
April 24, 2023 • 16 min read
NIST vs. ISO: What’s the Difference?

Vice Vicente
Your company needs security standards to benchmark against industry best practices, reduce losses, maintain your customers’ trust, and protect your bottom line. Your company needs a risk management strategy that incorporates security compliance, business needs, and data protection. Your company needs an infosec pathway that lets you fend off cyber attacks and stay within budget. When it comes to cybersecurity, the National Institute of Standards and Technology (NIST) and the International Organization for Standardization (ISO) dominate the standards scene. SOC 2 has a place in this conversation too, though for now, we’ll focus on NIST’s Cybersecurity Framework (CSF) and ISO’s 27000 family. But which set of standards should you pursue and implement? What are the benefits and differences between these information security risk management frameworks?
Because you are investing precious time and energy into developing your information security program, you’ll want to consider the pros and cons of NIST vs. ISO—which set of standards is most relevant to you and your business right now? Which set of standards will best suit your needs and protect your organization from cyber-attacks? This article provides an overview of the differences and overlaps between NIST’s Cybersecurity Framework (CSF) and ISO 27001 to help you make the right choice for your business.
What is the NIST CSF (Cybersecurity Framework)?
Unlike GDPR and HIPAA, which are mandatory privacy and security standards, the NIST Cybersecurity Framework (CSF) is a voluntary framework that allows companies to develop their information security, risk management, and control programs, regardless of the size of their business or the industry they’re in. The CSF was developed by the National Institute of Standards and Technology, a non-regulatory US government agency housed under the Department of Commerce. Today, NIST standards are employed in fields from nanotechnology to cybersecurity (and they even have their own measurement superheroes). In 2013, NIST was tasked with developing a Cybersecurity Framework through an executive order and published version 1.0 of the Framework for Improving Critical Infrastructure Cybersecurity in February 2014. Version 1.1 was made publicly available in April 2018. Currently, NIST is soliciting public comments on the NIST Cybersecurity Framework 2.0 draft by November 2023.
The CSF is one of NIST’s voluntary programs that is based on existing standards and guidelines and is developed with flexibility to help organizations better manage and reduce cybersecurity risk. The Cybersecurity Framework is not the only NIST framework that relates to this area — NIST has also released a Risk Management Framework (NIST RMF) to provide organizations with guidance on managing risk. The CSF is presented in a 48-page document that details different cybersecurity activities and desired outcomes that organizations can leverage for assessing their cybersecurity risk, risk maturity, and infrastructure around information security.
NIST’s core CSF documentation is supported by supplemental resources and Special Publications, like the NIST 800 series which covers various cybersecurity topics. Their guide for handling incident response and their publications on authentication security are especially popular. These resources are backed by considerable research and public comment, and undergo periodic revisions. The NIST CSF is used widely among federal agencies and their subcontractors due to the requirements imposed on government contractors regarding data security.
What Is NIST CSF Used For?
The CSF has three major components: the framework core, implementation tiers, and profiles, all designed to help you benchmark your organization’s risk maturity and security posture, in order to prioritize actions you need to take to make improvements. The framework core describes the actual controls and bones of the program, while implementation tiers illustrate an organization’s security maturity level, and profiles are formed by a company’s unique mix of risks, controls, and technology.
The Framework Core:
The “core” is divided into five functions: Identify, Protect, Detect, Respond, and Recover. While the CSF applies these functions to cybersecurity issues, they are really essential activities in most risk management systems. The functions are further divided into 23 categories, which cover the fundamentals of building a cybersecurity program. The five functions work in tandem to mitigate cybersecurity risks.
Implementation Tiers:
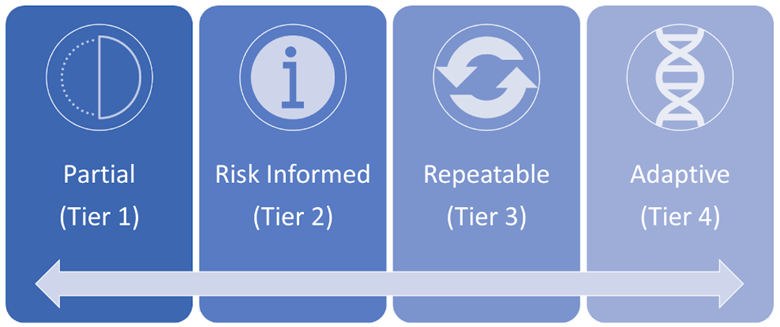
Implementation tiers are meant to indicate where in the cybersecurity maturity lifecycle an organization has reached. In other words, an organization’s implementation tier in the context of NIST’s CSF indicates how much of the CSF an organization has put into place, and how well it has put those practices in place. The lowest of four tiers indicates a “partial” implementation of the CSF, while the highest tier indicates an “adaptive,” or agile and informed approach to the CSF implementation. Companies can use these implementation tiers to measure their own security posture and target higher tiers as goals.
Image: NIST Implementation Tiers
Profiles:
Based on the tier, the profile lets an organization pinpoint its current level of risk tolerance and prioritize security controls and risk mitigation tactics. This section is designed to help an organization grow by comparing its current profile with target profiles, helping your organization determine how to allocate budget and employee resources to improve cybersecurity safeguards over time.
What Is ISO 27001?
ISO is a non-governmental organization operating in Geneva, Switzerland, that has released over 22,600 international standards across a variety of industries since its inception in 1954. Their 27000 family of standards is one of their most popular, covering a wide range of controls related to IT security risk management. ISO 27001 presents a framework for developing and implementing information security management systems (ISMS). The ISO/IEC 27001 standard was originally released in 2005, then substantially updated in 2013, and, like the NIST CSF, was updated most recently in 2018. The 27000 family of standards is often integrated with the ISO 9000 family of standards for Quality Management Systems (QMS).
ISO 27001 offers organizations a standard to be certified against. ISO certification requires a third-party assessor to perform an audit of an organization’s adherence to the ISO 27001 standard, especially Annex A. The certification, if obtained, lasts for three years, with a recertification audit required after. Through the automation of controls, the certification and compliance process becomes more streamlined.
What Is ISO 27001 Used For?
ISO 27001 is designed to help an organization operationalize cybersecurity controls they may have developed to cover particular situations or compliance needs into full-fledged information security management systems (ISMS) and security controls. It is best suited for organizations that have already put in place an infosec program, and want to take it to the next level. It is also possible to achieve official ISO 27001 certification through a third-party auditor. This certification can be shown to partners, customers, and other stakeholders to demonstrate the company’s dedication to security and compliance. Like NIST CSF, ISO 27001 doesn’t promote specific technologies or products, and can be applied to organizations in any industry of any size, even startups. An operationally mature organization that has already, for example, achieved compliance or certification with ISO 9001, may be ready to tackle ISO 27001.
ISO 27001 VS NIST CSF
So, what are the commonalities and differences between ISO 27001 and the NIST CSF? How do they differ? And which standard is right for your organization?
What Are the Commonalities Between ISO and NIST?
In comparing NIST CSF vs ISO 27001, both offer robust frameworks for cybersecurity risk management. An organization seeking to become compliant with ISO 27001 standards and implement the NIST CSF framework will find them easy to integrate. Their control measures are similar, and the definitions and codes are fairly transferable across frameworks. Both frameworks offer a simple vocabulary that allows you to communicate clearly about cybersecurity issues across multidisciplinary teams and with external stakeholders. They are produced by reputable standards organizations, and updated to match external trends.
What are the Differences Between ISO and NIST?
When it comes to NIST CSF and ISO 27001, there are a few key differences, including risk maturity, certification, and cost.
Risk Maturity
ISO 27001 is a good choice for operationally mature organizations seeking certification, while the NIST CSF may be best for organizations that are in the first stages of developing a cybersecurity risk management plan or attempting to mitigate prior failures or data breaches. While ISO 27001 does not have maturity tiers, the NIST CSF provides four implementation tiers that illustrate an organization’s security maturity based on adherence to NIST’s guidance. Companies seeking to evaluate their security performance against industry benchmarks and elevate the maturity of their cybersecurity risk programs can use NIST’s tiers to target higher levels of implementation.
Certification
ISO 27001 offers globally recognized certification via third-party audit that can be costly but can enhance your organization’s reputation as a business that stakeholders can trust. NIST CSF does not offer such certification. ISO 27001 is a popular international certification that can pave the way for partnerships and lucrative sales deals, making it an ideal standard for companies that do business around the world. ISO 27001 has many similarities to SOC 2, and they can have similar audit scopes.
Cost
The NIST CSF is available free of charge, while ISO 27001 charges to access their documentation—another reason an upstart might want to initiate their cybersecurity risk management program with the NIST CSF and then make a bigger investment in the process as they scale with ISO 27001.
NIST vs ISO: Which One Is Right for My Business?
Ultimately, what’s right for your business depends on its maturity, goals, and specific risk management needs. ISO 27001 is a great choice for operationally mature organizations facing external pressure to certify. However, you may not be ready to invest in an ISO 27001 certification journey quite yet, or your organization may be at a stage where it would benefit from the clear assessment framework offered by the NIST Cybersecurity Framework. Conducting a NIST audit can give you a sense of where your organization stands prior to developing and implementing more stringent cybersecurity measures and controls.
The two frameworks can be integrated as your organization matures—following the NIST CSF framework can be a useful precursor to your ISO 27001 certification journey. The NIST CSF offers growing organizations a way to structure their first cybersecurity risk assessments. If you already have these structures in place, you might consider going straight for ISO security and compliance certifications. Regardless of whether you’re starting with NIST CSF or growing with ISO 27001, a proactive and efficient information security management system benefits from the right software. AuditBoard stands ready to help— get started with our compliance management software today.
Frequently Asked Questions About NIST vs ISO
What Is NIST CSF (Cybersecurity Framework)?
The NIST CSF is a framework consisting of standards, guidelines and best practices designed to apply to various industries, with the aim of protecting critical infrastructure.
What Is ISO 27001?
ISO 27001 is an international standard for information security management systems (ISMS) designed to help organizations put a system in place to manage cybersecurity risks.
What Is NIST CSF Used For?
The NIST CSF is a voluntary framework that any organization can use to manage cybersecurity risk.
What Is ISO 27001 Used For?
ISO 27001 is designed to help an organization systematize cybersecurity controls that they may have developed to cover particular situations or compliance needs into full-fledged information security management systems (ISMS).
What Is the Difference Between ISO and NIST?
NIST and ISO differ in several ways, and some core differences are that NIST is part of the US Department of Commerce while ISO is an international standards organization; NIST’s CSF cannot be certified or audited against, while ISO 27001 can; and NIST is free while ISO 27001 does have a cost.
What are the commonalities between ISO and NIST?
NIST and ISO both provide guidance on cybersecurity and information security best practices, are voluntary, regularly update their documentation, and provide supplemental guidance for implementing specific control sets.
About the authors

Vice Vicente started their career at EY and has spent the past 10 years in the IT compliance, risk management, and cybersecurity space. Vice has served, audited, or consulted for over 120 clients, implementing security and compliance programs and technologies, performing engagements around SOX 404, SOC 1, SOC 2, PCI DSS, and HIPAA, and guiding companies through security and compliance readiness. Connect with Vice on LinkedIn.
You may also like to read

What is the Colorado AI Act? A detailed guide to SB 205

What is the EU AI Act?

What is the NIST AI Risk Management Framework?
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO



