January 12, 2023 • 7 min read
Managing Third-Party Relationships: Effective Approaches to TPRM and Compliance
SolarWinds, Log4j, Kaseya: All are security incidents that have been in the headlines over the past several years; all are security incidents that resulted from third-party breaches. The frequency and severity of third-party breaches are on the rise: 90% of organizations were impacted by a supply chain cybersecurity breach in 2022. Organizations are constantly challenged to fend against the potential of a security breach tied to one of often hundreds of third parties with which they engage. In the past year alone, organizations have had numerous serious threats to navigate, including incidents at GitHub and Toyota.
Find out effective approaches to TPRM and compliance below, and download the full IDC Spotlight, sponsored by AuditBoard, Beyond the Organization: Managing Risk and Compliance in Third-Party Relationships, to learn more about this emerging risk landscape, the results of the IDC Future of Trust Survey, and what organizations can do to protect themselves.
Benefits of Automating Third-Party Risk Management
With the frequency and severity of third-party breaches increasing, security frameworks and supply chain legislation are evolving to minimize the impact of these events. The intention of these efforts varies with both carrot (providing guidance in avoiding breaches) and stick (penalties levied if such breaches occur) approaches being pursued. These initiatives are targeting third-party risk at regional, national, and supranational levels.
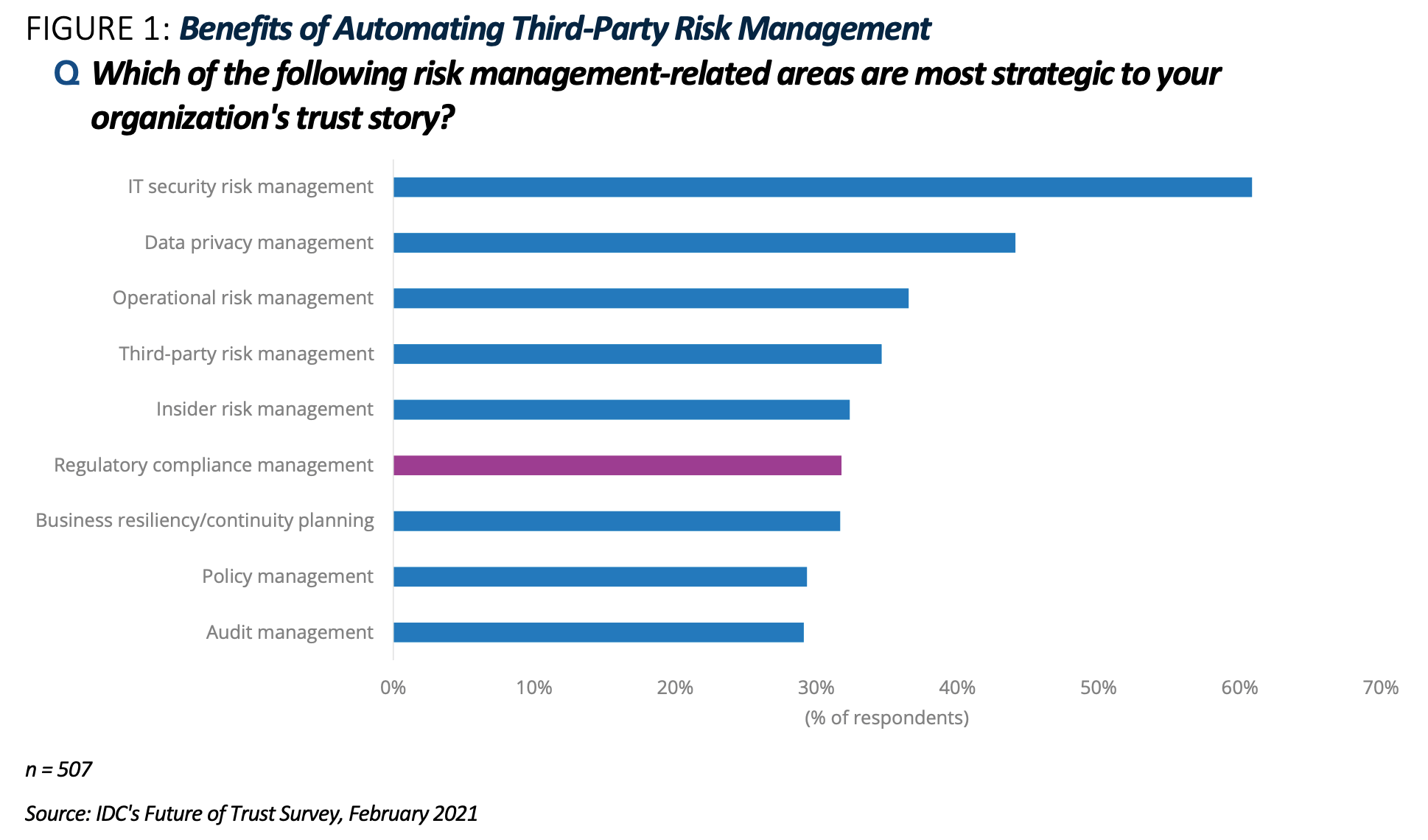
The current environment of heightened third-party software attacks and subsequent legislative response is elevating third-party risk management (TPRM) as an organizational priority. Modern organizations are increasingly focused on managing business risk to foster resiliency and trust; however, much of the risk that an organization contends with is not internal but stems from third-party relationships. Organizations rely on third-party suppliers for products and services necessary to operate; however, these relationships inherently introduce risk to organizations. IDC research has found that third-party risk is among the top considerations for organizational risk management, ranking just below internal IT security, data privacy, and operational risk (see Figure 1). Third-party risk is particularly important in an organization because failure to secure third-party relationships will directly impact these other aspects of organizational risk.
How to Respond
TPRM solutions support organizations in managing the myriad of risks across hundreds, or thousands, of third-party suppliers. The information management and automation benefits that
TPRM solutions deliver result in increased efficiency and efficacy in vendor risk analysis, which, in turn, reduces the potential for a risk event to occur. Among the key capabilities that TPRM solutions offer in preventing a third-party security breach are:
Vendor inventory: The first step in managing third-party risk is to identify an organization’s vendors and chronicle those vendors in a central repository. TPRM solutions can support an organization’s efforts to inventory vendors and leverage this inventory with applied intelligence to launch assessments and other monitoring/remediation efforts.
Vendor screening/due diligence: TPRM solutions automate initial vendor assessments, questionnaires/surveys, and risk rating. Automating vendor due diligence typically reduces vendor assessment time by 30–50%, which is a significant savings across a network of hundreds of vendors.
Software bill of materials: Organizations can leverage TPRM software to continuously monitor SBOMs and minimize risk. A secondary application of automated vendor screening is to collect information during onboarding (either via surveys or open source lists) of the “ingredients” in a software solution. By ingesting this detailed information, when security issues arise, organizations can quickly assess which of their software vendors may be impacted by the issue and begin remediation efforts.
Third-party risk categorization and assignment of key controls: TPRM solutions assess and rank vendor risk, basing the level and frequency of review on this risk rating. This automated analysis can also determine which questions should be included in the due diligence process, eliminating unnecessary information collection and thus improving efficiency for both the client and its vendors.
Risk/compliance monitoring (continuous monitoring): While due diligence review and onboarding assessment help organizations select the best partners at the moment, risk is fluid, and a trusted partner can become a risk very quickly. Even when vendors are reassessed at regular intervals, significant risk events require immediate remediation, reducing the efficacy of this type of risk management. For this reason, vendors must be continuously assessed across risk parameters. Integration with news monitoring and risk scorecard services supports this continuous assessment. A risk management platform that automates risk notices based on risk events identified by these services helps organizations better identify and respond to vendor risk.
Automated alerts/workflows/risk response: A key component of TPRM solutions is automation of notifications and remediation of risk using preset parameters linked to various risk controls. When vendors fall out of compliance with a particular control, workflows are commenced that alert the appropriate responders, and the risk is remediated.
Learn more about this emerging risk landscape, the results of the IDC survey, and what organizations can do to protect themselves in the IDC Spotlight, sponsored by AuditBoard, Beyond the Organization: Managing Risk and Compliance in Third-Party Relationships.
You may also like to read


An executive’s guide to the risks of Large Language Models (LLMs)

What is a model card report? Your guide to responsible AI

What is AI governance, and why does it matter?

An executive’s guide to the risks of Large Language Models (LLMs)

What is a model card report? Your guide to responsible AI
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO