
May 16, 2023 • 33 min read
7 Types of Information Security Incidents and How to Respond

Vice Vicente
Information security gets a lot of press nowadays, and with good reason — attackers and cybercriminals threaten businesses, public institutions, governments, and even individuals. Formally, information security or “InfoSec” is defined by the National Institute of Standards and Technology (NIST) as, “the protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide confidentiality, integrity, and availability.” This encompasses the systems, processes, tools, controls, and policies put in place to perform information security and protect a company’s sensitive information. Implementing and improving information security capabilities safeguards organizations from cybercrime and other risks in the information technology space. And crucial to any information security program is information security incident management, also known as incident response management (IRM). What is incident management, and why is it so important? Read on, and we’ll take you through building an incident response function, how to improve it, and seven common types of security incidents to expect.
What Is an Information Security Incident?
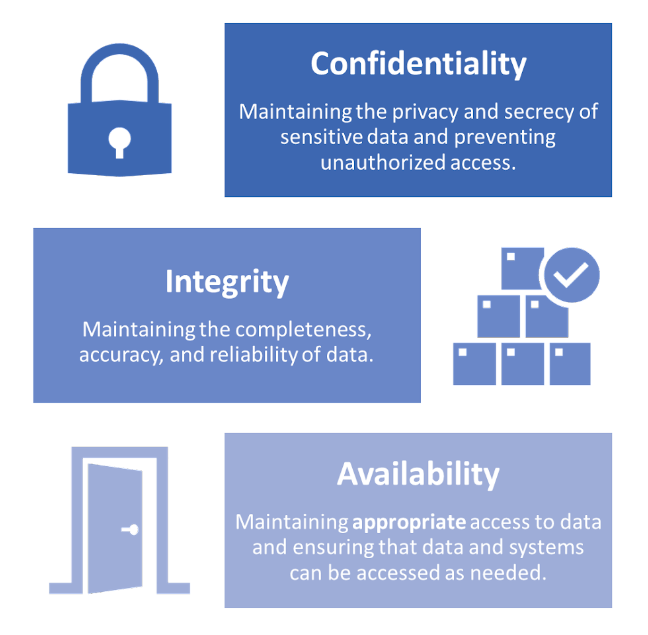
An information security incident is any occurrence that threatens the confidentiality, integrity, or availability of information systems and sensitive data. These three principles — confidentiality, integrity, and availability — form the CIA triad and provide guiding focal points for developing and improving an information security program. Unauthorized access to sensitive data would constitute a threat to confidentiality, while improper or incorrect modifications to data represent a threat to information integrity. System outages compromise information availability. Any one of these events would be classified as an incident due to their impact on the confidentiality, integrity, or availability of information.
Image: CIA Triad
Security Events
A security event typically ** ** preempts a security incident. Events are simply occurrences that are detected or flagged for triage. Some events that an organization might detect could be a spike in traffic to a website; an unusual access occurrence; or even a strange email. Some events are just that — things that happen that require no further action. For example, an information security team might detect unusual access to a system. After further analysis, the team determines that access was approved ahead of time to perform maintenance. In this case, that event would be a valid occurrence and require no further action.
Some events will escalate to the level of an incident. Events that rise to the level of an incident must pose some kind of threat to the CIA triad, or fall into another category specified by the business. An event can be categorized as an incident through manual triage — that is, a person analyzes the event and decides that it rises to the level of an incident. Incidents can also be automatically generated based on thresholds defined by the business. Many security tools now provide the option of notifying personnel in the event of anomalous activity, and can even generate and auto-populate certain fields in an incident response form or ticket. Tagging incidents with a priority or severity ranking allows teams to strategize and deploy resources accordingly.
Organizations have some leeway in defining what an event versus an incident should be — these definitions should, of course, be documented in a policy and have clear, actionable thresholds for differentiating between incidents and events such that responders can quickly and effectively make decisions when triaging.
In some cases, information security incidents arise from potential threats, not just actualized ones. This means the information security incident doesn’t have to be successful in order for it to be a problematic security threat. A cybercriminal declaring a future cyberattack on an organization would certainly qualify as a security incident, even if nothing has happened yet. Even an unsuccessful security incident requires procedures for both tracing and tracking the incident, and initiatives to limit or prevent future threats.
Incident management processes and policies provide companies with the tools and methods they need to respond to an incident once it has been detected.
Incidents and Data Breaches: What is the Difference?
While data breaches are incidents, not all incidents are data breaches. The goal of malicious activity directed toward an organization’s information security isn’t always to exfiltrate data or cause information leakage. Cybercriminals have other insidious aims, like compromising service providers to cause supply chain disruptions or holding information systems for ransom. Insider threats can propagate fraud or falsify data. Some incidents, like unauthorized access or deploying untested changes, may not be intentional, yet require adequate response. Likewise, something like a system outage would not necessarily result in a data breach, but would still be classified and treated as an incident. In short, there are many other types of security incidents beyond a data breach.
What Are the Components of Information Security?
Within the discipline of InfoSec, there are many types of information security methodologies, best practices, and approaches. Developing an effective information security program involves balancing all of these different approaches and topics to implement the right mix of processes, controls, and tools to protect your organization.
There are some commonalities between different InfoSec practices, such as making sure employees are properly trained and using protected devices, as well as ensuring your company has a proper incident response plan.
Key components of information security include application security (AppSec), cloud security, identity and access management (IAM), network security, infrastructure security, physical security, and incident response. Every company has a tailored technology stack, which calls for a personalized approach to information security. Heavily cloud-leveraged organizations might prioritize cloud security over other components; companies with physical data centers need to set up physical as well as cybersecurity safeguards.
Information Security versus Cybersecurity
You may wonder what the difference between information security and cybersecurity is. NIST defines cybersecurity as, “the prevention of damage to, protection of, and restoration of computers, electronic communication systems, electronic communications services, wire communication, and electronic communication, including information contained therein to ensure its availability, integrity, authentication, confidentiality, and nonrepudiation.” The two concepts have significant overlap and are often used interchangeably. However, while cybersecurity specifies a scope of electronic communications and computers, information security has a broader purview and specifies a scope of all information and information systems, including paper and physical assets.
Application Security
Application security involves enhancing security at the application layer to prevent data breaches and mitigate security vulnerabilities. An application is any software or software package that has specific functionality, whether it’s installed on your machine, served on the web, or downloaded on your phone — like Microsoft Word, Photoshop, or even Instagram. Application security takes into account the code comprising the solution, configurations, and even authentication to the program. Common vulnerabilities are found in the user authentication processes (e.g. logins), which can result in easy access for a data breach. As development, security, and operations integrate into DevSecOps, security teams and engineers should consider the potential for exposure in the libraries they are using, and regularly scan the code base for vulnerabilities and dependencies.
Cloud Security
Cloud security encompasses securing data across applications, functions, platforms, , and infrastructure within a cloud environment. The cloud is complicated, but there are some fundamentals pertinent to information security. As more companies move some or all of their computing, data storage, data processing, and/or operations to cloud-based solutions, the importance of enforcing strong cloud security controls and practices grows commensurately. Luckily, many third-party cloud service providers have built-in security tools, dashboards, and logs to support an organization’s InfoSec program. Although cloud service providers (CSPs) provide many services for information security, it’s up to the organization to enable, configure, and maintain those services and policies that apply to their cloud environment.
Network Security
Network security involves securing an organization’s perimeter, intranet, and wireless networks, as well as the equipment supporting it. Network security teams might be responsible for configuring and changing firewall rules, managing installing routers, and even securing new internal networks when needed.
Infrastructure Security
Infrastructure security includes the safeguarding of databases and operating systems that underlie traditional applications. This can include restricting access to administrative or privileged accounts; monitoring account activity; regular scans; and applying patches.
Identity and Access Management (IAM)
Identity and access management (IAM) involves the identity and authentication structure of the organization, as well as access management controls. This area of information security deals with how company personnel are managed electronically, including their user IDs, single sign-on configurations, and what information they have access to. Privileged or administrative access also falls under this umbrella. Best practices dictate that personnel should receive the least possible access (the principle of least privilege) needed to complete their role or function (role-based access control, or RBAC). Password and multi-factor authentication controls fall into this category.
Physical Security
Regularly overlooked, physical security is still an information security consideration, especially if your organization maintains paper records and physical data centers, or if your organization needs to protect physical systems, equipment, or devices. In these scenarios, information security teams should consider document disposal practices, locks, surveillance, and access logs.
Incident Response
Even the best information security programs will encounter some kind of incident. A critical component of effective InfoSec is how quickly and effectively your organization reacts to an incident. Allowing incidents to persist or go without mitigation means that the organization remains at risk to that incident, and those like it. To operate an effective incident response function, companies, and teams need to understand their greatest risks and implement controls and processes to limit or prevent those risks. Once the risks are understood, incident response teams (IRTs) can prepare incident response plans and conduct exercises to prepare for each risk scenario.
What Are the Different Types of Security Attacks and Attack Vectors?
The types of information security incidents and attack vectors cybercriminals cause and use vary in sophistication levels from simple to complex. Equipment theft, such as a stolen laptop or USB drive, is a security attack vector. Unauthorized access to and use of — or changes to — software or data is a cybersecurity incident. Compromised user accounts and Distributed Denial-of-Service attacks (or DDoS attacks) are also cybersecurity incidents. These are some common types of attack vectors used to commit a security breach: phishing, brute-force attacks, malware, SQL injections, cross-site scripting, man-in-the-middle attacks, and DDoS attacks.
Phishing and Social Engineering
Phishing and social engineering continue to be common cybercrimes, costing the US more than $52 million. Phishing attacks rely on human error, so employee training is critical to preventing a security incident. Blanket phishing attacks have evolved into spear-phishing or social engineering attacks, now conducted over the phone and through text messages, not only emails.. Employees need to be able to recognize phishing emails, as well as text and phone-based fraud, and avoid clicking on questionable links or downloading anything suspicious. In general, everyone should avoid sharing their sensitive information and credentials via email, over text, or on the phone without verifying the security of the transmission and the identity of the recipient.
Brute-Force Attacks
In these attacks, hackers use software to repeatedly and systematically attempt password combinations until they find one that works. Brute-force attacks are surprisingly effective, perhaps due to algorithmic progress, or the continued prevalence of weak passwords. Enabling multi-factor authentication (MFA) adds another layer of authentication security. Lengthier passwords are tougher to crack.
Malware
Malicious software, aka malware, infects devices without users knowing it’s there. Examples include Trojan horses, spyware, ransomware, and viruses. In 2021, Colonial Pipeline, the biggest oil supplier in the US, got caught up in a ransomware incident, lost days of business, and ultimately paid off their attackers approximately $5 million in Bitcoin. According to Bloomberg, the hackers got into the system via a leaked password on an old account that allowed employees to access company servers remotely through a VPN (virtual private network), and it did not require two-factor or multi-factor authentication. Once the hackers were in, they installed the malware, encrypted the company’s data, and demanded a ransom.
SQL Injections
Structured Query Language (SQL) injections occur when a hacker inserts malicious code into a user data input (like a text field)to manipulate or read a company’s database. The goal is to access private company data, such as customer information and credit card numbers.
Cross-Site Scripting
Cross-Site Scripting (XSS) attacks, like SQL Injections, are a type of injection. In this case, malicious scripts are added to trusted sites. The attacker can then send malicious code via a browser-side script to the end user. These types of attacks can redirect victims to another, potentially malicious site, or give private data to the hacker.
Man-in-the-Middle Attacks (MITM)
Hackers position themselves as middlemen between users and eavesdrop, intercept, and/or manipulate communication between two parties. This often occurs on unsecured networks, like public WiFi.
Distributed Denial-of-Service (DDoS) Attacks
A DDoS attack overwhelms a website with a flood of traffic using bots in an attempt to crash the service and deny access to real users. Sometimes hackers will initiate a DDoS attack to test a system’s integrity, especially when they manage a large consumer-facing website.
How Can I Detect Security Incidents?
There are different ways to detect if your company is under threat of a critical security incident. Different types of information security incidents will have markers for discovery.
Some methods for finding indicators of a current or future incident include:
- Look for traffic anomalies, attempts to access accounts without permission, excessive use, and access of suspicious files — this can be indicative of malicious activity.
- Servers tend to have a relatively stable and consistent volume of traffic, subject to business calendar needs and resultant fluctuations. If a company experiences an unusual traffic increase, it should look into the cause and look out for an attack.
- Unusual traffic or outages on an organization’s network, especially when it’s unexpected, can be a sign of unauthorized access.
- Employees are a main entry point for an InfoSec compromise, so restrict access appropriately and install endpoint security on company assets.
- Implement tested security tools and solutions to provide your information security program with enhanced detection and response capabilities.
- Take threats seriously — initiate your incident response protocol if your organization is being blackmailed, threatened with a cyberattack, or held for ransom.
Seven Common Information Security Incident Types and How to Respond
There are many types of information security incidents and attack vectors, and here we’ve selected seven common types to provide you with a starting point for developing an incident response plan and incident management program. The common security incident types we’ll be discussing are:
- Unauthorized Access
- Malware Infection
- Distributed Denial of Service (DDoS) Attack
- Internal Security Breaches and Insider Threats
- Security Misconfigurations
- Cryptography and Data Security
- Advanced Persistent Threats (APTs)
Many of these are derived from the OWASP Top Ten, a list of the top risks to web applications.
1. Unauthorized Access
Unauthorized access via brute-force attacks, phishing attacks, or other password exploits are frequently used to steal sensitive information. Furthermore, OWASP identified inadequate access controlas the number one risk to web application security in 2021 — entailing vulnerabilities that make it easier for hackers and attackers to obtain improper, unauthorized access. Ramping up authentication controls, encrypting sensitive data, boosting password requirements, and application security, as well as requiring or enforcing multi-factor authentication can help prevent these types of incidents.
Once unauthorized access is detected and identified as an incident, the IRT must come up with a plan for isolating or containing the attack, including disabling accounts if necessary. Investigating this type of incident is just as crucial as responding, and any security gaps that resulted in the unauthorized access event should be prioritized for remediation. The investigation and analysis process needs to account for the activity performed through the inappropriate access, and determine if further action is necessary, such as if the outcome of the incident was likely to result in a data breach.
2. Malware Infection
Malware can be very damaging. In fact, ransomware is malware. Getting hit with a successful malware attack can take out a company’s operations, supply chain, or network, and can have an impact on the company’s bottom line. To protect the organization from malware, businesses should install anti-virus and anti-malware (AV/AM) tools on critical infrastructure and endpoints, scanning systems frequently for indications of compromise. Signs of malware include unusual system activity, like a sudden loss of memory space, unusually slow speeds, repeated crashes or freezes, and unexpected pop-up ads.
If an infection cannot be prevented, the IRT should be prepared to contain the malware spread as much as possible, then proceed to eradication, as outlined in NIST’s Computer Incident Handling Guide. Once the IRT is confident that malware has been removed from systems, the focus should shift to safe recovery.
3. DDoS Attacks
Distributed Denial-of-Service attacks can be detected by the flood of traffic hitting your site. Combat them by configuring your servers to fight HTTP flood requests and coordinate with your ISP to block sources when an attack occurs. Also, beware of a DDoS diversion attack, which is when an attack is initiated in order to distract security teams from a more serious malicious attempt. Configuring firewalls, routers, and servers can block or mitigate future DDoS attacks, as can implementing a web access firewall (WAF). By identifying and blocking IPs involved in the DDoS attack, IRTs can respond in real time.
4. Internal Security Breaches and Insider Threats
Unfortunately, sometimes, employees abuse their access to information. Employees have considerable access to sensitive data, systems, and information, and can use that access for less than benign purposes. Disgruntled employees are capable of doing considerable damage. To limit insider threats, maintain role-based and least-privilege access control for employees. Configure systems to record privileged information accessed, and set notifications for unauthorized attempts to access data in restricted areas. Lastly, make sure all systems are monitored for anomalous activity.
Once an insider threat has been identified, the IRT should consult management and the Human Resources team on the next steps, while keeping information about the incident confidential. The ramifications of an insider threat can extend beyond information security, and require discretion. Employees should be encouraged and trained on using internal whistleblower systems to report unethical, improper, or inappropriate behavior.
5. Security Misconfigurations
Another one from the OWASP Top Ten, and with over 200,000 occurrences in 2021, security misconfigurations leave the door open for successful cyberattacks and are more common than you think. These configurations can range from out-of-date infrastructure to unchanged defaults, to missing values for security parameters. Companies can avoid security misconfigurations and the risks and vulnerabilities they bring by establishing and maintaining a regular infrastructure patching frequency and server hardening standard. Using configuration management technology that orchestrates settings across a fleet of infrastructure can help businesses with a large server footprint.
Upon detecting and analyzing security misconfigurations, the IRT’s responsibility is to track those erroneous configurations to remediation, working with the necessary teams to ensure that security variables are set and best practice security settings are in place. Any potential exploits of these vulnerabilities should be investigated until the IRT is confident that no further compromise has taken place.
6. Cryptography and Data Security
With so many ways of moving data and transmitting information, it can be easy to forget one mechanism or another. Failure to adequately secure data and apply up-to-date cryptography and encryption practices is another major area of vulnerability for organizations and a risk that IRTs will have to prepare for. Since there are so many mediums for moving data, one method companies can use to prevent the exploitation of weak data security is by establishing classifications and clear encryption procedures for different types of data, as well as a regular cadence for reviewing encryption standards. Organizations should outline in policy what file transfer methods are acceptable (no FTP!) and what encryption and cryptography standards are acceptable.
In the event that data is decrypted, a data breach occurs, or an insecure algorithm is used for cryptography, the IRT should follow their organization’s requirements for notification and communication, then proceed to remediation.
7. Advanced Persistent Threat
An Advanced Persistent Threat (APT) is a prolonged and targeted attack. The hacker gains access to a network and remains undetected for an extended amount of time. The hacker will then frequently monitor network activity and steal data rather than cause damage to the network. It’s a prolonged heist where the hacker slyly goes undetected, stealing privileged information. Monitoring incoming and outgoing traffic can help prevent hackers from extracting sensitive information. Firewalls also help protect network information and can prevent SQL injection attacks, which are often used in the early phase of an APT attack.
Real-Life Examples of Information Security Incidents
There have been many high-profile information security incidents involving major corporations that end up having a significant effect on regular folks; and an uncountable number of regular folks who have found themselves the victim of cybercrime.. In addition to the Colonial Pipeline ransomware exploitation, both Alibaba and LinkedIn have experienced large data breaches in recent years. In 2019,Alibaba experienced a leak of more than 1 billion units of user data when a developer scraped customer info, including user names and cellphone numbers from their Chinese shopping site, Taobao. The information did not end up on the black market, but after the eight-month-long theft was discovered, the culprits were caught and ultimately fined and sent to prison. It was in June 2021 that the theft of LinkedIn information for 700 million users — representing approximately 93% of their user base — was exposed when a hacker bundled data for sale on the black market. The hacker scraped data using the site’s API and captured information, which included email addresses, phone numbers, geolocation information, and other social media details that could lead to follow-up social engineering attacks.
Get Ahead of Information Security Incidents Today
Information security is incredibly important to modern businesses. The increase in InfoSec incidents, cyberattack vectors, and significant data security threats means businesses are more at risk of information security attacks than ever before. Companies need to monitor the data security landscape and be prepared to respond to threats when they occur. Prioritizing information security and integrating it with the culture and operations of an organization goes a long way in protecting from and preventing information security threats.
It’s critical to establish an InfoSec incident response plan to ensure your company is poised and ready to combat all types of information security incidents. Having the right technology can help — get started with AuditBoard’s information securitycompliance management software today, and prepare for the threats of tomorrow!
Frequently Asked Questions About Security Incidents
What is an information security incident?
An information security incident is any occurrence that threatens the confidentiality, integrity, or availability of information systems and sensitive data.
What are the types of information security?
Key components of information security include application security (AppSec), cloud security, identity and access management (IAM), network security, infrastructure security, physical security, and incident response.
What are the different types of security attacks?
These are some of the common types of attack vectors used to commit a security breach: phishing, brute-force attacks, malware, SQL injections, cross-site scripting, man-in-the-middle attacks, and DDoS attacks.
How can I detect security incidents?
Some methods for finding indicators of a current or future incident include:
- Look for traffic anomalies, attempts to access accounts without permission, excessive use, and access of suspicious files — this can be indicative of malicious activity.
- Servers tend to have a relatively stable and consistent volume of traffic, subject to business calendar needs and resultant fluctuations. If a company experiences an unusual traffic increase, it should look into the cause and look out for an attack.
- Unusual traffic or outages on an organization’s network, especially when it’s unexpected, can be a sign of unauthorized access.
- Employees are a main entry point for an InfoSec compromise, so restrict access appropriately and install endpoint security on company assets.
- Implement tested security tools and solutions to provide your information security program with enhanced detection and response capabilities.
Take threats seriously — initiate your incident response protocol if your organization is being blackmailed, threatened with a cyberattack, or held for ransom.
About the authors

Vice Vicente started their career at EY and has spent the past 10 years in the IT compliance, risk management, and cybersecurity space. Vice has served, audited, or consulted for over 120 clients, implementing security and compliance programs and technologies, performing engagements around SOX 404, SOC 1, SOC 2, PCI DSS, and HIPAA, and guiding companies through security and compliance readiness. Connect with Vice on LinkedIn.
You may also like to read


How AI maturity impacts risk, speed, and strategy

Mind your business: The real secret to career growth

A GRC implementation guide for faster adoption and ROI

How AI maturity impacts risk, speed, and strategy

Mind your business: The real secret to career growth
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO



