compliance tools help startups get their first SOC 2 report fast, but they struggle as companies grow. The question isn't, “Can I get compliant quickly?” What you should ask is, “Will my compliance solution still work in two years?”
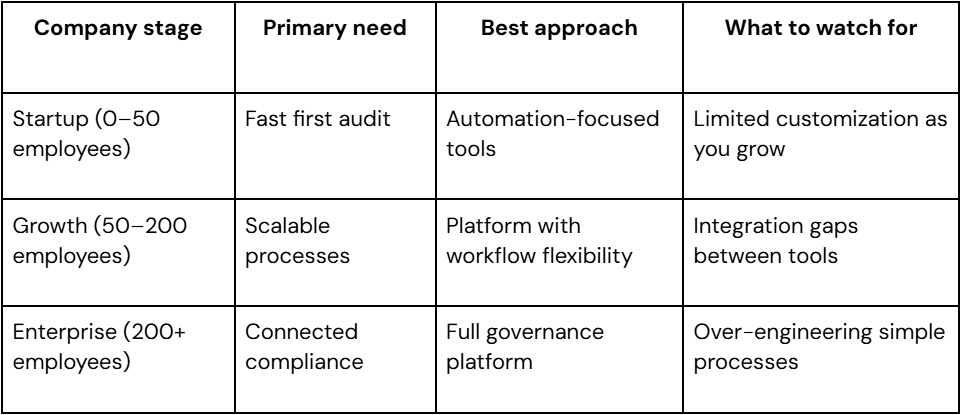
Quick tools work when your security environment is straightforward. But if you're adding new systems quarterly, hiring across multiple locations, or facing additional compliance requirements, you need something that grows with you.
Automation-first vs. risk-aligned platforms
Automation-first tools promise to handle SOC 2 compliance with minimal human involvement. They're appealing because they require less up-front work, but they often miss the nuances that matter during audits.
Risk-aligned platforms require more setup but adapt to your actual business processes. When auditors ask about your custom deployment workflow or unique data handling procedures, you have documented compliance controls that match what you truly do.
When automation-first works:
- Standard SaaS environment with minimal customization
- Limited compliance requirements beyond SOC 2
- Small teams that need to focus on product development
When you need risk-aligned:
- Custom security processes or unique infrastructure
- Multiple compliance frameworks (SOC 2, ISO 27001, etc.)
- Complex approval workflows or exception handling
Startups vs. mature environments
Startups can often get away with simpler tools because their environments are less complex. But mature organizations have legacy systems, custom integrations, and established processes that generic tools can't handle.
For mature companies, there’s another layer: the right platform should support mapping controls and collecting evidence across multiple frameworks — not just SOC 2, but others like ISO 27001, PCI, or HIPAA — so you’re not building one-off systems for every new requirement.
The real test: Can your SOC 2 tool handle the weird stuff? Every organization has unique requirements, like custom approval workflows, legacy system integrations, or industry-specific controls. Basic tools break down when you need them to adapt.
Consider how your SOC 2 framework needs to interact with existing governance processes. If you already have risk management, internal audit, or regulatory compliance programs, your SOC 2 tool should connect to those efforts rather than creating parallel processes.
Making the decision
Start with your current pain points:
- If your biggest problem is getting started: Choose a tool that can deliver your first SOC 2 report quickly, but plan for platform migration as you grow. Look for vendors with straightforward onboarding processes to minimize setup time.
- If you're drowning in manual processes: Look for automation that connects to your existing tools rather than requiring new workflows.
- If audits keep finding gaps: You need a system that helps you stay proactive, not just reactive. Look for a platform that lets you review your controls and audit artifacts thoroughly — so you catch issues early and close gaps before the next audit cycle.
- If compliance feels disconnected from security: Choose a platform that treats SOC 2 as part of your overall risk management.
The best choice balances your immediate needs with long-term scalability. You don't want to re-implement your compliance program every two years, but you also can't let perfect planning prevent progress on your current audit timeline.
Also, consider pricing models that scale with your organization rather than penalizing growth.
AuditBoard delivers scalable SOC 2 compliance that grows with you
SOC 2 compliance doesn't have to drain your team or derail your priorities. The right platform turns scattered controls into connected workflows and audit panic into year-round readiness. Working with compliance experts during your initial setup can accelerate your compliance journey from months to weeks.
AuditBoard maps controls to your real processes and captures evidence as you work. Your SOC 2 controls don’t stand alone — they overlap with requirements from frameworks like ISO 27001, PCI, and HIPAA.
With the right platform, changes you make for SOC 2 flow through to your other security compliance obligations, and evidence collected for one standard can often be re-used for others. When auditors ask questions, you have complete answers ready, without managing separate systems for every framework.
Teams using AuditBoard report faster audit cycles, fewer findings, and compliance programs that improve data security. Connected workflows eliminate silos. Real-time dashboards show exactly where you stand. Evidence collection happens continuously, not just during audit season, making your SOC 2 Type 2 audit preparation seamless.
Request a demo and experience SOC 2 compliance that really works.
About the authors

Jimmy Pfleger, CISA, Kanban Certified (Agile), is a Manager of Product Solutions at AuditBoard and has over 11 years of IT Audit, Compliance & Security experience. He started his career at KPMG in the IT Advisory practice where he led external audit & assurance activities for some of the largest companies in the St. Louis area. In addition to managing the IT Internal Audit function at both Caleres & RGA, he also spent time as the Manager of Security Compliance at Express Scripts where he built and managed the SOC 2 program.
You may also like to read


GDPR compliance requirements guide: What GRC managers need to know

How Cielo became the first RPO to achieve ISO 42001 compliance in just 3.5 months

8 best compliance automation tools

GDPR compliance requirements guide: What GRC managers need to know

How Cielo became the first RPO to achieve ISO 42001 compliance in just 3.5 months
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO



