
August 24, 2023 • 8 min read
Raising the Cybersecurity Bar for CISOs
The average cost of a reported breach in 2022 was more than $24 million. By now, most high-level enterprise decision-makers are well aware of the costs — and risks — that cyber threats represent to the ongoing success of their business operations. They’ve evolved metrics and processes for evaluating the strategies that business unit managers, CIOs, and CFOs present to them. They can use these metrics to rank risks and opportunities, outline strategies, and create timeline projections of proactive plans for both meeting business goals and managing risks.
The SANS 2023 Attack and Threat Report, sponsored by AuditBoard, takes a deep dive into how CISOs are often strong in identifying big risks, but weak when it comes to prioritization, remediation, and developing business-relevant security metrics. The first step in overcoming these challenges and obtaining management support for changes needed to raise the cybersecurity bar is for CISOs and other security leaders to understand the rapidly evolving threat landscape and — crucially — its impact on enterprise risks. For a more comprehensive look, download our new report: SANS 2023 Attack and Threat Report.
We’ll begin with a baseline from data collected by the Identity Theft Resource Center (ITRC), a nonprofit organization that works to minimize the risk and mitigate the impacts of identity compromise. The ITRC has applied a consistent methodology for many years, using only verified information from publicly disclosed breaches. It doesn’t include incidents, like denial-of-service attacks, that don’t result in the exposure of private information, but it does include the most recent ransomware attacks.
The ITRC data shows a slight decrease in the number of breaches reported in 2022, compared with 2021. The number of records exposed, however, rose dramatically, from 298,213,506 in 2021 to 422,143,312 in 2022, for an average of more than 234,000 records exposed per breach. The hard costs of a breach of that size typically are calculated to be in the $100-per-record range, which means the average cost of a reported breach in 2022 was more than $24 million.
Prioritize third-party sources of security failures
One significant factor the ITRC notes is that 40% of breaches in 2022 were via supply chain partners. That is consistent with SANS Institute’s observations that as an enterprise raises its level of security maturity, its supply chain partners often become the weakest point in its defense. These aren’t the only third-party sources of security failures. We’ve also seen malicious actors focusing on service providers as a means of compromising multiple targets simultaneously. The ITRC reports that a major trend in 2021 and 2022 has been fewer breach reports releasing detailed information indicating the root cause of the breach.
This is likely due to recent court rulings requiring that actual damage, not potential harm, be proven in order for a damage claim to be upheld. This lack of information for 2022 reports makes direct comparisons with 2021 somewhat more difficult. However, looking only at breaches where root cause information is available makes some trends clear, including:
- Successful phishing attacks are still the leading cause of breaches at 53%, up from 36% in 2021.
- Ransomware was still a growth industry in 2022, up to 32% from 23% in 2021.
- Zero-day attacks still represent only a small fraction of root cause reports, at under 1%. Just as this report was being finalized, the ITRC released statistics for Q1 2023. The overall numbers largely mirror Q1 2022’s, but the number of breaches and records exposed doubled for the technology sector.
This is consistent with the continued criminal focus on compromising service providers in technology.
Minimize damage from supply chain attacks
The annual Verizon Data Breach Investigation Report (DBIR), first released in 2008, has consistently been another rich source of information about attacks and threats. The DBIR is based on incident response investigations of actual successful attacks, so it provides the most detailed root cause information available. The single most important factor enabling successful attacks in 2022 was the attackers’ use of reusable credentials, mostly obtained with phishing techniques. Enhanced security awareness and education along with better email security gateways have reduced the percentage of phishing emails users click on. But when enterprises rely on reusable passwords, all it takes is one click on the wrong link and the game is over.
Verizon’s investigation found an even higher rate of supply chain compromise than the ITRC, reporting 62% of intrusions involved a supply chain partner. A key point from the DBIR: “Compromising the right partner is a force multiplier for threat actors. Unlike a financially motivated actor, nation-state threat actors may skip the breach and keep the access.”
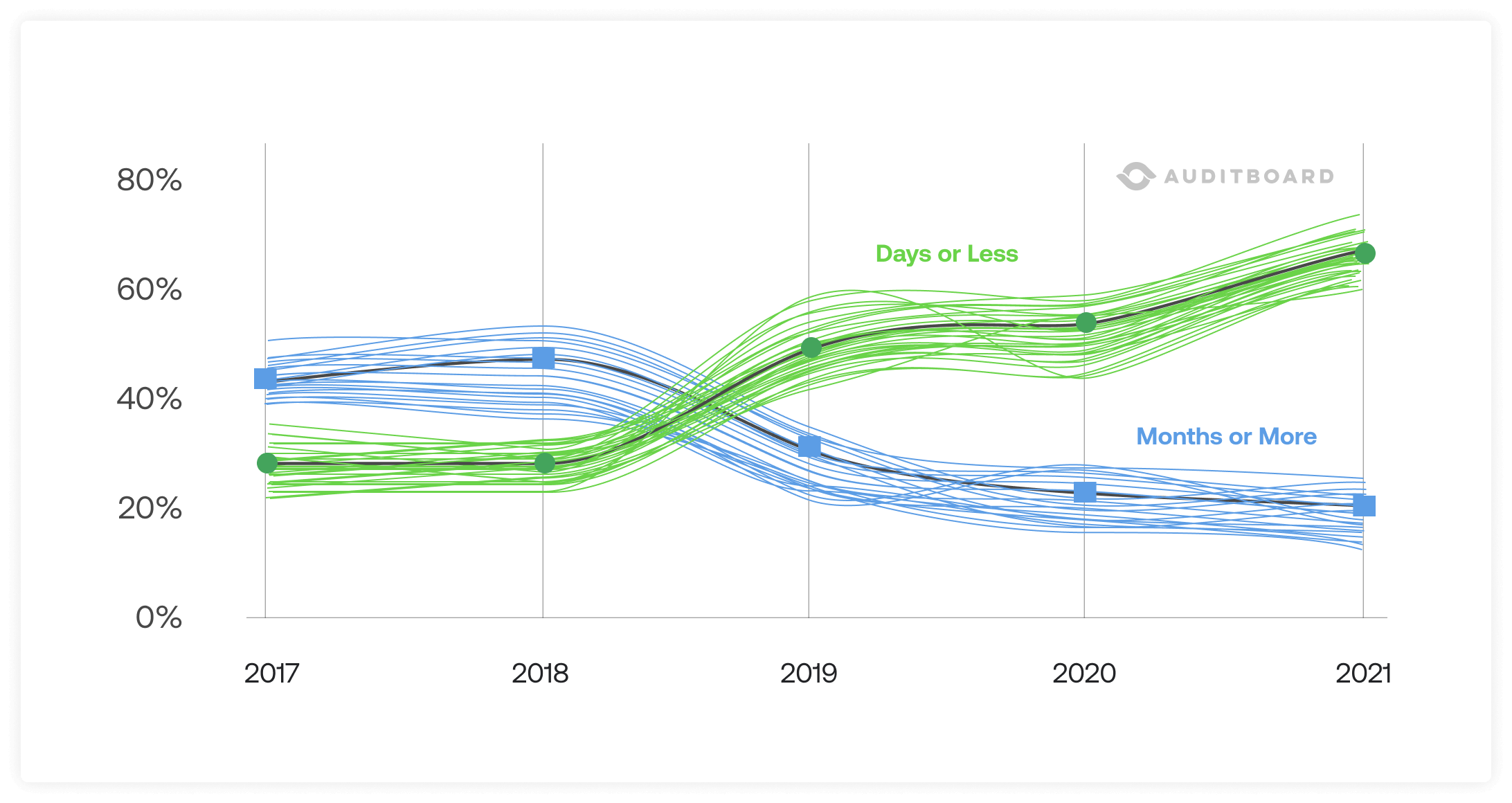
This means that time-to-detect is key to minimizing damage from supply chain attacks that—as is often the case in politically motivated attacks—have the goal of monitoring an enterprise’s research and development (R&D) and business efforts over an extended period. The DBIR did have some good news on the time-to-detect front, showing that enterprises are now more likely to detect in days rather than months. But, of course, this is only for the 50% of breaches not “actor disclosed,” as often happens in ransomware events.
Assess the current threat environment
What does all this data tell us about the current threat environment? Essentially, although there have been definite improvements in some areas—notably end-user security awareness and endpoint protection—the bad actors are constantly evolving their tools and techniques. That means CISOs and other security leaders must be constantly updating their knowledge of the threat environment and the risk impacts of emerging threats on enterprise operations. The presentations by the expert panelists at RSA Conference 2023 are an excellent place to start.
They included these takeaways:
- Reusable passwords remain irresistible low-hanging fruit for threat actors.
- Where enterprises have strengthened their levels of essential security hygiene, attackers are going after supply chain partners as the “screen window” access point.
- Zero-day attacks get the headlines, but 99% of breaches exploit well-known vulnerabilities in people, processes, and software for which mitigation actions are available and widely known.
The SANS Institute’s newest report, sponsored by AuditBoard, examines the up-to-the-minute information on emerging cyber threats and their impacts that CISOs need. Download SANS Attack and Threat Report 2023 to learn more.
You may also like to read

What is the Colorado AI Act? A detailed guide to SB 205

What is the EU AI Act?

What is the NIST AI Risk Management Framework?
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO



