
June 2, 2022 • 6 min read
Keys to Organizing a Successful Third-Party Risk Management Program

Richard Marcus
Whether an organization works with 10, 1,000, or 10,000 third parties, any third-party risk management (TPRM) program faces the same challenges: organization, visibility, and limited resources. How an organization approaches these challenges from the beginning can set a third-party risk program up for success or failure. First, it is essential for risk management practitioners to familiarize (or refamiliarize) themselves with the guiding principles of third-party risk management.
One helpful resource is our guide to Effective Third-Party Risk Management: Key Tactics and Success Factors. Once you have a firm understanding of the foundational principles, the following organizing tactics can help you set your third-party risk management program up for ongoing success.
Ensure Ongoing Visibility Between the “Where” and the “Who”
What is the best way to formalize your plan, policies, and processes for continually identifying new third parties working with the business? The most important tactics are to:
- Assess WHERE in your organization new third-party engagements are initiated.
- Identify WHO is responsible for assessing and making decisions about relationship risk.
- Build a process that ensures ongoing visibility between the WHERE and the WHO.
The graphic below further fleshes out the goals your identification and discovery process should be designed to support.
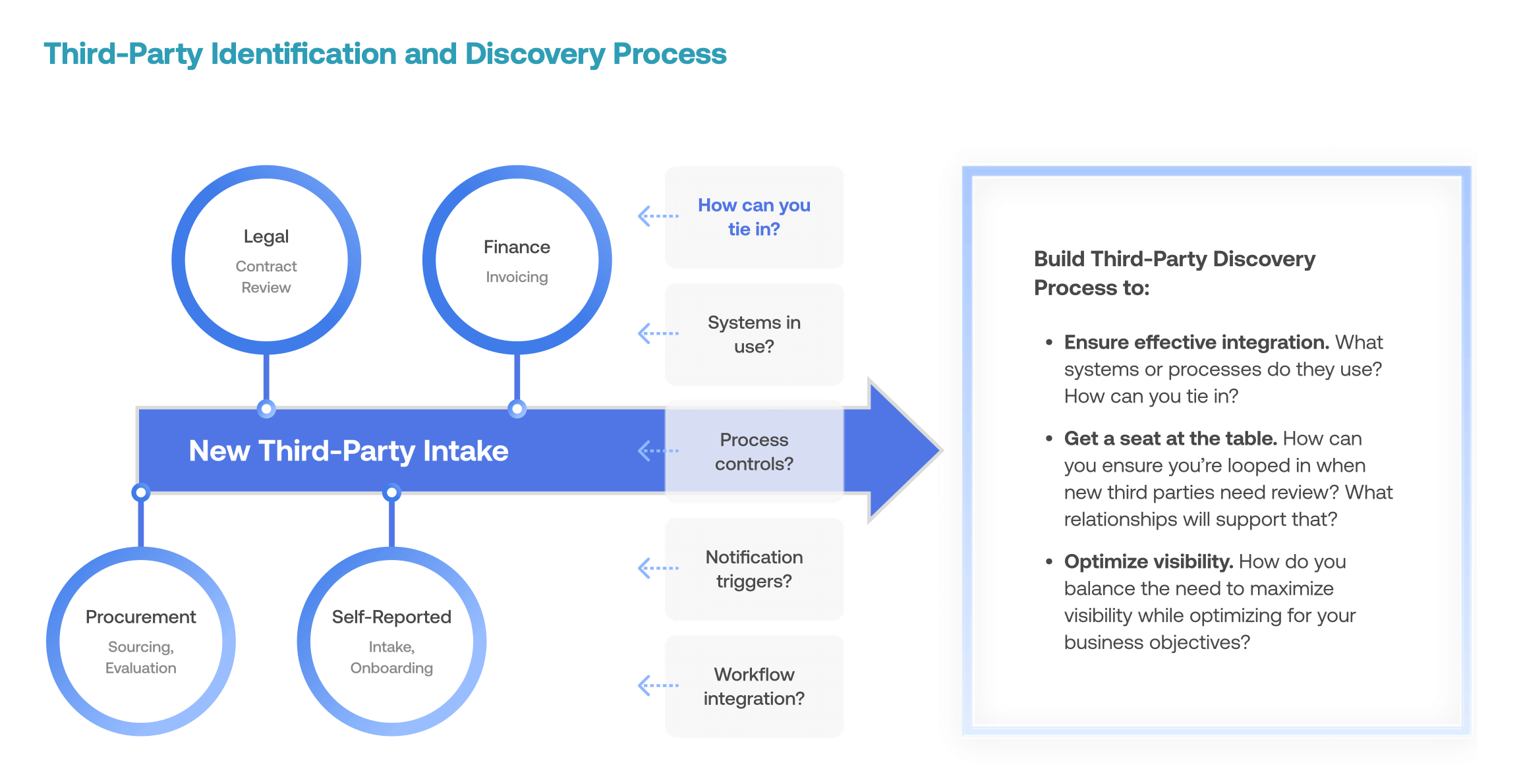
Third-Party Identification and Discovery Process
Establishing a reliable mechanism for capturing these pieces of information can often be facilitated by technology platforms such as AuditBoard. In addition, the following are ways to enable smart and proactive resource deployment:
- Create and promote clear, readily available TPRM policy and process guidance.
- Use simple vendor request and review forms at the point of intake.
- Establish a complete, regularly-updated inventory of third parties.
- Scale assessment and remediation approach(es) as appropriate to match risk levels.
- Consider technology tools that create a safety net and offer ongoing visibility. For example, automated discovery tools that connect to payment or contracting systems (e.g., G2 Track) can be set up to provide alerts following triggers you establish.
Third-Party Risk Categorization Tactics
The most important success factor for a TPRM program is to structure and formalize continuous monitoring activities based on risk level. Higher-risk third parties should receive more attention more frequently, and lower-risk third parties should receive less attention less frequently.
“The most important success factor for a TPRM program is to structure and formalize continuous monitoring activities based on risk level.”
As such, creating and updating third-party risk categorization is a key success factor for any TPRM program. Since all third parties do not present equal risk, they should not consume equal risk assessment capacity. Develop criteria to help you categorize third parties into high-, medium-, and low-risk buckets that help you better allocate your limited resources where they’ll have the most impact.
Begin by referring back to your enterprise and cybersecurity risk assessments, assessing each third party based on the risks that matter most to your organization. For example, if access to confidential data is the most important consideration for your organization, you may establish the following risk tier categories.

Based on the risk profile of your organization, you could also consider categorizing third parties based on questions such as:
- Is the third party a critical dependency to meet organizational objectives?
- Will the third party have access to confidential or customer data?
- Will the third party have direct access to your infrastructure, networks, or systems?
- Does the third party support the availability of customer-facing services?
- Does the third party support any critical internal business functions?
- Can the third party impact your organization’s reputation or business relationships?
- What is the estimated spend?
- How many internal users, teams, functions, or processes will rely on this third party to perform?
Ensure Realistic, Appropriate Distribution Across Tiers
Keep an eye on distribution across tiers. Most third parties should fit into Tiers 2 and 3. Be very discerning with categorizing third parties as Tier 1, since that’s where you’ll invest the most time and resources.
By keeping these organizational tactics in mind, risk management practitioners can build a solid foundation for identifying and categorizing third-party risks on a consistent basis. Moving forward, this enables teams to deploy their resources in the most effective and efficient manner toward risk/controls assessments, audits, issue management, reporting, and ultimately — continuous monitoring. For more practical tips on building an effective third-party risk management program, download the full guide to Effective Third-Party Risk Management: Key Tactics and Success Factors.
About the authors

Richard Marcus, CISA, CRISC, CISM, TPECS, is the CISO at AuditBoard, where he is focused on product, infrastructure, and corporate IT security, as well as leading the charge on AuditBoard’s own internal compliance initiatives. In this capacity, he has become an AuditBoard product power user, leveraging the platform’s robust feature set to satisfy compliance, risk assessment, and audit use cases. Connect with Richard on LinkedIn.
You may also like to read


What is a model card report? Your guide to responsible AI
GRC survival guide: Thriving in the era of AI SaaS

An executive’s guide to the risks of Large Language Models (LLMs)

What is a model card report? Your guide to responsible AI

GRC survival guide: Thriving in the era of AI SaaS
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO




