
August 15, 2023 • 8 min read
Taking a Risk-Based Approach to Your Security Compliance Program
Your board and investors are thinking about risk — it drives their decisions. You’re already making risk-based decisions: when you see risk but don’t talk about it – you own that risk. Risk management frameworks can only specify controls and objectives, but it’s risk itself that should drive the development of controls and objectives.
For all these reasons, it’s a good idea to use risk-based approach to drive security and security compliance programs. This article explores the benefits of a risk-based approach and discusses how to use top-down and bottom-up risk assessments to convey risk information more fully, identifying gaps and trends in compliance risk and delivering the insights that shape an effective security compliance program.
Benefits of a Risk-Based Approach to Compliance
According to a recent Gartner survey, risk considerations drive leadership decisions, as risk appetite statements are linked to business outcomes. Talking with board members about risks to business objectives is, therefore, a meaningful way to support them. In fact, a risk-based approach positions security compliance professionals to discuss any threat that concerns the board and executives in terms of responses that are already planned and controls already in place. By gathering and organizing risk information, you can speak knowledgeably about whether any threat is increasing risk to your organization and whether you’ve already addressed the threat with other capabilities.
Getting Started: Know the Business
Taking a risk-based approach to compliance starts with knowing the business. These steps help you familiarize yourself with the organization so you can make an effective assessment of compliance risk.
- Know leaders’ risk tolerance and appetite. Is there a clear statement from leaders to indicate their risk appetite? If not, your budget may indicate how much risk the business is willing to assume. But don’t leave it at that: have the conversation with leaders to ensure an explicit statement of risk appetite. In discussions with stakeholders, clarify that risk only exists when there is real financial impact to the business. Whether it’s regulatory risk, or risk to image, reputation, or something else, expressing risk in financial terms helps decision-makers understand relative impacts. Viewing risk through a financial lens can help focus conversations.
- Learn what leaders are thinking. Listening to executives about the risks on their minds helps ensure your program is solving the right problems. Talking to executives about risk empowers them as true risk owners. In the context of building systems, deploying new capabilities, and moving into new business markets, business leaders are taking risks. Security compliance programs can help by informing them about the risks associated with these activities.
- Get to know the business:
What processes do leaders consider the most important?
Who owns those processes?
What controls and objectives are needed to assure compliance?
What technologies and facilities do those processes depend on? - What processes do leaders consider the most important?
- Who owns those processes?
- What controls and objectives are needed to assure compliance?
- What technologies and facilities do those processes depend on?
- Look for existing documents. You can start to learn about key processes and capabilities by studying the current business impact assessment. Even business continuity documents can offer important context as you begin.
- Identify the critical data. Knowing the business’ goals and objectives will drive identification of critical data. Security compliance programs must look beyond regulated data to include all data types that could impact the organization.
Approaches to Risk Assessment: Top-Down and Bottom-Up
There are two common approaches to risk assessment: top-down and bottom-up. Organizations often adopt one approach or the other, but adoption of both results in a more complete and usable assessment of risk. Here is how they differ, and how they can be aligned for a more complete picture of risk:
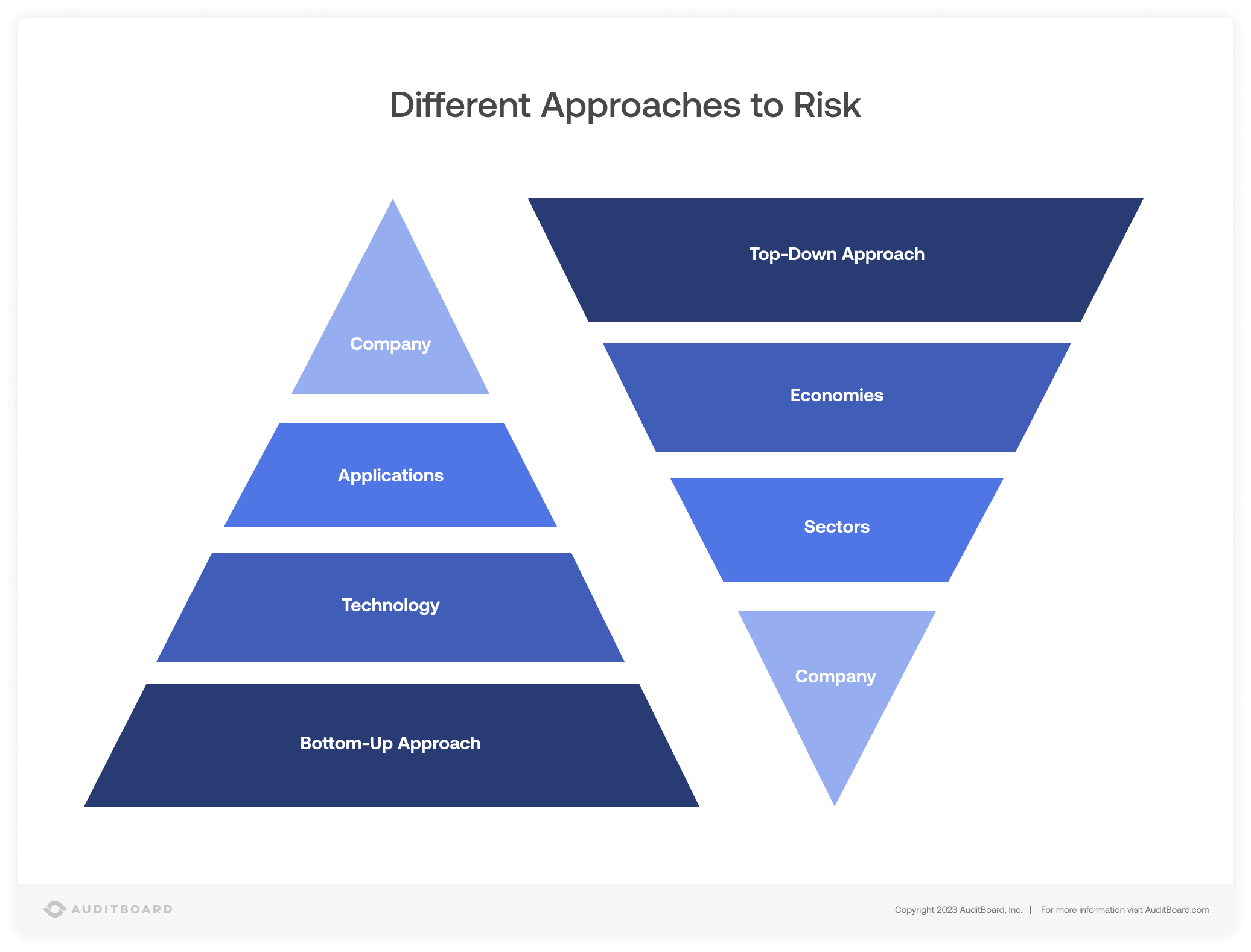
Top-down risk assessments are based on business functions, and are frequently the basis for board reporting. At this point, we’re assessing the highest-level risks that command the attention of senior leaders, like losing the ability to manufacture, or losing critical intellectual property. Identify top risks and analyze each for impact. If you can’t identify a tangible risk to the business, it isn’t a risk. Develop your risk register to support risk trending over time, and discuss these risks with your executive and board stakeholders regularly.
Bottom-up risk assessments focus on threats. The bottom-up approach generates a lot of detailed data, so leaders can understand risks more deeply. Data is critical to risk. You can have a third party do a bottom-up risk assessment initially, after which you can routinely update it.
Aligning the information resulting from top-down and bottom-up risk assessments yields significant benefit. Stakeholders will be able to drill down from any high-level risk to see underlying issues taking place in the business. Leaders will be able to understand top risks more deeply by viewing data from bottom-up risk assessments. They’ll see controls gaps and failures as well as new risks entering the register based on new systems, business models, and compliance requirements.
This aligned collection of risk data enables analysts to identify gaps, patterns, and trends. It points the way to new security initiatives and to the most effective structure for the overall security compliance program.
It is not impossible to merge and align top-down and bottom-up risk assessment information in tools as simple as spreadsheets. A robust connected risk platform, however, enables mapping between bottom-up risks to controls, and between controls and top-level risks. Risk data that’s organized for drill-down and trending supports more meaningful conversations about how compliance and security investments are yielding returns for the enterprise.
Better Together
Boards rely on risk information to drive their decisions. While compliance frameworks help by specifying controls and objectives, frameworks can’t analyze the organization’s risks. Risk should drive the development of controls and objectives that frameworks specify. Top-down or bottom-up risk assessment approaches are each powerful in their way. The most effective risk-based security compliance programs, however, use top-down and bottom-up risk assessment approaches together to enable more complete analyses that can identify gaps, patterns, and trends.
You may also like to read

What is the Colorado AI Act? A detailed guide to SB 205

What is the EU AI Act?

What is the NIST AI Risk Management Framework?
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO



