June 17, 2025 • 22 min read
Fraud triangle: A practical guide for internal audit teams
Your quarterly vendor analysis flags three new suppliers added without proper onboarding documentation. When you pull the approval records, the authorization trail breaks down at a critical step.
These details deserve attention. In audit, fraud rarely arrives with a label — it emerges as a string of small decisions, patterns, and changes others might miss.
Opportunity, pressure, and rationalization shape everyday choices. In practice, they appear as backdated approvals, off-cycle payments, or shifting justifications when targets get tight. Each sign is specific. Each one asks for clear answers, not guesswork.
Effective audit leaders use the fraud triangle — a simple framework that explains what drives people to commit fraud — to guide investigation, not to assign blame. When your team names risk factors in plain language and ties them to actual events, you get smarter discussions and stronger controls. The right approach is methodical: Track the facts, ask focused questions, and document actions.
Fraud prevention thrives on process and persistence. With a sharp, consistently applied framework, your team doesn’t just respond: They anticipate, strengthen weak spots, and give your organization practical confidence in its controls.
What is the fraud triangle — and why does it matter?
The fraud triangle isn’t just a textbook concept. It’s a shortcut for spotting trouble before it starts. Every instance of fraud ties back to three simple forces: opportunity, pressure, and rationalization. For fraud to occur, these three forces typically work together, creating the conditions where someone might cross ethical boundaries.
You see the elements of the fraud triangle every day. Perceived opportunity appears when controls get loose or duties aren’t separated. Financial pressure builds when hitting a number feels urgent, or when personal finances get tight. Rationalization comes in quiet moments: a well-meaning employee tells themselves, “I’ll fix it next quarter.”
The triangle matters because it’s a practical checklist. When you break down possible fraud, ask three things: Where could someone act unchecked? Who feels squeezed right now? What stories make bending the rules sound reasonable?
By using the fraud triangle as your lens, you don’t chase ghosts. You focus on the situations where the risk of fraud is most likely and build audits that ask sharper questions, get better answers, and close real gaps before they grow.
Understanding pressure, opportunity, and rationalization
Most fraudulent activity — large or small — traces back to these three elements. Pressure is the push: maybe it’s missing a sales goal, covering a personal loss, or juggling too many demands. According to the Institute of Internal Auditors, about 95% of fraud cases involve financial or vice-related pressures.
Opportunity takes shape when processes break down or duties aren’t clearly separated, making the door to abuse easy to open.
Rationalization is the story people tell themselves: a small shortcut, a temporary fix, or an excuse that softens the risk.
These aren’t distant ideas; they show up every time you review payments, question manual approvals, or look at exceptions that no one wants to explain. Spotting fraud risk means asking: What’s pushing people to take risks? Where are the weak spots in our controls? How might someone justify a bad call, even for what seems like a good reason?
By seeing these elements in the details of daily work, audit teams keep focus on where risks build and where questions matter most.
Where the classic fraud triangle falls short
The fraud triangle’s basics still hold up, but the model doesn’t catch everything in today’s complex environments. Employees work across borders and systems now. Fraudsters use new tools and technology, sometimes moving faster than controls can keep up. Not every scheme fits neatly into just opportunity, pressure, or rationalization.
Pressure takes new forms. Some employees feel the weight of working alone from home more than any sales target or revenue slump. Culture and team dynamics now shape how people handle stress, sometimes even more than their own finances. On top of that, the rise of digital payments and quick approvals opens up weak spots that older processes never had to address.
And the players have changed. Fraud isn’t always a one-person job; sometimes, people team up and sidestep controls meant for individuals. Every month, there’s a new tool or workflow. The pace of tech leaves audit procedures scrambling to catch up.
You can’t count on old patterns sticking around. The basics are still your anchor, but risk keeps moving. To keep up, your fraud approach should move too. Update your reviews to match how your business really works now. When you combine the triangle with practical questions and tools that fit today’s environment, you spot what others miss.
Modern variations of the fraud triangle in practice
Auditors see firsthand how fraud risk evolves. Technology, remote work, and new business models mean red flags show up in different shapes. This is why versions of the fraud triangle now reflect specific environments: Cybersecurity, procurement, or financial statements reporting all come with their own types of risk.
Some teams use the cyber fraud triangle: motivation, capability, and rationalization. Here, technical skill opens doors that didn’t exist a decade ago, and motivation can be anything from a challenge to ideology. In other domains, the pressure shifts — a supplier relationship, a regulatory deadline, or fast-changing market conditions might drive someone to stretch the rules.
Tailoring the model matters. Rigid checklists miss unique risks. A fresh look at the triangle sharpens focus during planning, fieldwork, and conversations with management. Fraud fighting isn’t static; neither are your tools.
The cyber fraud triangle: Motivation, capability, rationalization
Instead of only looking for pressure and opportunity, audit teams must consider technical skill and intent. In cyber fraud, motivation isn’t always about money. Some actors want a challenge, and others aim for disruption or to make a statement. Capability becomes the gatekeeper — fraudsters might need specific software, credentials, or insider knowledge to exploit a control.
Rationalization still plays a role, but it can sound different online. Someone may justify their actions by blaming weak security or telling themselves that large organizations “won’t miss it.”
Cyber incidents often combine teamwork, automation, and speed. Traditional controls (like manual approvals) lose power in the face of well-equipped attackers. By mapping motivation, skill level, and rationalization to each risk, audit teams build better questions and target their controls where cyber threats are most likely to slip through.
Tailoring the triangle to specific audit domains
No two audit areas look the same. Procurement, financial reporting, and cybersecurity each carry their own types of risk and pressure points. In procurement, opportunity might appear in single-person approvals or vague vendor vetting.
Financial reporting brings pressure from quarterly targets or looming deadlines. Rationalization shifts too. A team member might justify “timing adjustments” to meet expectations or see a payment as a harmless favor.
Audit teams get better results when they adjust the fraud triangle for the landscape in front of them. Ask what opportunities are unique to this process or department. Probe for sources of pressure — regulatory, operational, and reputational — that could shape risky decisions. Consider how rationalizations change as incentives and controls shift.
Building this mindset into your planning gives you sharper risk assessments and control tests that fit the real world, not a generic checklist.
Using the fraud triangle in audit planning and fieldwork
Theory comes to life when audit teams translate the fraud triangle into action. Planning starts with mapping where opportunity, pressure, and rationalization could surface in the process you’re reviewing. Fieldwork then puts that map to the test, looking for red flags, testing controls, and tracking inconsistencies.
"AuditBoard has helped us address risk and drive consistency. Our overall company strategy — and one of the big messages from our CEO — is to do the right thing always. Having AuditBoard gives people the visibility into what's expected and helps them really understand what the values of the company are and why we're doing things," explains Alex Byrne, Director of Internal Audit at Watts Water.
Effective fraud detection goes deeper than asking, “Could fraud happen here?” It breaks down each element: Who faces new or unusual demands this year? Where could someone override controls or slip something past a split responsibility? Which rationalizations are you actually hearing in walkthroughs or interviews?
Good fieldwork means blending structured questions with real curiosity. It’s about picking up on patterns, cross-checking stories, and documenting both what you see and what doesn’t add up. Consistency matters.
When the fraud triangle frames the audit from start to finish, nothing gets overlooked, and responses stay grounded in evidence.
Identifying fraud risk factors in risk assessments
Strong audits start with clear risk identification. This means looking beyond routine checklists and focusing on the real-world pressures and opportunities in your organization. Pay attention to roles with broad access or weak oversight. Watch for business units under new stress, whether from growth, downsizing, or leadership changes.
Teams get better results by asking direct questions: Where have responsibilities shifted? Has anyone taken on duties outside their usual scope? Are there changes in incentives or policies that might make rationalizing a risky decision easier?
Document findings in straightforward terms. Link each risk factor to specific processes and why it matters. When you bring the fraud triangle into your assessment, you’re not guessing where to start. You’re targeting the most likely trouble spots from the outset.
Incorporating red flags into test design
Strong test plans catch more than obvious errors. They target the places where fraud risk is highest: roles with high access, points where duties blur, and steps that can be overridden or bypassed. Before designing your tests, review recent exceptions, policy overrides, or transactions that stand out for their timing or structure.
Effective teams use scenarios from the fraud triangle to shape testing. For example, design tests that check for duplicate payments where opportunity exists, or sudden changes in approval chains when pressure peaks. Don’t limit procedures to one department. Fraud often crosses boundaries.
Discuss red flags openly during planning. Agree on clear triggers for follow-up questions, deeper sampling, or escalation. When everyone on the team understands what to look for, routine testing becomes a real tool for early detection.
When to deepen your review — or bring in others
Finding a red flag raises the stakes. Not every sign means fraud is taking place, but every signal deserves a response.
The first step is to determine whether there’s a pattern or a one-off error. Review the documentation. If controls failed, map out how and where. If facts or explanations are missing, dig deeper with follow-up questions and extra samples.
If doubts remain, pause before jumping to conclusions. Escalate only when you see repeated issues, evidence of intent, or links to higher-risk areas. Have a clear process for moving findings beyond your team, whether that means alerting management, compliance, or a formal investigation unit.
The shift from a deeper review to escalation comes down to what you find. In practice, your team gathers facts, documents every step, and only involves management or outside experts when the evidence points to a bigger issue. You need enough detail to support next steps — so you’re never left guessing if your decisions are questioned later.
Awareness training and red flag recognition
Fraud isn’t just an internal control concern. It’s a growing threat to business performance and reputation. According to the ACFE, businesses lose an estimated 5% of revenue each year to fraud. No organization is immune. Rising losses signal that methods are evolving, and organizations of every size face higher risk.
Many teams can’t catch fraud because they don’t know what to look for. Training makes red flags visible and gives staff the language to describe suspicious patterns. Most audit leaders start with examples: unusual vendor changes, inconsistent documentation, or habits that sidestep approval steps.
The goal isn’t to turn everyone into an investigator. It’s to help people recognize when a detail deserves a second look.
Each part of the fraud triangle has its own warning signs. Changes in lifestyle or pushback on controls hint at pressure. A lack of oversight or staff turnover can create an opportunity. Rationalization emerges as justifications: “That’s how we’ve always done it,” or “This helps us hit the deadline.” Bring real cases and lived examples into your training. Not just rules, but stories your team will remember.
By making red flag awareness part of your control environment, you give your team the power to surface concerns early and start conversations before issues grow.
Fraud triangle: Common red flags
Red flags look different depending on which part of the triangle you’re watching.
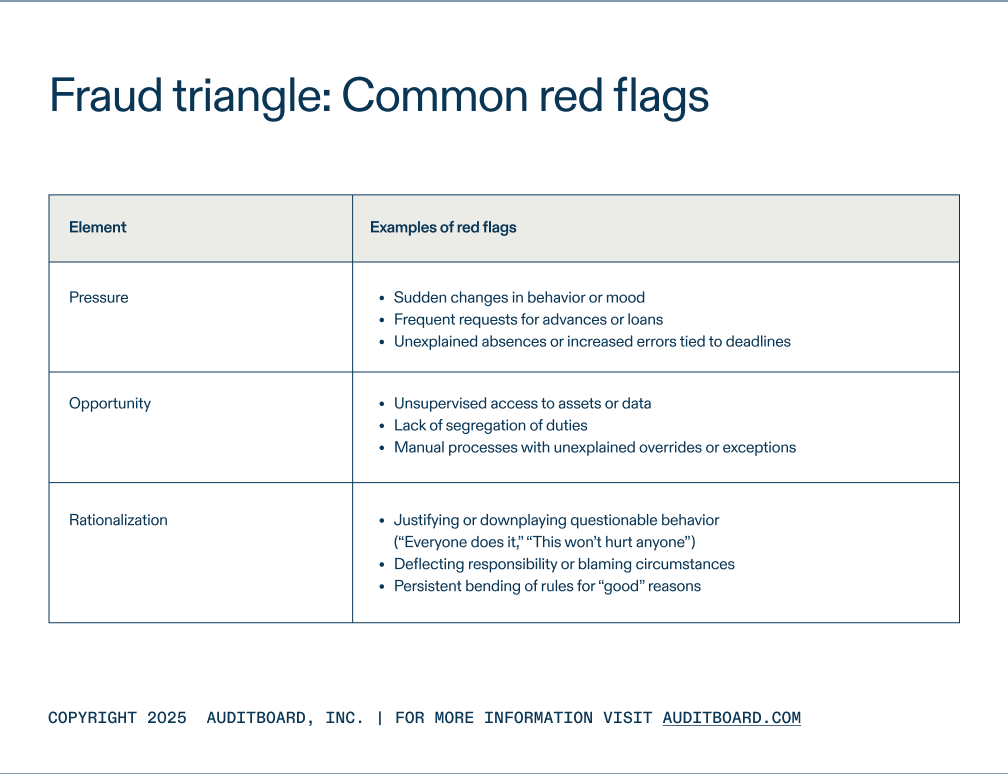
Not every red flag means fraud has happened, but patterns are worth flagging. The more your team learns to spot specific symptoms (linked to real-life cases), the faster you can separate noise from genuine risk.
How to train audit teams on fraud scenarios
Training sticks when it’s built around actual cases and hands-on scenarios. Move beyond theory by using recent examples from your organization or public cases that match your risks:
- Start with real cases. Select incidents from your own company or credible news sources. Walk the team through each stage: What pressure was present? Where did the opportunity arise? How was rationalization expressed?
- Break cases down step by step. Ask your team to call out red flags at each point and explain what responses might be appropriate.
- Use role-play and practical exercises. Have team members practice interviews, review mock documentation, or update an old policy together. Scenarios should match the types of risk and controls your team faces every day.
- Get other departments involved. Finance, HR, and compliance can provide fresh views on how pressure, opportunity, and rationalization show up across the business.
- Make it a habit. Reinforce red flag awareness at project launches and in recurring audit meetings. The practice of asking, “Where could these elements show up next?” keeps everyone alert.
This approach turns training into muscle memory and helps your team spot fraud risks before they become bigger problems.
How AuditBoard helps auditors detect and document fraud risk
AuditBoard gives audit teams a single source for risk factors, red flags, test results, and documentation. Each feature is built to make seeing, tracking, and responding to fraud risks simpler and faster.
Here’s how the platform supports your entire workflow:
Embed red flags and risk factors into assessments
AuditBoard lets you build risk factors and red flags right into your assessment templates. As you scope each audit, you can note exactly where opportunity, pressure, or rationalization might surface and tie those risks to specific controls, owners, and workflows.

Custom fields and checklists help teams capture evidence as they go. No more spreadsheets lost in someone’s inbox. With a few clicks, your team can document exceptions, link issues to findings, and highlight trends that need extra attention. High-risk areas get flagged automatically, so nothing slips through when schedules get tight.
A shared, transparent assessment process not only cuts down on manual work, but it also keeps your whole team focused on the real risks, setting up every audit for faster action and better decisions.
Link audit test results to potential fraud indicators
AuditBoard connects your test results directly to fraud risk areas. As you complete workpapers and testing steps, you can tag findings with specific red flags or link them to related controls and issues. If an exception pops up, it’s easy to trace it back to the underlying risk. No more digging through separate documents or email trails.
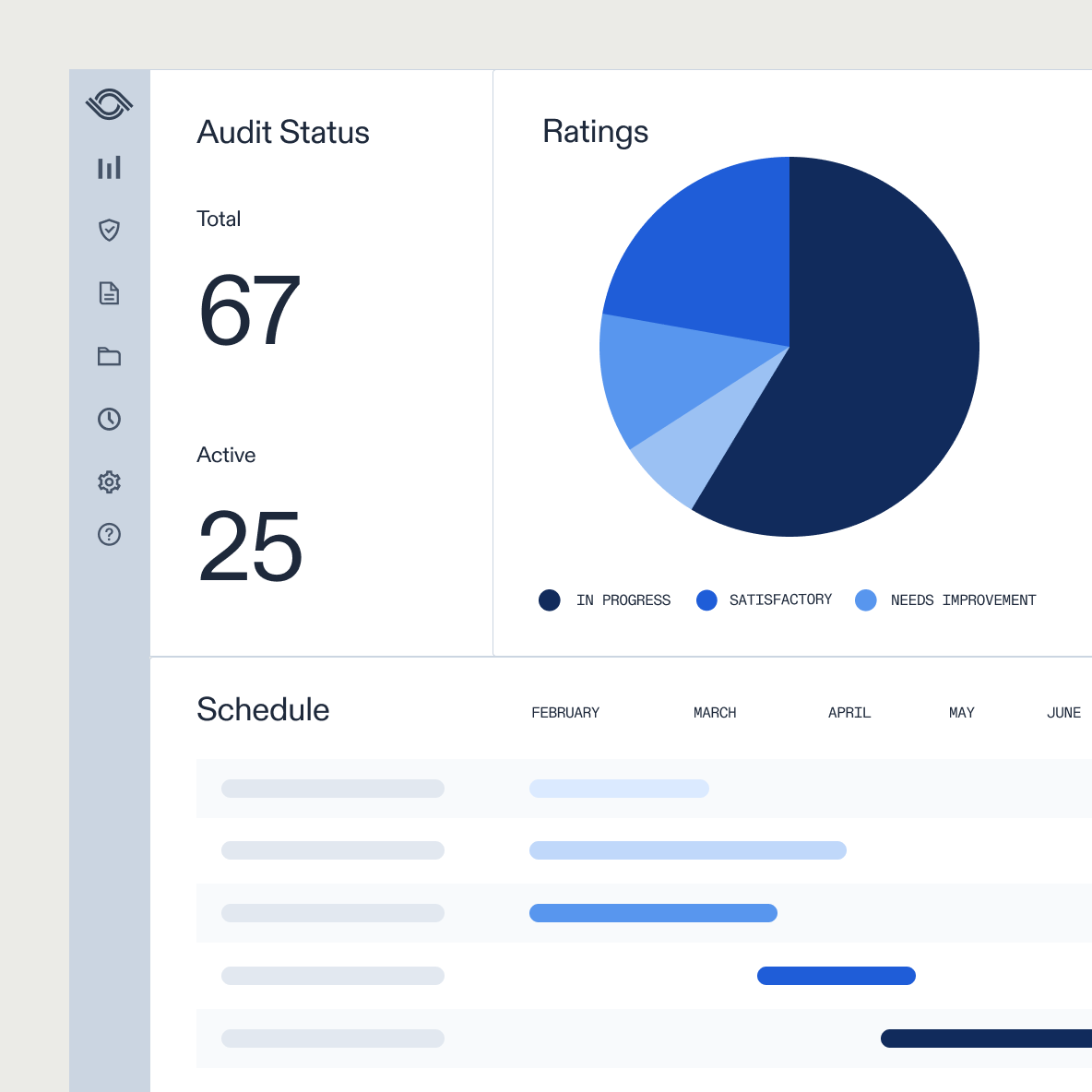
With everything in one place, your team can spot trends earlier, such as repeated issues with approvals or payments that keep crossing thresholds. When it’s time for management reporting or escalation, the supporting evidence is organized and ready for review.
This speeds up response time and helps prove how your audits keep the organization ahead of fraud risk.
Centralize documentation for escalation and reporting
AuditBoard keeps all your evidence, correspondence, and decisions in a single, accessible platform. When you need to escalate an issue, whether to management, compliance, or investigators, you can quickly pull all related workpapers, test findings, and supporting documents.
No more piecing together a timeline from scattered files.
Consistent, centralized documentation also makes reporting easier and more credible. Trends spotted across audits, recurring red flags, or escalation history can all be surfaced with just a few clicks. This transparency gives your leadership (and external reviewers) confidence that fraud risks are monitored and resolved with a clear, reliable process.
Turning fraud theory into audit practice
Fraud risk never waits for the perfect moment. It hides in everyday routines and shifting pressures. Turn the fraud triangle into your team's daily playbook: Ask sharper questions, design better tests, and use real data to close gaps before they grow.
With the proper process and technology, you move from firefighting to foresight. AuditBoard provides structure, speed, and insight to every step, so your team builds trust through action, not just intention.
Bring the fraud triangle to life with smarter audits, better documentation, and connected controls — all in AuditBoard.
Request a demo today to level up your fraud risk management.
You may also like to read


AuditBoard and IAF report: The more you know about AI-enabled fraud, the better equipped you are to fight it

Audit reporting best practices: Guide for audit leaders

Boards are struggling with AI oversight. How internal auditors can help

AuditBoard and IAF report: The more you know about AI-enabled fraud, the better equipped you are to fight it

Audit reporting best practices: Guide for audit leaders
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO