
May 2, 2024 • 23 min read
Third-Party Risk Management 101: Guiding Principles

Richard Marcus
Do your third-party risk management (TPRM) policies and processes provide adequate protection against third-party risk? Today, many organizations are refocusing on the importance of effective third-party risk management due to third-party security and data breaches that have dominated the headlines. SolarWinds, Kaseya, Accellion, Microsoft, and Volkswagen have all been affected by third-party breaches that threatened data and information security — and posed regulatory, financial, and reputational risks.
However, adoption of third-party services continues to rise, as Deloitte reported in 2022 that 73% of surveyed organizations “have a moderate to high level of dependence on CSPs.” Despite this, most organizations are still struggling to get TPRM right. A 2021 AuditBoard survey of 800+ risk and compliance professionals across North America found nearly 37% of respondents rated their TPRM maturity as either nonexistent or simply reactive.
There is no better time than now to strengthen your third-party risk management practices. One helpful resource for doing so is Effective Third-Party Risk Management**: Key Tactics and Success Factors, a new guide exploring key third-party risk management principles, as well as practical tips for building a successful TPRM program. Read on for an overview that introduces the fundamentals of third-party risk management, then download your free copy of our full guide. What is Third-Party Risk Management?
TPRM programs are designed to provide discipline, structure, and oversight to guide the plans, policies, and processes by which your organization:
- Identifies and categorizes the third-parties you engage.
- Understands and prioritizes the risks presented by the third-parties.
- Establishes and enforces key controls for mitigating those risks.
- Performs monitoring that tracks and regularly reassesses third-party relationships and risk exposures.
- Responds to real-time issues, and communicates TPRM awareness and accountability throughout the organization.
Third-party risk management encompasses suppliers, vendors, contractors, managed service providers, and cloud service providers — essentially, any external entity from which an organization procures products, materials, or services. Known interchangeably as Vendor Risk Management (VRM) or Supply Chain Risk Management (SCRM), TPRM is considered a broader term that also incorporates managing the digital supply chain.
An organization’s third-party risk management function aims to address risks that come with forming business relationships with third-party vendors and service providers, and keep risks at an acceptable level for the organization. These risks run the gamut, from vulnerabilities in third-party services that could carry cybersecurity risk, to compliance risks associated with poor third-party management, to operational risks that could arise from supplier delays or provider outages.
TLDR
Assessing third-party risks involves evaluating potential vulnerabilities and security gaps posed by external partners, suppliers, or service providers that have access to your organization’s sensitive data or systems. It includes identifying risks, assessing their impact, and implementing measures to mitigate them effectively. Regular monitoring and audits are essential to ensure ongoing security and compliance.
What are the Guiding Principles of Third-Party Risk Management?
TPRM programs vary based on the size, scope, resource and budget constraints, regulatory requirements, and risk profiles of the organizations for which they’re built. One size does not fit all — but all programs share certain guiding principles.
Typically, TPRM programs:
- Are cyclical. As new third parties enter the equation and existing relationships evolve, you should periodically revisit third-parties’ risk categorization, assessment, issue management, reporting, and continuous monitoring.
- Occur against the backdrop of your organization’s enterprise and cyber risk assessment(s). As your risk profile, exposures, and prioritization evolve, so too must your TPRM program.
- Are best built around a culture of accountability. TPRM responsibilities are typically shared across a range of functions and business units. Set the tone that everyone has an important role to play in managing the risks presented by the third-parties they engage with.
A third-party risk management program is part of a larger, organization-wide set of risk assessments, but follows many of the same principles as other types of risk management systems. The cycle of third-party risk management begins with initial third-party identification and discovery, which involves cataloging and inventorying all vendors in your organization’s environment. You may begin cataloging with a simple spreadsheet or utilize Audit Board TPRM to keep it organized from the ground up. The entire process should be built around a culture of accountability in which everyone is aware of third-party risks. Once third-parties are identified, each third-party must undergo risk categorization and risk assessment or analysis. During risk categorization and assessment, each vendor is evaluated and examined to understand the risks associated, and the impact to the business and likelihood of those risks occurring.
Any open risks or gaps that come out of the previous steps of third-party discovery, risk categorization, and risk assessment should then be treated and managed. Any issues that arise throughout the third-party risk management lifecycle should be reported and tracked to remediation or completion. In order to ensure that the program continues to operate optimally, risks are updated and addressed, and issues are resolved, a third-party risk management process must incorporate continuous monitoring, and improve based on the results of monitoring, with all the support from the internal stakeholders.
Image: Third-Party Risk Management Program Overview
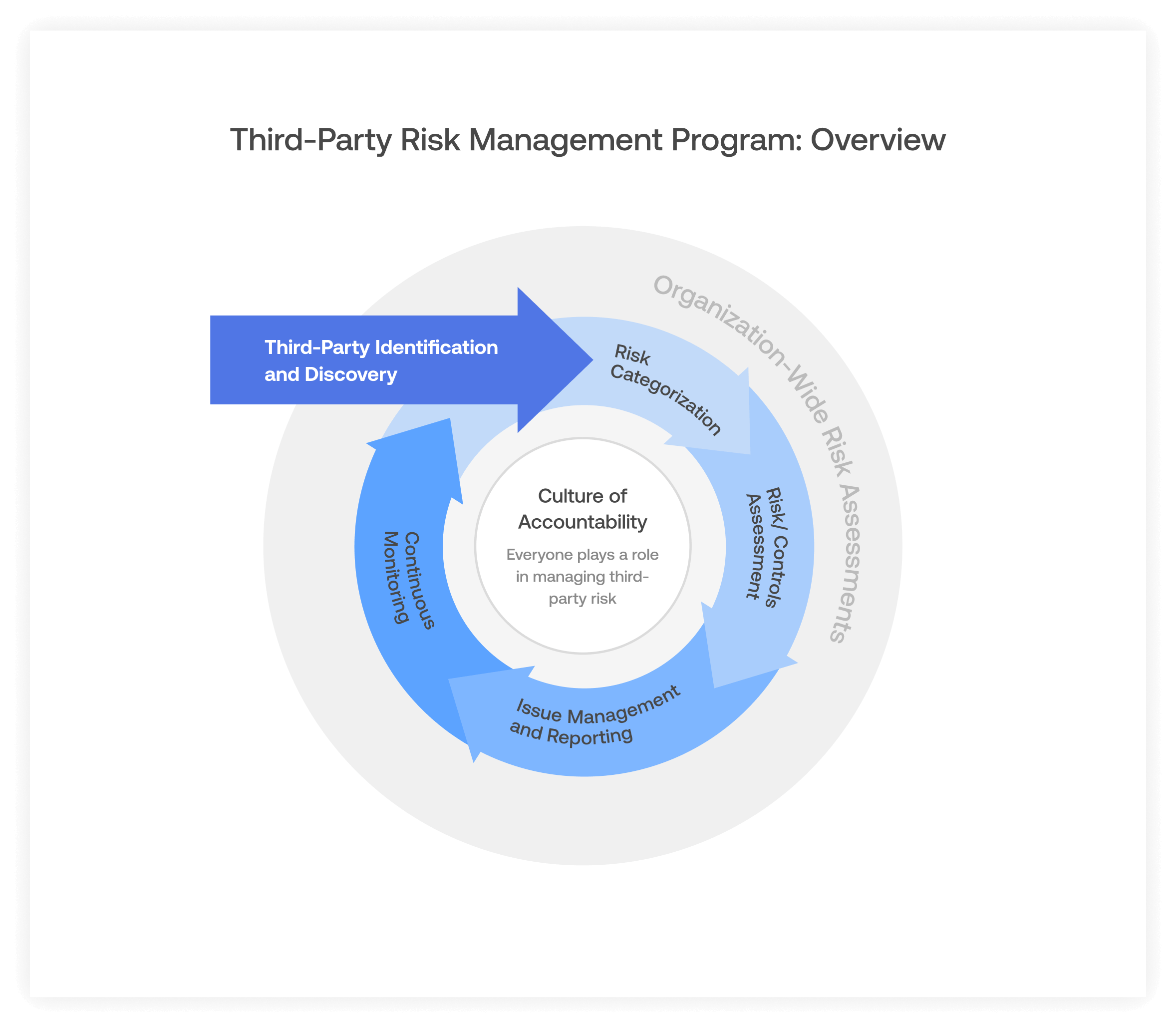
What are Common TPRM Program Components?
Third-party risk management policies and procedures are usually built out around the selection, onboarding, maintenance and ongoing monitoring, and offboarding of third-party suppliers or vendors. After your organization has developed and designed a TPRM workflow, it’s usually simple to streamline that process and create templates that apply to common due diligence and procurement scenarios.
Third-Party Selection and Due Diligence
Once a stakeholder or the procurement team has received business approval to start the procurement process and contract with a third-party for some purpose, the third-party or new vendor selection workflow begins. There are countless types of third-party providers and services out there, designed to provide solutions for almost any business problem you can think of. In mature procurement processes that are mindful of third-party risks, some enterprises have established a common benchmark or baseline for vendor selection. This baseline may require third-parties to have some kind of cybersecurity certification or attestation, like ISO 27001 or SOC 2; or have certain industry standards in place, like a defined risk management process or GDPR-compliant privacy controls.
In addition to these enterprise-wide “table stakes,” stakeholders should come up with the attributes and criteria they need from a third-party. Breaking these criteria out into “Must Haves,” “Want to Haves,” and “Non-Critical” features and then scoring each vendor against the same benchmarks allows stakeholders to compare solutions equitably.
As the field of potential third-parties narrows, your organization may want to send candidates a due diligence questionnaire such as SIG (Standardized Information Gathering) that evaluates vendors’ security posture, business continuity measures, and governance further.
Third-Party Onboarding
Upon selecting a third-party vendor and completing all due diligence and contractual bona fides, a good TPRM program will move the new vendor into the onboarding phase. This step may involve working directly with the third-party, on-site or otherwise, to install or integrate systems, coordinate shipments, define the terms of the outsourcing project, and kick off the operational side of the business relationship.
During this part of the third-party risk management lifecycle, your organization should conduct a formally documented third-party risk assessment, alternatively known as a vendor risk assessment. This will begin with the completed SIG questionnaire previously sent to the vendor. A risk assessment should be conducted on the responses by the vendor. Also, as a part of this assessment, the team should evaluate the role of the new vendor in the company’s overall third-party ecosystem, and the level of risk it poses. The documentation should reflect whether the third-party poses any financial risk or strategic risk to the organization, and the risk mitigation steps in place to address those areas. The vendor risk assessment should also consider whether any fourth-parties are involved, and if they need to be assessed for inherent risk. If the third-party has any control or gap remediation to perform due to findings that arose from due diligence, that should be noted as well. Finally, every third-party your organization contracts with should receive a criticality rating based on their importance to your organization. A high risk vendor would be one whose outage would have a severe impact on your organization’s ability to continue operations, while a low risk vendor would have little impact on your organization’s operations.
All of this documentation about third-party suppliers and providers, along with their corresponding criticality ratings should be retained in a central third-party inventory for ease of reference and update.
Third-Party Maintenance and Ongoing Monitoring
As the relationships between your organization and various third-parties in its ecosystem continue, certain maintenance and monitoring steps help keep operations moving smoothly. Foremost, each third-party relationship should have a designated owner or accountable person who is responsible for maintaining the vendor relationship, holding vendor contact information, and managing the terms of the contract. Third-party relationships differ from one vendor to the next — some may provide your organization with a designated customer support or success team that provides supplemental services, while others take an off-the-shelf approach. Keeping lines of communication open and clear between your organization and its third-parties is a major, but often overlooked component of effective third-party risk management.
Monitoring third-parties is also important. Ensuring that contract terms are being fulfilled and that contractors or providers are performing as expected will help companies glean the most value from their third-party relationships. Using automation and monitoring software to analyze data and measure third-party execution can streamline the process of ongoing monitoring.
Periodic reviews are a best practice and major compliance component of third-party risk management. High-risk vendors should have their vendor risk assessments renewed at least annually; medium-risk vendors should be reviewed every other year; and low risk vendors should be reviewed every three years. In some high risk vendor cases, these assessments can be ongoing throughout the year by tracking changes in vendor performance, security incidents, or any changes in their business operations. These refreshed risk assessments and security ratings should also be retained in your company’s third-party inventory.
Third-Party Offboarding
While many third-party relationships continue for many, many years, there does eventually come a time when a third-party needs to be offboarded, whether that’s for cost purposes, the third-party has been acquired or gone out of business, or your company simply doesn’t require those materials or services any longer.
Offboarding a third-party seems deceptively simple, however it’s essential to be detail-oriented in the offboarding phase. In today’s intertwined digital ecosystem, it’s easy to miss third-party accounts, services, or users that need to be removed or disabled. Access privileges need to be revoked, user accounts disabled, API integrations removed and any third-party issued software or applications removed. As with personnel offboarding, having a templated checklist of offboarding steps for third-parties is an invaluable tool to ensure that a vendor or provider has been fully removed from your organization’s environment and information systems.
Equally important is retrieving intellectual property, IT devices, and other company assets provided to third-parties over the course of your organization’s relationship with them. These should be cataloged and tracked until all listed items have been returned.
Properly offboarding a third-party vendor is so critical because of the digital backdoors they can leave in your environment – usually unintentionally. Failing to disable third-party users, accounts, or services can leave those open for attackers to exploit. Likewise, leaving IT assets and intellectual property with third-parties could open your organization to exposure through those avenues.
With the third-party risk management best practices and lifecycle outlined above, your team can step up the organization’s TPRM program and protect the company from third-party risks. The team will be ready to step up your TPRM program and protect your organization from third-party risks. There are some common stumbling blocks when it comes to managing vendor risk, and we’ll discuss the best ways to cope with them below.
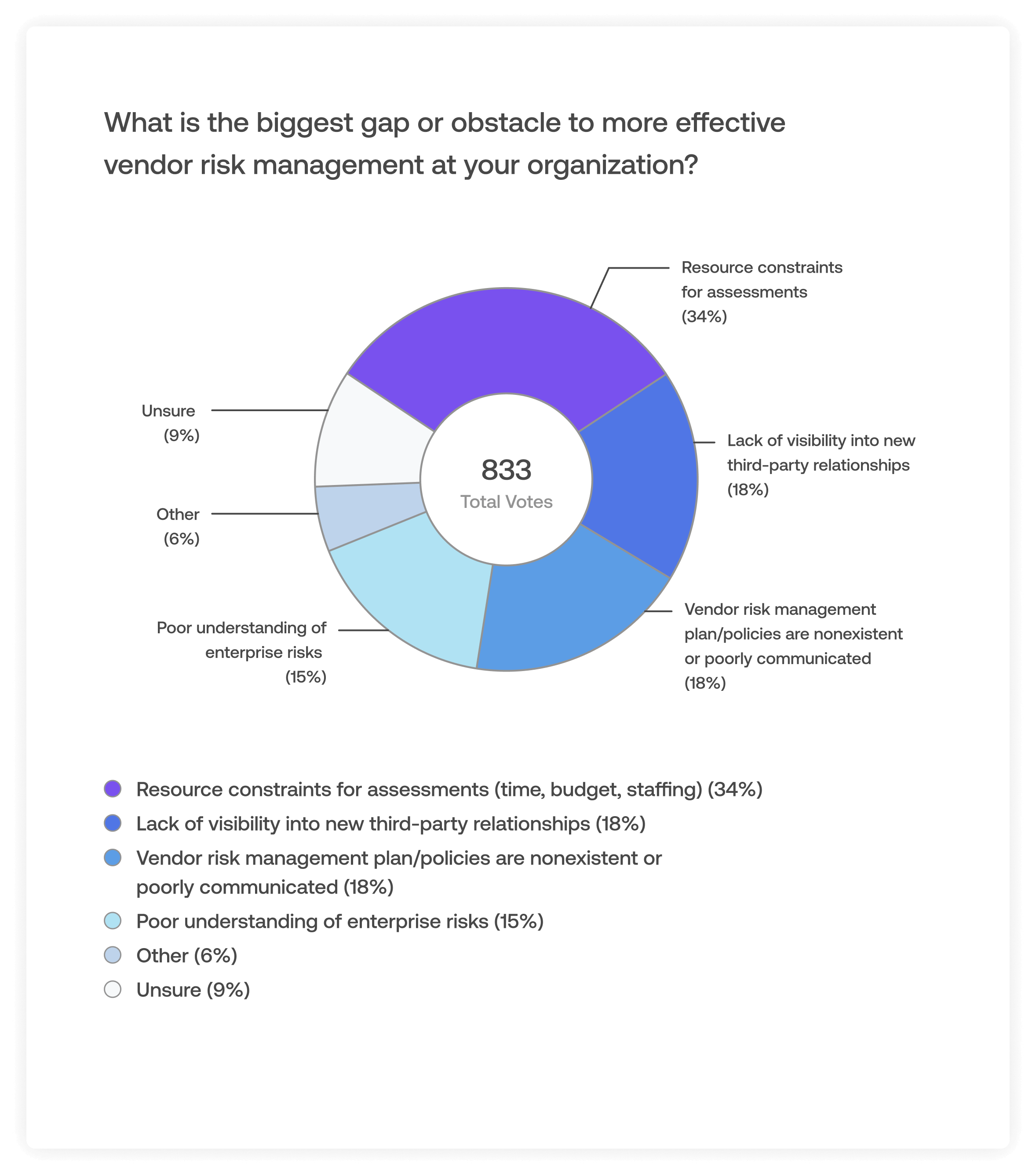
Where do TPRM Gaps and Obstacles Present Themselves?
Despite the developments in third-party risk management, all organizations face challenges in establishing effective TPRM programs. A 2021 AuditBoard survey of 800+ risk and compliance professionals across North America found the most commonly cited challenges, in descending order, were:
- Resource constraints for assessments (e.g., time, budget, staffing).
- Lack of visibility into new third-party relationships.
- Nonexistent or poorly communicated vendor risk management plan/policies.
- Poor understanding of enterprise risks.
Although there’s no silver bullet for all of these challenges, there are a few things your organization can do to handle them.
Resource Constraints
Perhaps the most difficult challenge to cope with, many companies are feeling the squeeze of a tumultuous economy, geopolitical upheaval, and inflation. It’s not easy to get headcount requests approved, funding is scarcer, and budgets keep shrinking. Perhaps the best way to gain more resources and buy-in is to demonstrate the cost of data breaches and illustrate the importance of third-party risk management as a deterrent and control mechanism.
Lack of Visibility into New Third-Party Relationships
In the past, this was a particularly difficult challenge to deal with. Without centralized systems and repositories, it was hard to get a handle on all of the suppliers and vendors present in a large organization. Now, there are tools and technologies that can help you and your company scan your environment and discover the third-parties present. This can bring all the internal stakeholders for their procurements in a single pane of glass.
Nonexistent or Poorly Communicated Vendor Risk Management Policies
Coupled with resource constraints, the lack of a well-communicated vendor risk management program or policies can make managing third-party risks almost impossible. However, vendor risk management policies and procedures don’t have to be overly complex. Simply compiling a list of third-parties in the environment and assigning them a criticality rating based on their importance to operations is a great starting point for a third-party risk management program.
Poor Understanding of Enterprise Risks
One way of managing third-party risks without having a good understanding of macro-level enterprise risks is to start with what you have (current state). Referring to a third-party risk inventory and understanding the criticality of each vendor in your environment can give a good idea of where the most significant third-party risks lie, and which vendors need the most attention and monitoring. Often, companies contract with third parties to manage non-core business areas, allowing them to focus on their primary offerings and maintain their competitive edge.
Take Advantage of Third-Party Risk Management Software
Whatever your biggest challenges, improving your understanding of key third-party risk management tactics and success factors can help you close gaps and overcome obstacles. Purpose-built third-party risk management technology can change the game and provide your team with a centralized dashboard and inventory for managing all of your third-parties and associated risks. To revamp your TPRM program and level up your team’s capabilities, schedule a demo of our TPRM software today.
Whatever your biggest challenges, improving your understanding of key third-party risk management tactics and success factors can help you close gaps and overcome obstacles. For practical tips on building an effective third-party risk management program, download the full guide here.
Frequently Asked Questions About Third-Party Risk Management (TPRM)
What are the guiding principles of third-party risk management?
Third-party risk management involves assessing the risks tied to each third party, performing thorough due diligence before engagement, and consistently monitoring their performance and risk levels. Clear contracts should outline expectations and responsibilities, and compliance with relevant laws and regulations must be ensured. It’s also crucial to have a plan for addressing any issues or breaches, and to maintain detailed records and reports on third-party risk management activities.
What are the common TPRM Program components?
A Third-Party Risk Management (TPRM) program typically includes assessing the risks associated with each third party, conducting thorough due diligence before engagement, and establishing clear contracts that outline roles and responsibilities. It also involves having a structured onboarding process, continuously monitoring third-party performance and risk levels, ensuring compliance with relevant laws and regulations, and maintaining a plan for addressing any issues or breaches. Detailed record-keeping and regular reporting are also key components.
Where do TPRM gaps and obstacles present themselves?
Third-Party Risk Management (TPRM) gaps and obstacles often arise in various areas. These include having insufficient resources such as staff and budget, not conducting thorough risk assessments, and lacking effective due diligence before engaging third parties. Weaknesses may also appear in monitoring third-party activities, managing contracts unclearly, ensuring compliance with laws, and responding to incidents. Challenges can also involve maintaining accurate records, communicating effectively between teams, and navigating cultural differences, especially with international third parties.
About the authors

Richard Marcus, CISA, CRISC, CISM, TPECS, is the CISO at AuditBoard, where he is focused on product, infrastructure, and corporate IT security, as well as leading the charge on AuditBoard’s own internal compliance initiatives. In this capacity, he has become an AuditBoard product power user, leveraging the platform’s robust feature set to satisfy compliance, risk assessment, and audit use cases. Connect with Richard on LinkedIn.
You may also like to read


Mind your business: The real secret to career growth

How to transform your GRC strategy with AI-driven tools

How AI maturity impacts risk, speed, and strategy

Mind your business: The real secret to career growth

How to transform your GRC strategy with AI-driven tools
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO




