
January 14, 2026 • 22 min read
Bank regulatory compliance: How to stay ahead
New and evolving banking regulations — across capital, cyber, operational resilience, anti-money laundering, and consumer protection — are emerging as board-level demands for faster, cleaner reporting rise. Success now hinges less on memorizing regulations and regulatory standards and more on operationalizing compliance: aligning policies, controls, data, and teams in a repeatable system that scales.
The increased scrutiny can be daunting, and AI and cloud computing technologies add an additional level of complexity to the IT compliance manager’s job.
To deal with this, successful IT compliance managers at financial institutions are focusing on developing firm-wide systems that weave regulations into day-to-day workflows to operationalize compliance across teams, automate repeatable tasks, and deliver real-time insights on compliance issues to regulators and executives.
What is bank regulatory compliance?
Bank regulatory compliance is the discipline of translating compliance regulations, consumer protection laws, and supervisory expectations into repeatable processes with clear ownership, measurable controls, and evidence that stands up to examination.
Banking compliance is unique because it protects both systemic stability and consumer trust at all times, not just during an annual audit. Regulators demand continuous, verifiable adherence, making non-compliance a direct threat to an organization’s license to operate. The goal for financial institutions isn’t merely to “be compliant” on paper; it’s to make compliance with regulatory requirements observable and verifiable in day-to-day operations.
Key regulations in 2025
Banks operate under a web of overlapping regulations covering capital requirements, cybersecurity, operational resilience, fair lending, electronic fund transfer rules, and customer data protection.
Here's what IT compliance managers need to know about the major frameworks shaping bank compliance today.
Basel III
Basel III “Endgame” sets the global standard for how much capital banks hold as a cushion against losses. The current rules, called the "Endgame," focus on making the calculation of this capital more consistent and transparent. The Basel Committee for Banking Supervision (the international rulemakers) lets organizations use their standardized formulas or build their own internal models if regulators sign off.
The impact is scale-dependent: Large global banks face brutal capital requirements and stress tests. While smaller community banks under $100 billion experience minimal changes.
EU Digital Operational Resilience Act (DORA)
DORA applies to banks, insurers, investment firms, and payment providers operating in the EU. Even non-EU institutions with European customers have to comply. DORA requires ICT (Information and Communications Technology) risk governance, incident reporting, resilience testing, and oversight of critical third-party providers that examiners can trace through your systems.
IT risk and compliance platforms are essential because DORA generates documentation requirements that quickly outpaces spreadsheet management. Penalties go up to 2% of global annual turnover, or 1% of average daily turnover per day you're out of compliance.
UK Operational Resilience Requirements
The UK Financial Conduct Authority (FCA) requires banks, insurers, exchanges, investment managers, and building societies to prove they can deliver important business services within impact tolerances during severe disruptions (e.g., cyberattacks, system failure, supplier collapse, etc.).
The FCA expects ongoing proof through regular testing and monitoring. Non-compliance carries significant fines for organizations and their executives, business restrictions, and public censure that tanks market confidence.
Cybersecurity: New York State NYDFS 23 NYCRR 500
NYDFS created the cybersecurity rules most other states now try to match. If an organization operates in New York, compliance is mandatory. If not, plenty of institutions still use NYDFS as their baseline because it's become the de facto standard.
The requirements focus on concrete security measures and executive accountability. Firms must use phishing-resistant MFA (Multi-Factor Authentication) like FIDO2 keys and encrypt sensitive data across all systems. Firms must also run annual risk assessments and vulnerability scans, report major incidents within 72 hours, and place a qualified CISO in charge to oversee compliance and submit annual certifications.
Banks working on SOC 2 compliance often align it with NYDFS since both push for strong access controls and regular security testing.
Gramm-Leach-Bliley Safeguards Rule
The Gramm-Leach-Bliley Act (GLBA) instructs financial institutions to "protect the security and confidentiality of customers' nonpublic personal information." Recent amendments added a reporting requirement that doesn't give you much runway: Firms must notify the FTC (Federal Trade Commission) within 30 days if a breach hits 500 or more consumers.
When the threat landscape shifts, an organization's compliance program requires active management, compliance training, regular risk assessments, tested controls, vendor oversight, and timely program updates.
Third-Party Risk Management (US Interagency Guidance)
The OCC (Office of the Comptroller of the Currency), FDIC (Federal Deposit Insurance Corporation), and Federal Reserve published guidance on managing vendor risks that examiners now treat as requirements. The approach breaks vendor management into five stages: planning (do we need this vendor?), due diligence and onboarding (can they handle the work safely?), contracting (what security terms do we need?), monitoring (are they keeping their promises?), and termination (how do we exit without disruption?).
Examiners pay closest attention to critical vendors — the ones with access to critical systems, handling customer data, or running functions the financial institution can't operate without. When exam season hits, compliance management platforms make vendor oversight easier to demonstrate than pulling together disparate spreadsheets from various teams.
Federal Financial Institutions Examination Council (FFIEC) IT Handbook updates
The FFIEC recently refreshed the examiner procedures for Development, Acquisition & Maintenance (DA&M), underscoring change control discipline, data governance, and enterprise IT planning as exam priorities. The revised guidance elevates the need for institutions to demonstrate robust, documented processes and controls over technology risk, making IT governance a primary focus of upcoming examinations.
Sarbanes–Oxley Act of 2002 (SOX)
SOX requires that IT governance be viewed as part of financial governance, meaning systems must be secure, reliable, and auditable. The key provisions related to IT compliance are internal controls over financial reporting (ICFR), data security and access restrictions, internal audit trails and logging, change management controls, and data retention and backup across the regulatory landscape.
Banks that violate SOX provisions, and their officers, are potentially subject to harsh penalties. Financial services firms and lenders can face fines of up to $25 million per incident, threatening financial stability, and potential delisting of their stock. Officers can be fined up to $5 million and could face up to 20 years in jail.
Avoiding penalties and maintaining trust
Non-compliance hurts twice: Once when a firm pays for remediation, and again when enforcement actions restrict growth, trust, product launches, and capital distributions for years. Banks that treat compliance as continuous work instead of a quarterly scramble before exams tend to avoid this pain.
Here's how to build a system that holds up:
Clear, flexible policies
Put document requirements in plain language. structure them so you can update when rules change without rebuilding from scratch.
Connected data
Break down silos between risk, audit, compliance, and operations. When everyone works from the same information, you catch problems before regulators do.
Automation
Handle repetitive tasks like evidence collection and control testing to cut manual errors and free your team for analysis instead of administrative work.
Cross-team workflows
Ensure Risk, Audit, IT, and business owners collaborate from a shared inventory of processes and controls. Scattered ownership creates gaps examiners will find.
Documentation trails
Track who did what, when, and why. Examiners want evidence, not explanations.
We'll walk through how to build this compliance strategy in more detail below, including specific steps for risk assessments, control testing, and automation.
Challenges banks face in compliance
Two problems create most of the pain in bank compliance: regulations that won't sit still and data scattered across systems that don't talk to each other. Both drain resources and create compliance risks, but they're also fixable with the right approach.
Regulations change faster than compliance programs adapt
Your compliance program needs to absorb regulation changes without rebuilding from scratch every time.
But the problem isn't tracking regulatory updates — it's operationalizing them fast enough to stay ahead of exams. When your policies, controls, and testing procedures are rigid or tied to specific regulatory language, every change triggers a cascading update across documents, workflows, and training.
How to handle this: Build your compliance framework around principles rather than specific rule text. Map controls to multiple regulations, so when one changes, you update the mapping once and see where else it ripples. Use flexible policy templates that separate core requirements from regulatory citations.
Data silos turn routine tasks into integration projects
Most banks still run compliance from fragmented systems: policies in one tool, risk assessments in another, control testing in spreadsheets, issues in ticketing systems, and evidence scattered across shared drives.
This fragmentation creates three specific problems. First, you can't see how risks connect across the organization. Second, every exam prep cycle wastes weeks copying data between systems and fixing inconsistencies instead of analyzing actual risk. Third, when controls or requirements change, the updates don't propagate automatically, so gaps open up between what you think you're monitoring and what you're actually tracking.
How to fix this: Centralize your compliance data in a connected platform where policies, risks, controls, tests, and evidence live together. When IT updates a security control, everyone relying on that control — audit, risk, compliance, third-party oversight — sees the change immediately.
Core elements of a modern compliance program
A sustainable program is simple to describe and hard to execute. Clearly, such a program involves policies and procedures, risk assessments, controls and testing, issues and remediation, reporting, and governance. The differentiator in 2025 is the connective tissue that keeps these elements aligned as rules change.
Policies and procedures: From documents to operational playbooks
Policies tell you what to do. Procedures show you how. The difference matters when examiners show up asking for evidence that your controls work as described.
Most banks still manage policies as static PDFs in a document repository. Someone reviews them annually, updates version numbers, and emails acknowledgment requests. That approach fails the moment regulations shift or an exam reveals gaps.
What works better: Establish role-based workflows that assign specific tasks to specific people at specific intervals and track completion automatically. Instead of a policy stating "perform quarterly access reviews," the workflow routes tasks to system owners each quarter, reminds them if they're late, requires evidence uploads, and escalates to managers when deadlines pass.
For third-party risk, the workflow might trigger when procurement flags a new vendor. Risk management gets an automatic task to tier the vendor. High-risk vendors route due diligence tasks to security, legal, and compliance. After contract signing, the system schedules ongoing monitoring tasks and assigns them to relationship owners.
Risk assessments and control testing: Ensuring coverage
With DORA live, UK operational resilience monitoring ongoing, and US cybersecurity risks evolving constantly, banks need continuous assessment cadences that catch problems before examiners do.
What you need for effective risk assessments:
- Rolling assessment schedules: Perform quarterly updates for high-change areas like cloud security, data protection, and third-party relationships instead of once-a-year exercises.
- Connected risk-to-control mapping: Link each risk to specific controls and regulations so you see coverage gaps when rules change.
- Change integration: Tie risk assessments to your change management process so new systems, vendors, or processes trigger risk reviews automatically.
- Risk-based testing frequency: Test critical controls (privileged access, payment system resilience, vendor concentration) more often than low-risk controls.
Controls that need more attention:
Your enterprise-level controls deserve higher testing frequency and independent validation. Focus extra scrutiny on:
- Privileged access management in cloud environments
- Payment service and critical system resilience
- Vendor concentration and critical third-party dependencies
- Data protection controls covering customer information
- Segregation of duties in financial systems under SOX compliance
Document your control-to-risk-to-regulation mappings so when Basel operational risk guidance shifts or DORA testing requirements get clarified, you immediately see where coverage gaps exist.
How to build a sustainable compliance strategy
Sustainable compliance programs don't just check boxes — they make regulatory requirements part of how work gets done. This means automating repetitive tasks so your team focuses on analysis instead of data collection and breaking down silos so everyone works from the same source of truth.
Using automation — improving efficiency and reducing errors
Automate evidence collection and control monitoring to eliminate manual errors and speed up compliance cycles. Here's where to start:
Set up automated evidence collection. Script the collection of system configurations, user lists, encryption settings, backup logs, and vulnerability scan outputs. But don’t stop there — tie this influx of reliable evidence to specific controls to run continuous tests, allowing teams to evaluate control gaps and automatically open issues for remediation.
Implement AI-assisted alert triage. Use AI to filter financial crimes and fraud monitoring alerts for suspicious activity and cut false positives. The technology routes higher-risk items to human analysts faster while reducing the noise from routine flags. Just make sure you document data sources, test for bias, and monitor performance so you can explain decisions to supervisors.
Automate control testing schedules. For controls tied to SOC 2 compliance or SOX, set up testing to run automatically rather than relying on calendar reminders. When controls fail, the system should notify owners immediately and track remediation through closure.
Cross-team collaboration — ensuring risk, audit, and compliance alignment
Get risk, audit, IT, and business owners working from the same inventory of processes, risks, and controls. Scattered ownership creates gaps that examiners will find.
Build a shared control library. Map each control to multiple frameworks (Basel operational risk, DORA articles, NYDFS sections, FFIEC booklets). When a rule changes, update the mapping once and the change propagates everywhere.
Link issues to remediation plans. When testing reveals control failures, create remediation tasks with clear owners, due dates, and status tracking that rolls up to governance dashboards. Make sure status updates are visible to all stakeholders — audit, risk, compliance, and business owners — so nobody's working from outdated information.
Integrate third-party risk into workflows. The interagency TPRM (Third-Party Risk Management) guidance expects life-cycle rigor from planning through termination. In practice, this means procurement, security, legal, and first-line teams use a single workflow with vendor tiering, due diligence artifacts, contractual controls, and continuous monitoring captured centrally.
How AuditBoard supports bank compliance
The gaps above are integration problems — not single-control problems. A connected platform helps unify policy mappings, risks, controls, tests, and evidence, with workflows that traverse teams. AuditBoard’s compliance capabilities center on:
Unified risk and compliance mapping
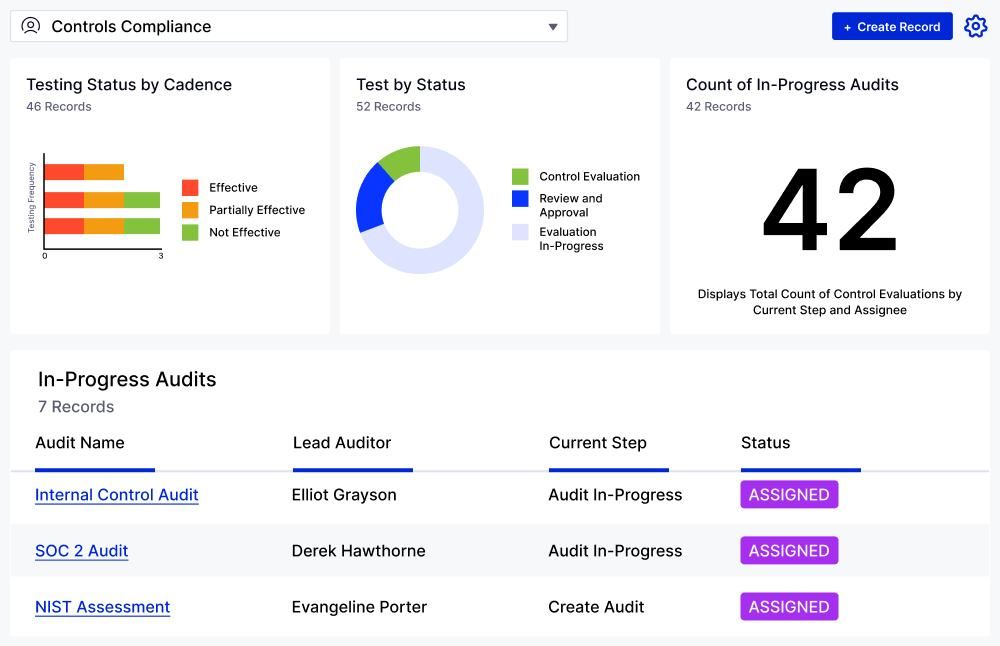
AuditBoard can streamline processes and allows one control to be mapped to multiple frameworks (e.g., DORA Article 10, NYDFS 500.7, FFIEC DA&M topics). When a rule changes, you update once and see downstream impacts across testing and reporting.
AuditBoard also provides cross-functional workflows. Issues raised in testing generate remediation tasks for owners in IT or bank operations, and the status is visible to audit, risk, and compliance — reducing email-driven silos. Brett Schimanski, EVP Senior Director, Enterprise Risk Management, Stellar Bank, says:
“AuditBoard has been invaluable as a streamlined, automated change management program as we move forward. Now, we’re working on risk assessments. We have our risk register, we’re conducting risk mapping, and are focusing on connected risk as we continue to grow and develop.”
Real-time reporting
AuditBoard dashboards highlight coverage, exceptions, and aging actions, enabling boards and exam teams to see status without manual compilation.
The benefit isn’t merely speed. It’s repeatability under change — exactly what the current regulatory environment demands, and how AuditBoard provides regulators and executives with insights.
To learn how you can meet these complex regulatory requirements with less effort using AuditBoard’s connected platform, request a demo today.
You may also like to read


GDPR compliance requirements guide: What GRC managers need to know

How Cielo became the first RPO to achieve ISO 42001 compliance in just 3.5 months

8 best compliance automation tools

GDPR compliance requirements guide: What GRC managers need to know

How Cielo became the first RPO to achieve ISO 42001 compliance in just 3.5 months
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO



