
August 15, 2022 • 7 min read
Tactics for Continuous Third-Party Risk Monitoring

Richard Marcus
Third-party risks change as the business changes. Security breaches, new contracts, and changes in internal risk ownership — to name a few examples — can all impact the performance of a third-party risk management program (TPRM). To effectively execute a continuous risk monitoring program, it is necessary to have a solid foundation of TPRM guiding principles and organizing best practices. Beyond this, it is important to tailor your risk monitoring approach to match the level of your organization’s third-party risk prioritization and categorizations.
Below, learn six tactics for continuous third-party risk monitoring, and download the full guide, Effective Third-Party Risk Management: Key Tactics and Success Factors.
1. Ensure the tactics used are proportional to the level of risk each third party presents to your organization.
TPRM programs commonly employ a range of tactics for assessing third-party risks and controls. The following are the most commonly used tools for assessing third-party risk:
- Security Controls Questionnaires. The most common tactic, this flexible approach allows you to customize each questionnaire based on the type of third party and the risks you are concerned with.
- Standardized Questionnaires. Widely used options include Shared Assessments’ Standardized Information Gathering Questionnaire (SIG) and Cloud Security Alliance’s Cloud Control Matrix (CCM) Consensus Assessment Initiative Questionnaire (CAIQ). Third parties may be familiar with, and have ready responses to, these questionnaires.
- Compliance certifications and reports. Common examples include: HIPAA, GDPR, NIST 800-53, SSAE-18 SOC 2, CSA STAR, and CCM.
- Onsite audits. Should generally be reserved only for your highest-risk third parties — those that present truly critical risks to your organization.
- Contract reviews. While contract reviews are generally performed by your legal team, it’s ideal to embed your risk team in the process.
- Reputation services reports. These services develop third-party risk ratings — essentially “security credit scores.”
2. Establish a periodic reassessment cadence based on risk level.
The most important success factor is to structure and formalize continuous monitoring activities based on risk level. Higher-risk third parties should receive more attention more frequently, and lower-risk third parties should receive less attention less frequently.
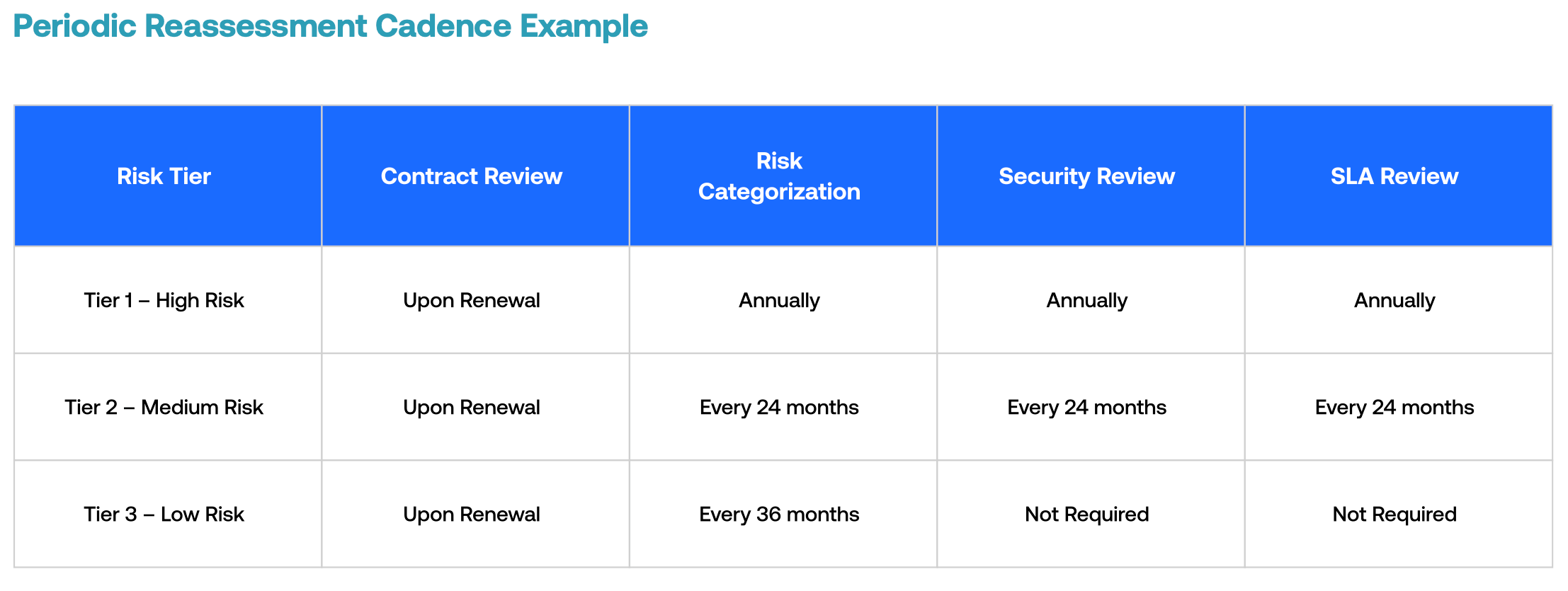
3. Perform rediscovery with internal relationship owners.
Risk changes over time, so reassessments should involve appropriate rediscovery with your organization’s third-party relationship owners. This will help ensure that TPRM approaches and categorization continue to be appropriate for each third party. Most often, rediscovery occurs via surveys that are either sent manually or triggered within a third-party risk management solution. Surveys should address:
- Relationship ownership. Are they still the owner?
- Risk categorization. Have the use cases that the third party is addressing changed? Have there been changes to the third party’s risk profile?
- Contract renewals. Should terms be restructured to better manage risk or account for new considerations?
- SLAs. How do they feel about the overall performance of the third party? Are SLAs being met? While SLA review isn’t typically in the risk mandate, reassessment touchpoints are a great opportunity to assess SLA compliance.
4. Perform targeted assessments following key events.
You may want to re-engage third parties outside your normal cadence to either re-assess or perform a targeted assessment:
- After a security incident or breach.
- After a public zero day, if it’s likely the third party was impacted.
- After you’ve updated your internal risk assessment(s).
5. Build accountability around regularly updated risk assessments.
Effective TPRM programs take place against the backdrop of regularly updated organization-wide risk assessment(s) and around an overall culture of accountability. The risks stemming from control gaps or other identified issues with third parties should be quantified and rolled up from the relationship owner, to the executives responsible for owning the overall risks for their area of the organization.
As a result, relationship owners can collaborate with risk owners on the tradeoffs of engaging this third party, changing how they negotiate that third party’s contract and SLAs, implementing compensating internal controls, or causing them to engage a different third party altogether.
6. Focus on meaningful, effective reporting.
Another key success factor is creating meaningful reporting that regularly communicates risk information and insight to the right people across your organization. Effective TPRM issue management and reporting are symbiotic, benefiting and supporting each other in turn. Meaningful reporting helps to create ongoing awareness of key gaps and risks. When awareness is raised with the right people, reporting remains meaningful and accurate. People are equipped not only to avoid issues, but to respond more effectively when they occur.
For more practical tips on building an effective third-party risk management program, download the full guide here.
About the authors

Richard Marcus, CISA, CRISC, CISM, TPECS, is the CISO at AuditBoard, where he is focused on product, infrastructure, and corporate IT security, as well as leading the charge on AuditBoard’s own internal compliance initiatives. In this capacity, he has become an AuditBoard product power user, leveraging the platform’s robust feature set to satisfy compliance, risk assessment, and audit use cases. Connect with Richard on LinkedIn.
You may also like to read

What is the Colorado AI Act? A detailed guide to SB 205

What is the EU AI Act?

What is the NIST AI Risk Management Framework?
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO




