
March 30, 2023 • 10 min read
Disruptions, Data Loss, and Reputational Damage: Why Organizations Are Prioritizing Third-Party Risk Management
In CyberRisk Alliance Business Intelligence’s November 2022 Third-Party Risk Survey, more than half (57%) of respondents reported they were victims of an IT security incident — either an attack or a breach — related to a third-party partner in the past 24 months.
The fear of severe consequences from a third-party-related attack or breach — including business disruption, financial losses, network and infrastructure disruptions, data loss, reputational damage, and regulatory compliance failure — have convinced more senior and board-level executives to increase their oversight of proactive third-party risk management, particularly as these types of breaches continue to make headlines. Customers, regulators, auditors, and cyber insurance providers are also leaning on organizations to demonstrate proper vetting and deeper management of their partners, according to multiple survey respondents.
Learn how organizations are impacted by third-party cyberattacks and how they are prioritizing third-party risk management — and download your free copy of the CyberRisk Alliance Business Intelligence report, sponsored by AuditBoard, Third-Party Risk: More Third Parties + Limited Supply-Chain Visibility = Big Risks for Organizations.
Business and Custom Service Disruptions, Data Loss, and Damaged Reputation Arising From Third-Party-Related Incidents
More than half of all respondents (57%) reported they were victims of an IT security incident — either an attack or a breach — related to a third-party partner in the past 24 months. On average, organizations experienced two third-party-related security incidents (attacks or breaches) in the past two years. This number increases with organization size, with respondents from the largest organizations estimating they experienced an average of five incidents during this period.
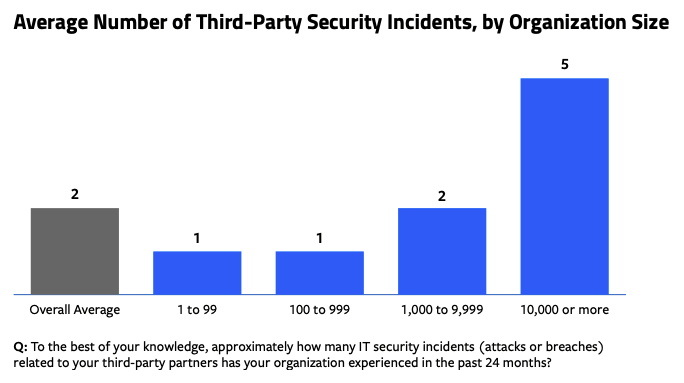
In recounting their experiences with attacks and breaches originating from third parties, respondents’ descriptions ranged from minor incidents with little organizational impact, to major attacks and breaches in which their organization suffered serious consequences. Typically, organizations encountered business, customer service, and supply chain disruptions and delays, computing infrastructure failure or downtime, re-installations and re-implementations of software and business processes, stolen data/data leakage, and additional remediation resources and extra manual efforts as a result of a third-party incident. In some cases, organizations also faced reputational repercussions, legal actions, and even FBI investigations.
““Our supplier of PCs was hacked and it affected their supply chain, billing, AR/AP, and [caused] lots of frustrations between us.””
Respondents also revealed their accounts of frustrating vendor delays and even coverups in notifying or correcting the issues — several stating it took weeks, months, and even years to recover from a third-party-related attack. According to one respondent describing their experience following an attack, “It was difficult to determine and attribute” and “very difficult to get the vendor to take responsibility.”
““A third-party data processor was compromised which exposed our data to the attackers. We were notified more than one month after the attack was discovered by the third party.””
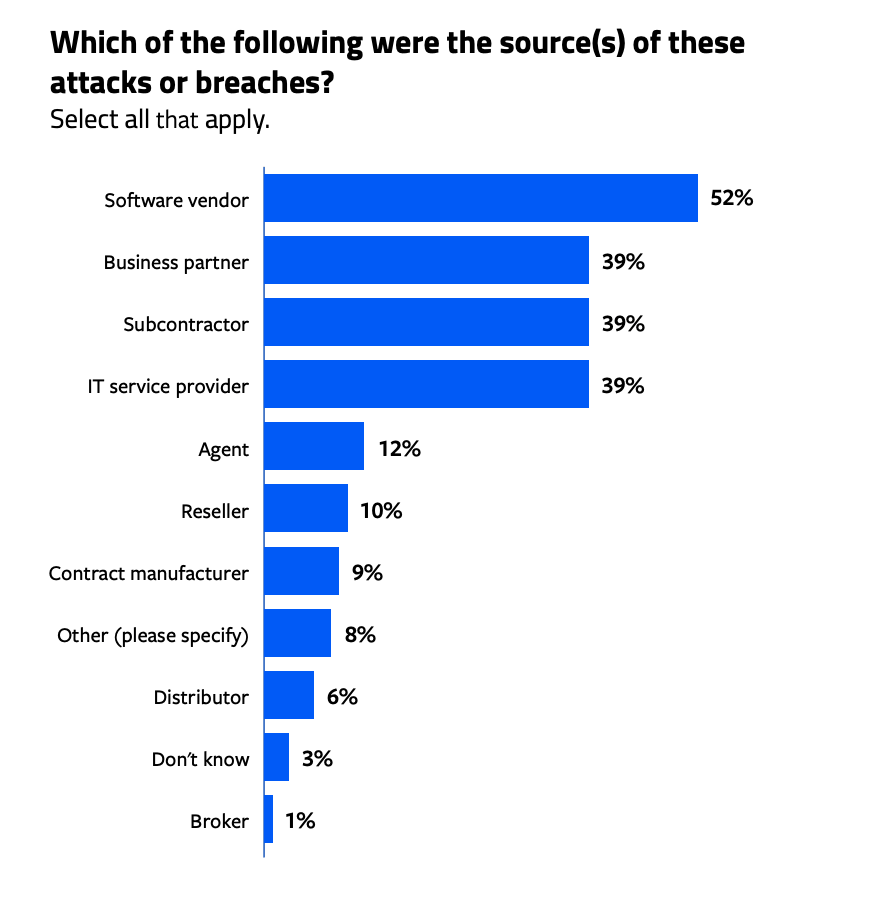
Among those whose organizations were affected, 52% reported the source of their attack was a software vendor. And for at least nearly 4 in 10 respondents (39%), a business partner, subcontractor, or IT service provider was responsible for the incident.
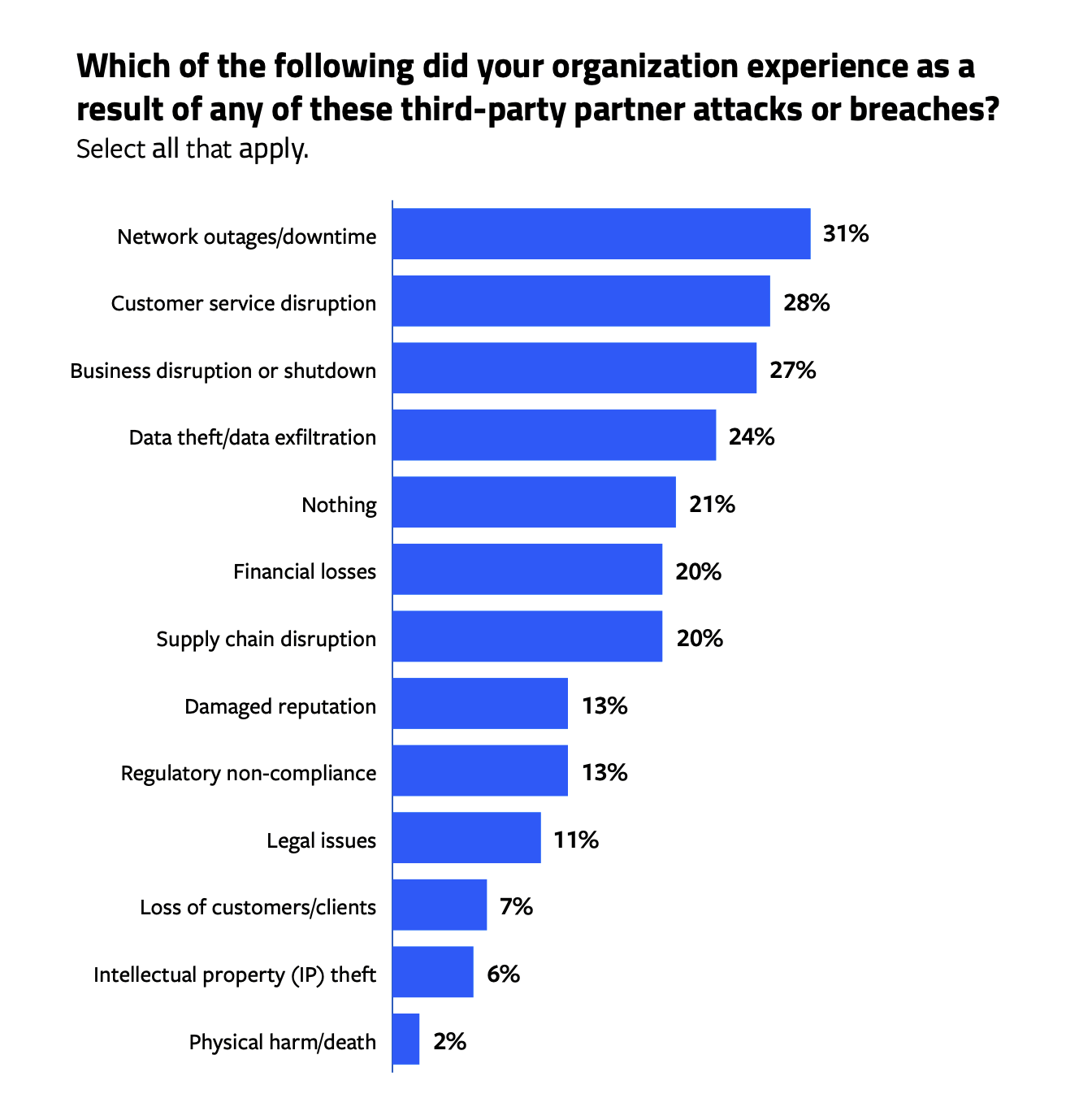
Overall, the consequences for organizations impacted by third-party attacks or breaches were serious, and in some cases, disastrous. About 9 in 10 respondents said they experienced one or more consequences from the attacks related to third parties. The most common were network outages/downtime, reported by 31% and disruption in customer service (28%). Another 27% suffered a business disruption or shutdown, while 24% said their data was stolen/exfiltrated. One in five respondents also reported financial losses or supply chain disruptions. Other impacts included damaged reputation (13%), regulatory non-compliance (13%), and legal issues (11%). Several respondents also reported physical harm/ death as a result of their attack.
““An incorrectly configured AWS bucket was taken over, and customer data was stolen. Customer-facing sites were down, and calls and emails were arriving. A few weeks later, we had sporadic calls coming in from customers who were asking about their orders.””
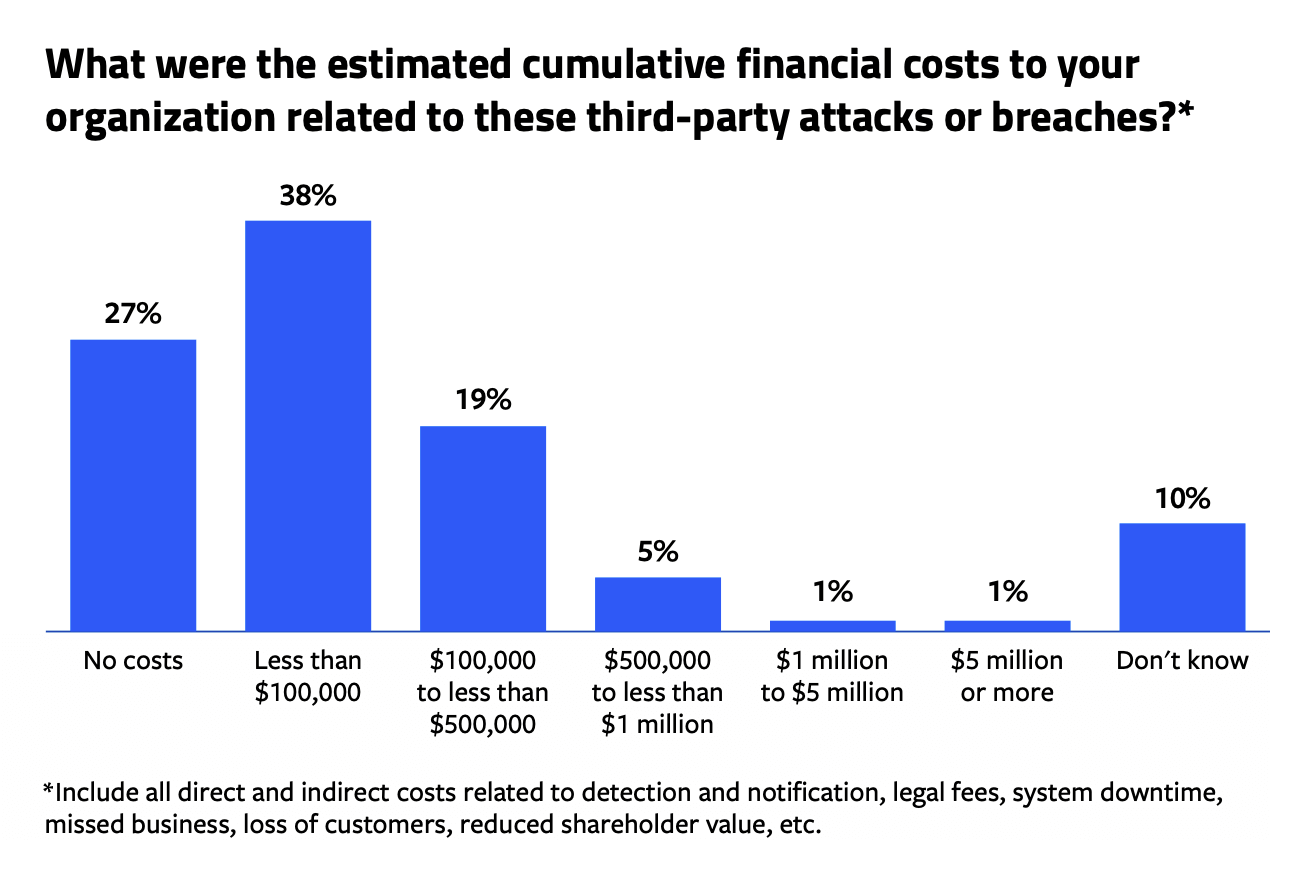
Nearly two out of three respondents (64%) also reported some level of imposed costs and fees associated with their attack/breach. While 38% estimated their cumulative direct and indirect losses and costs — including legal fees, downtime, and loss of customers and business — were less than $100,000, another 26% said these costs exceeded $100,000.
““Partner had ransomware; shut down connections/services for our organization and impacted our supply chain and our patients.””
Large Organizations More Likely to Prioritize Third-Party Risk Management
Compared to 2021, 68% of respondents said that third-party risk management has become either somewhat or much more important at their organization. However, nearly two-thirds (65%) have relegated the priority of managing third-party risk to no more than “moderate” at their organization. While organization size has no effect on the perceived importance of third-party risk management, the priority of these initiatives is highly correlated to the size of an organization. For example, about 6 out of 10 (59%) respondents from large enterprises specified it as either a critical or high priority at their organization whereas smaller organizations are less likely to have this at the top of their priority lists.
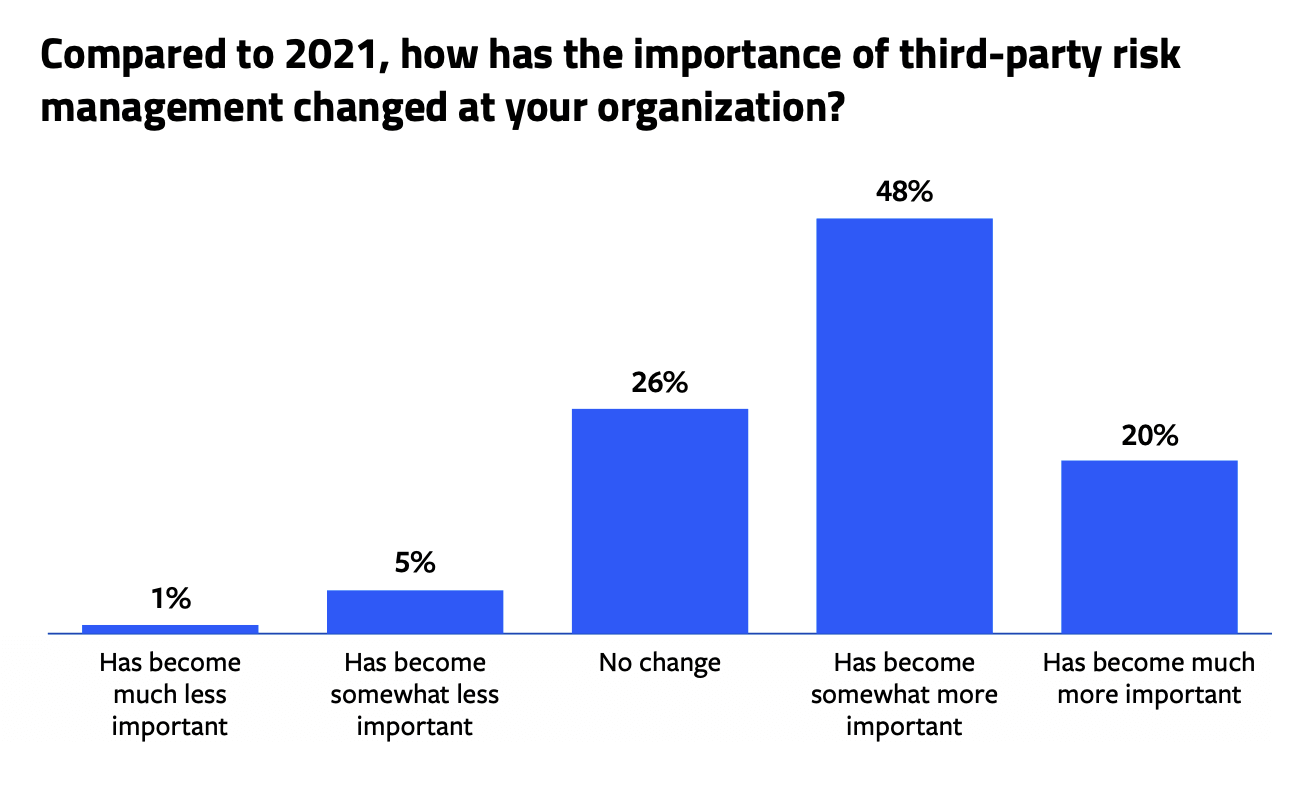
In many cases, respondents attributed the increased importance of third-party risk to their heightened awareness of the issues. In describing the reasons for their deepened attention, many referred to their growing reliance and partnerships with third-party vendors, particularly since the onset of the COVID-19 pandemic and the shift to remote workforces. Their expanded use of diversified applications and programs, SaaS, and other cloud solutions were also factors in their greater focus on third-party risk. Others mentioned the publicity around high-profile, third-party attacks and that publicly disclosed vulnerabilities and breaches had raised their own awareness while also alerting senior management to the potential dire consequences if the vulnerabilities were not proactively addressed.
““We have so many third-party vendors and when data breaches show up on CNN, the C-suite and board perk up and expect something to be done proactively to protect our institution from lapses in security from our third-party vendors.””
Respondents also stressed the increased complexities of their supply chains, while some explained they did not have a full “birds-eye view” into the security of their partners as well as their fourth-party vendors (i.e., their vendors’ vendors), raising serious concerns about their vulnerabilities and the potential damage caused by the “unknowns” in their supply chain.
““We understand that the cybersecurity landscape is continuously evolving and that new threats are emerging on a daily basis. We cannot afford any business disruption from cybersecurity threats, especially if those disruptions were avoidable/ preventable.””
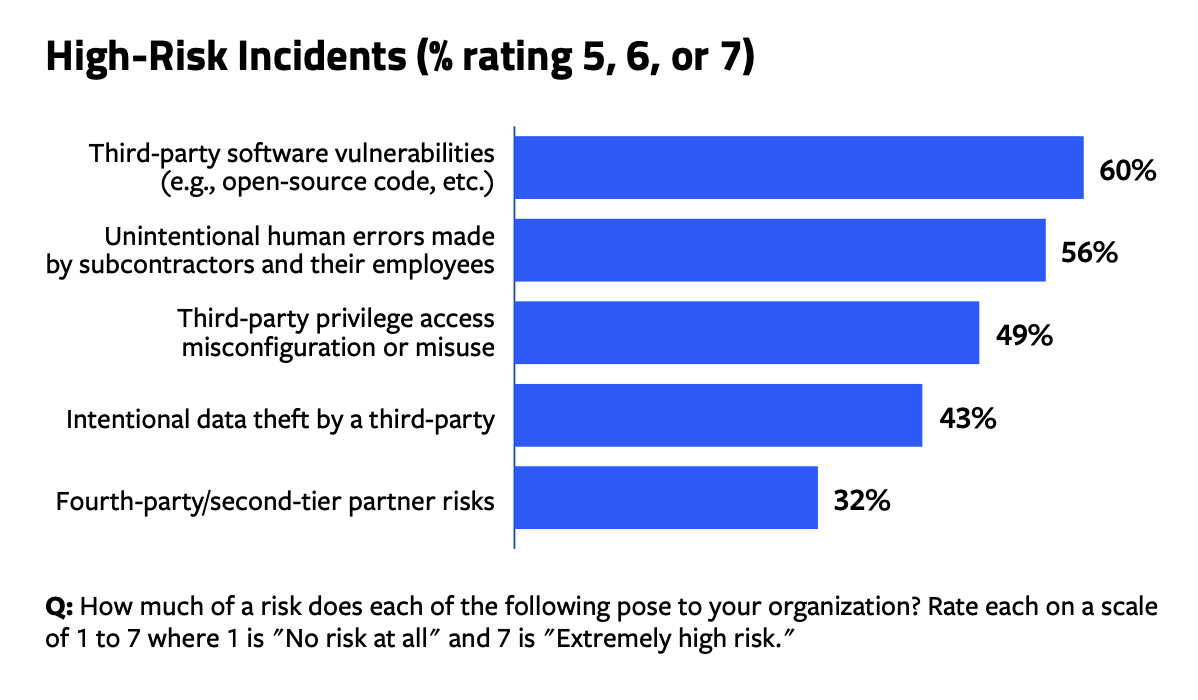
Respondents also commented that their customers, cybersecurity insurance providers, auditors, and/or regulators were putting more pressure on their organization to step up security and management of their vendors and partners. In rating their perception about the risk levels of potential incidents caused by third parties, the largest proportion of respondents (60%) rated third-party software vulnerabilities a 5, 6, or 7 (rating out of 7 in which 7 is the highest risk). Nearly the same number of respondents (56%) provided these ratings for unintentional human errors made by subcontractors and their employees. Also, for almost half of all respondents, third-party privilege access misconfiguration or misuse (49%) as well as intentional data theft by a third party (43%) were considered high risks to their organization. However, less than one-third (32%) believe second-tier partners pose a high risk to their organization.
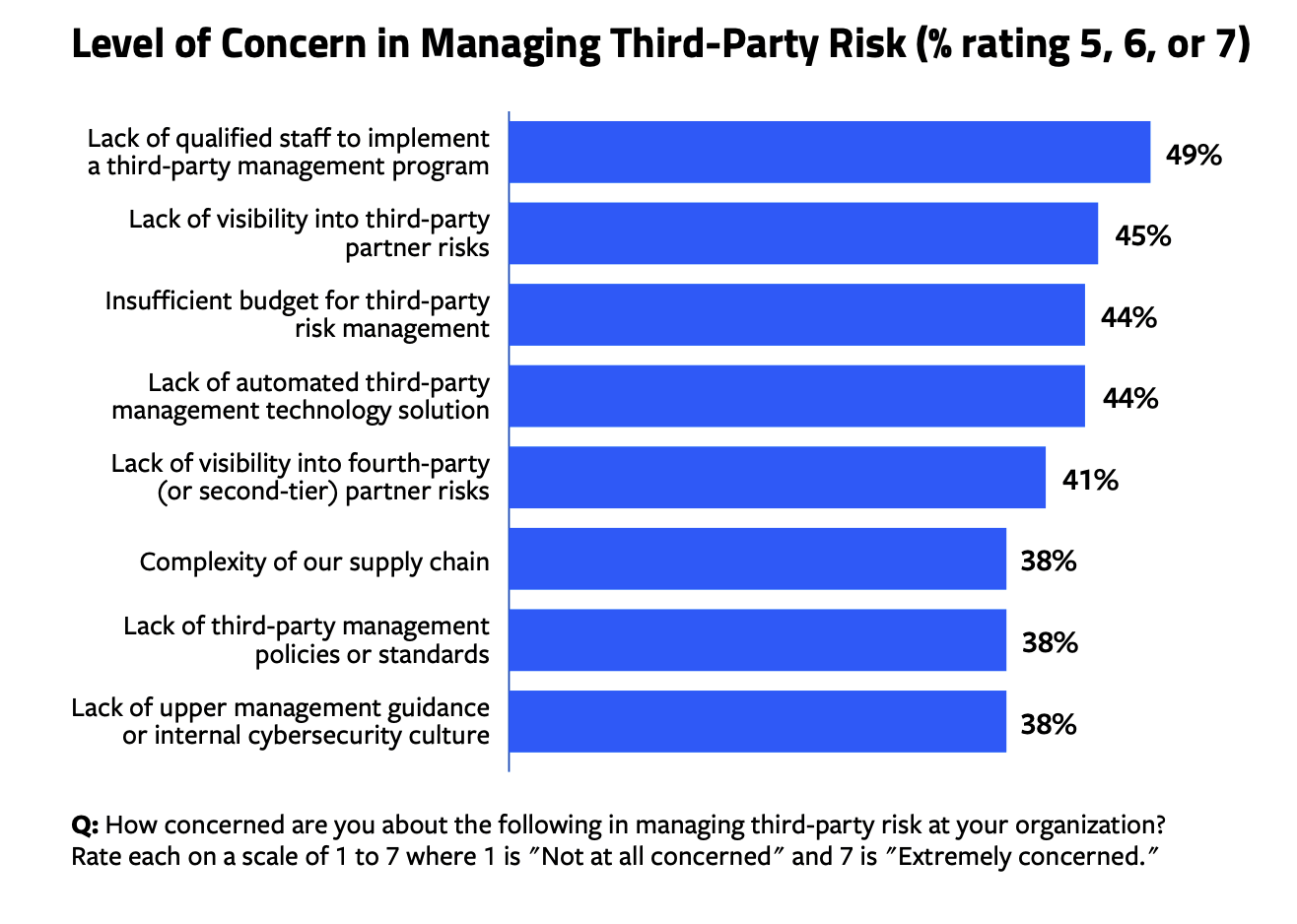
Concerns about managing third-party risks centered around the lack of human resources, budgets, and technology solutions. Nearly half of all respondents (49%) rated the lack of qualified staff to implement a third-party management program as highly concerning (rating this a 5, 6, or 7 out of 7), while the lack of visibility into third-party risks (45%), insufficient budget (44%), and lack of an automated third-party management technology solution (44%) were also similarly rated as highly concerning.
“There is increased reliance on SaaS vendors/services and less visibility into the downstream data processing in these third-party vendors.”
To learn more about how organizations are approaching third-party risk today, download the full CyberRisk Alliance Business Intelligence report, sponsored by AuditBoard: Third-Party Risk: More Third Parties + Limited Supply-Chain Visibility = Big Risks for Organizations.
You may also like to read

What is the Colorado AI Act? A detailed guide to SB 205

What is the EU AI Act?

What is the NIST AI Risk Management Framework?
Discover why industry leaders choose AuditBoard
SCHEDULE A DEMO



